HTB - Blocky

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/blocky/nmap/10.10.10.37-d-scan 10.10.10.37
Nmap scan report for 10.10.10.37
Host is up (0.15s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://blocky.htb
|_http-server-header: Apache/2.4.18 (Ubuntu)
8192/tcp closed sophos
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 21,22,80,8192
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 21 | ftp | ProFTPD | 1.3.5a | |
| 22 | ssh | OpenSSH | 7.2p2 Ubuntu 4ubuntu2.2 | Ubuntu Linux; protocol 2.0 |
| 80 | http | Apache httpd | 2.4.18 | |
| 8192 | sophos |
port 80:
Adding the ip address 10.10.14.37 host url with blocky.htb in /etc/hosts.
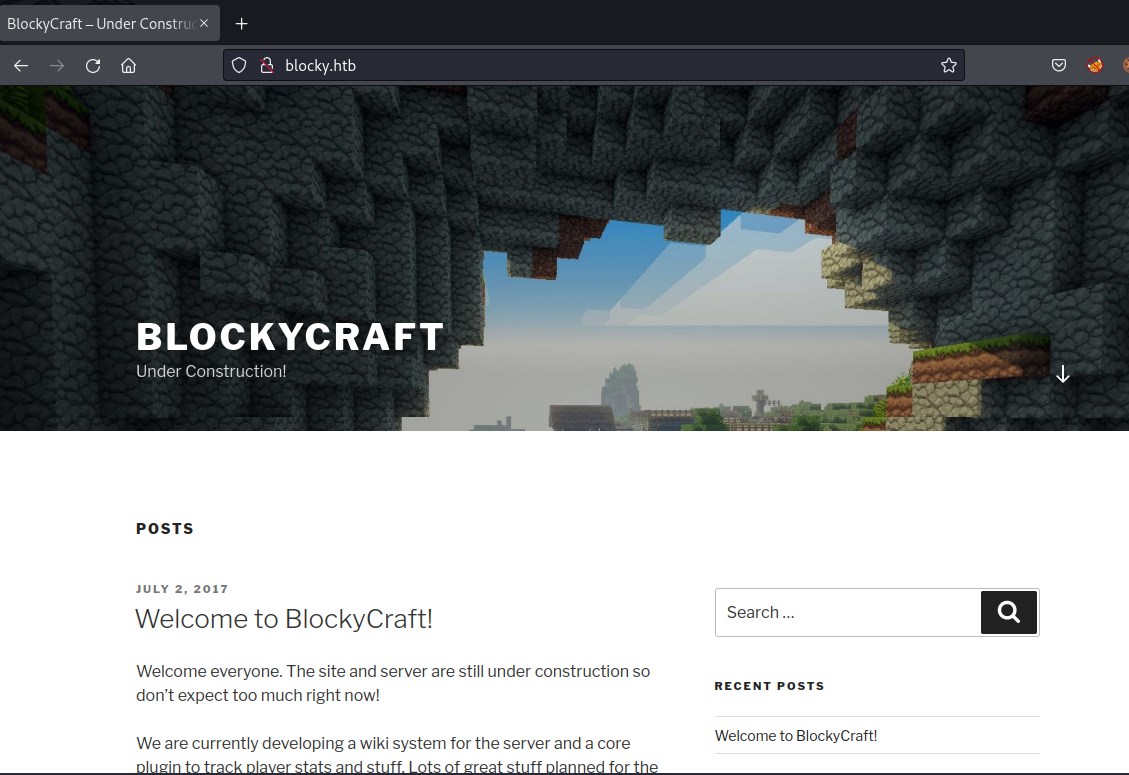
And has wordpress running on the machine. Running wpscan to probe into the machine.
Enumerating users on wordpress environment. There is a user Notch
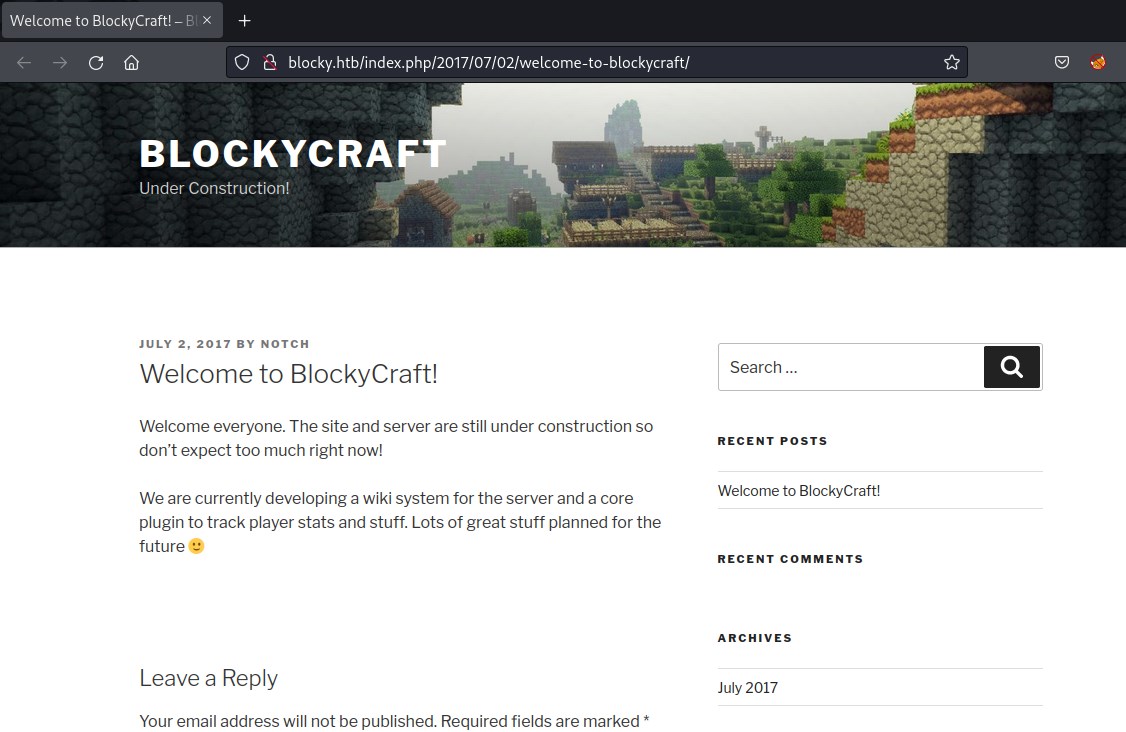
gobuster has detected few files
/index.php (Status: 301) [Size: 0] [--> http://blocky.htb/]
/wiki (Status: 301) [Size: 307] [--> http://blocky.htb/wiki/]
/wp-content (Status: 301) [Size: 313] [--> http://blocky.htb/wp-content/]
/plugins (Status: 301) [Size: 310] [--> http://blocky.htb/plugins/]
/wp-login.php (Status: 200) [Size: 2397]
/license.txt (Status: 200) [Size: 19935]
/wp-includes (Status: 301) [Size: 314] [--> http://blocky.htb/wp-includes/]
/javascript (Status: 301) [Size: 313] [--> http://blocky.htb/javascript/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 311] [--> http://blocky.htb/wp-admin/]
/phpmyadmin (Status: 301) [Size: 313] [--> http://blocky.htb/phpmyadmin/]
/xmlrpc.php (Status: 405) [Size: 42]
/wp-signup.php (Status: 302) [Size: 0] [--> http://blocky.htb/wp-login.php?action=register]
/server-status (Status: 403) [Size: 298]
wiki
phpmyadmin
plugins
Browsing through all the detected url /plugins looks promising.
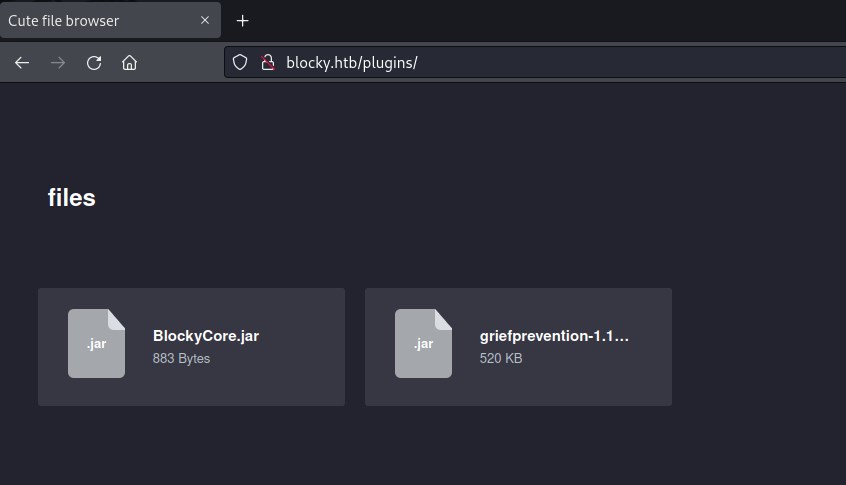
Downloading the BlockyCore.jar and griefprevention-1.11.2-3.1.1.298.jar files.
Open jar file - jadx-gui
Extracting the source from jar file with jadx-gui
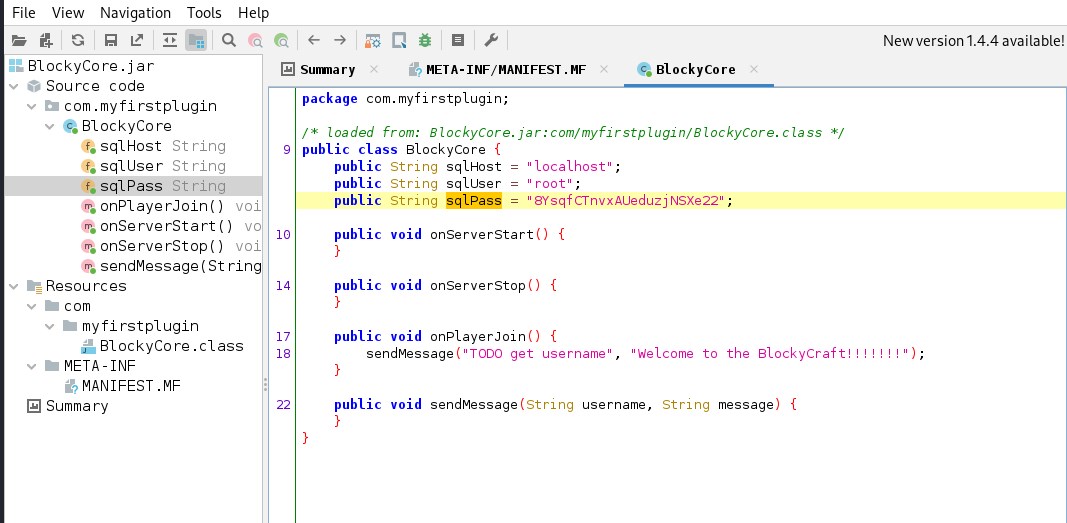
found Creds
Found credentials for sql user in BlockyCore plugin
sqluser = root
sqlpass = 8YsqfCTnvxAUeduzjNSXe22
Lets try connecting to login into phpmyadmin again with these newly found cred's.
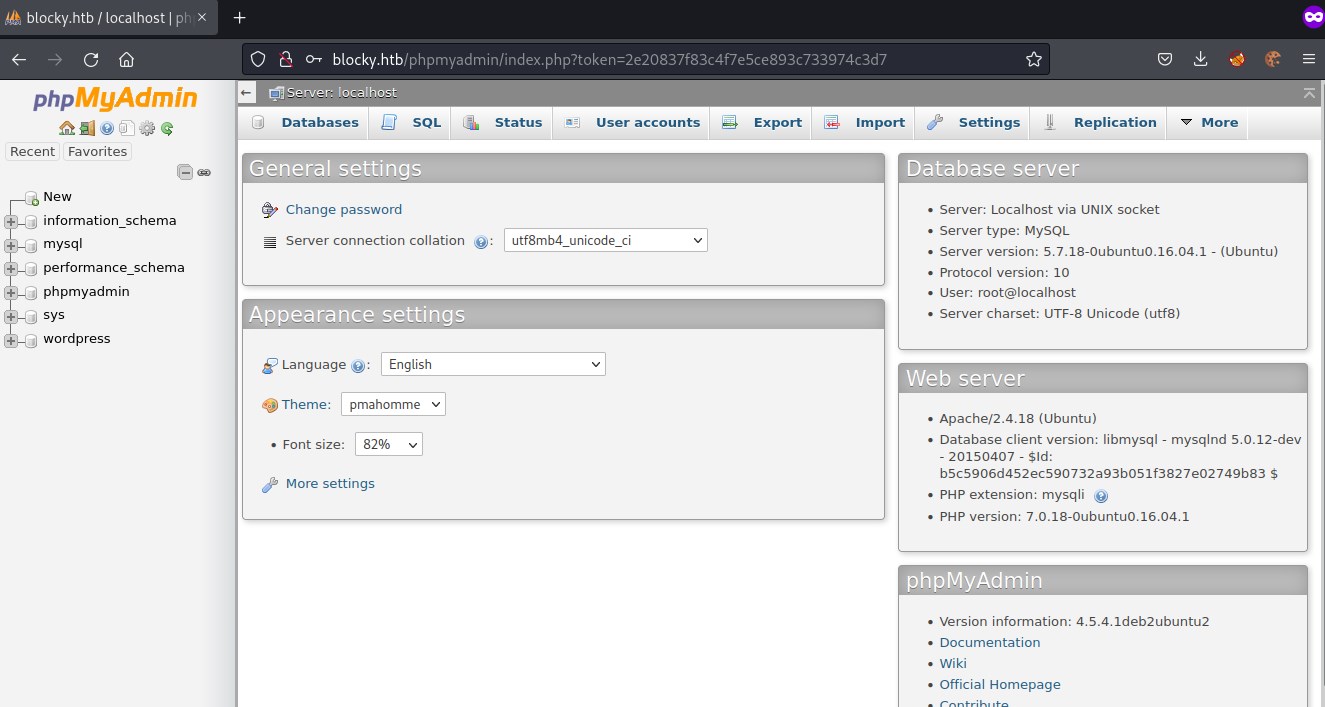
Successfully able to login.
found cred's for wp-user notch in phpmyadmin on wordpress database in wp_users table. querying the table got us the cred's
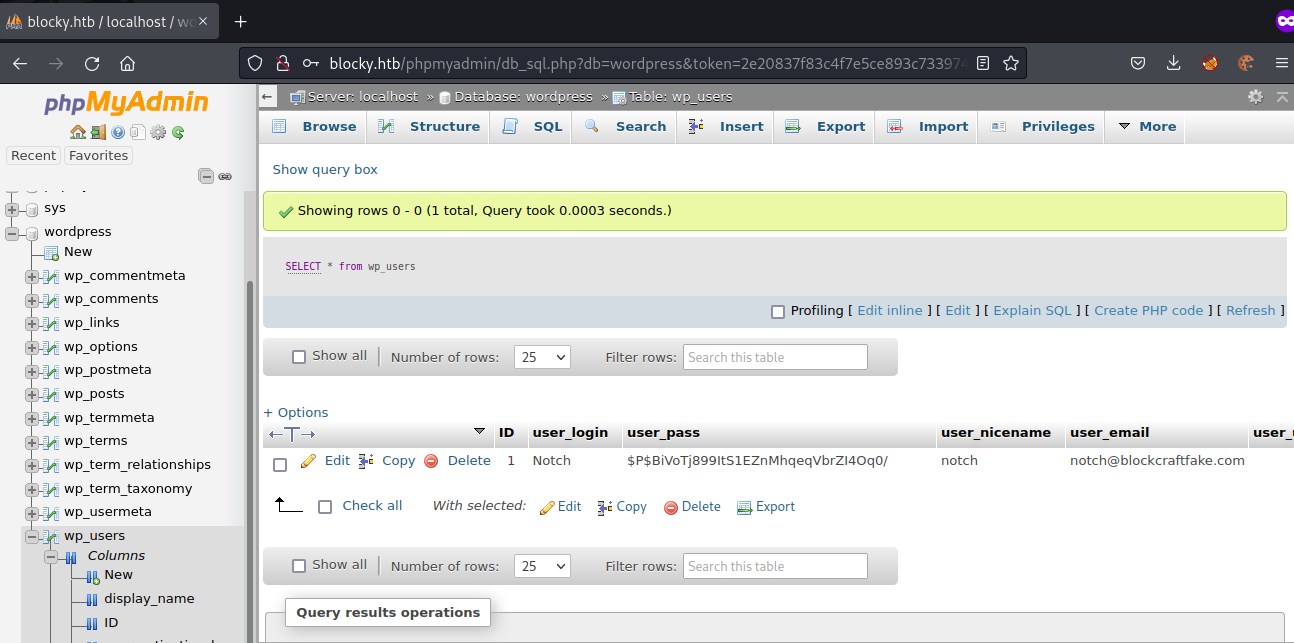
user_login: Notch
password: $P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
user_email: [email protected]
Cracking the wordpress password
hashcat --example-hashes | grep -B12 -A2 '\$P\$'
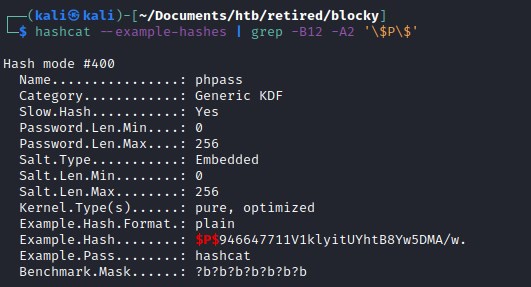
But was not successful in cracking the password.
ssh connection as notch
Now we will use the password from phpmyadmin to the user notch and connect through ssh using the root credentials earlier we found.
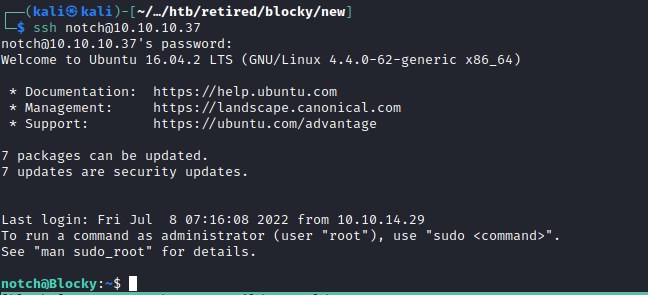
user flag
Privilege escalation
Checking sudo permission.
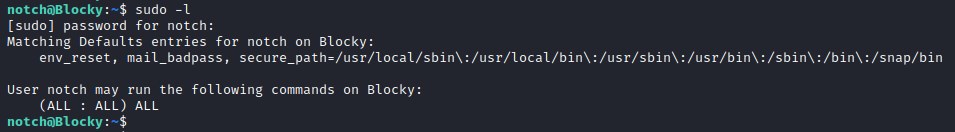
Looks like the user notch can run any command as root user.